Online Customer Accounts Are Vulnerable to Takeover
Cybercriminals exploit every tool at their disposal to steal credentials and hijack online accounts for profit. They impersonate trusted brands through convincing phishing websites, voice phishing (vishing), text-based scams (smishing), and malware delivered across both mobile and desktop platforms.
Once credentials are compromised, threat actors seize control of customer accounts. They carry out fraudulent transactions that can inflict serious financial losses and long-term damage to an organization's reputation.
Proactively Detect Advanced Phishing Attacks
Threat actors are constantly evolving their tactics to evade detection technologies. Developing new blocking techniques enables scammers to keep phishing campaigns active for longer periods of time, increasing the likelihood of their success.
Improving the ability to quickly detect new threat campaigns leads to faster takedown and ultimately less impact. However, successfully bypassing bad actor evasion tactics requires implementing advanced countermeasures.
Fortra Brand Protection leverages advanced anti-evasion techniques to uncover and analyze active threat campaigns. Our experts go beyond surface-level detection, mapping out associated infrastructure and generating high-fidelity, actionable intelligence. This intelligence is continuously fed into our detection systems, enhancing their speed and precision to identify threats earlier and shut down malicious campaigns before they launch or cause damage.
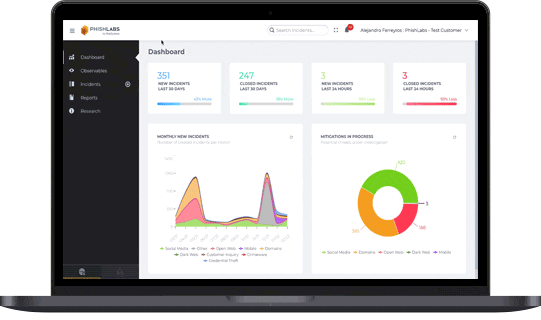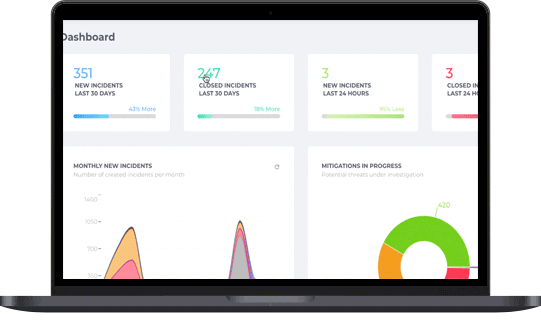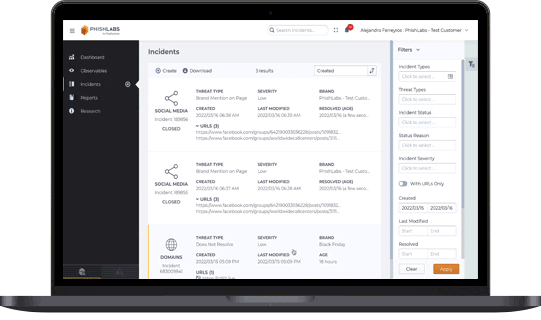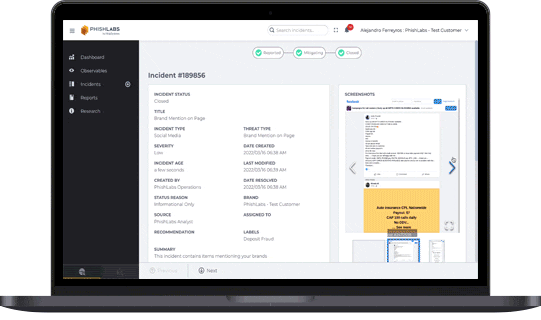
Protect Valuable Online Customer Data
Cybercriminals are skilled at manipulating users into revealing login credentials and sensitive data. Once obtained, they exploit compromised accounts for theft, malware distribution, and launching further attacks.
Early detection is critical. Identifying phishing campaigns before damage is done allows businesses to safeguard customer data and prevent account takeovers. But this level of protection demands broad, proactive visibility across a wide range of online intelligence sources.
Fortra Brand Protection technology consumes and monitors intelligence from a robust set of sources, including over 350 million potential phishing URLs daily from new domain registrations, SSL transparency logs, passive DNS data, active DNS queries, and DMARC failure reports (such as those from Agari by Fortra). With advanced proactive detection, the largest phishing dataset, and world-class expertise, our ability to accurately detect phishing campaigns that lead to account takeover attacks is unparalleled.
Prevent, Detect, and Disrupt Account Takeover Fraud

Learn how Fortra’s Customer Phishing Protection Bundle integrates best-of-breed solutions from Agari and PhishLabs to prevent domain spoofing, detect more phishing campaigns resulting in account takeover, and mitigate the infrastructure threat actors rely on to initiate attacks.
Unrivaled Takedown at Enterprise Scale
Paired with early detection, the disruption of phishing campaign infrastructures and the rapid takedown of credential theft phishing sites significantly reduces the risk of account compromise. However, contacting hosting providers, ISPs, and registrars to report abuse can be time-consuming as procedures for handling takedown requests vary widely. Partnering with PhishLabs gives your organization access to an extensive global network of provider relationships, extending your ability to quickly mitigate attacks.
Additionally, fraud actors are increasingly using sophisticated automation to multiply the number of lures they distribute and improve their chances of success. Effective takedown of attack infrastructures and malicious sites requires streamlined reporting processes, trusted relationships, and automated integrations.
Yet businesses still face volumes too high to manage effectively, leading to prolonged exposure and elevated risk. With direct access to automated killswitches and preferred escalation integrations, PhishLabs’ customers enjoy unrivaled threat takedown at enterprise scale.