Expose the Data Leak, Not Your Brand
Stolen credentials remain one of the primary entry points for threat actors. Today’s security teams must safeguard massive volumes of internal data while contending with limited visibility across expansive digital ecosystems, including obscure corners of the internet where attackers thrive.
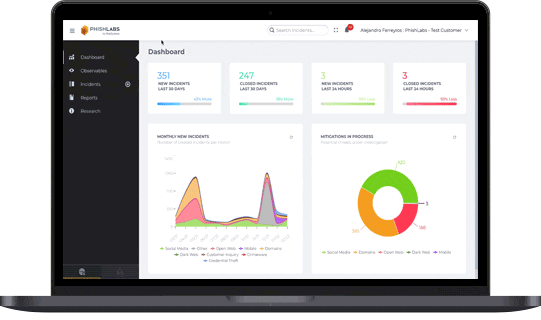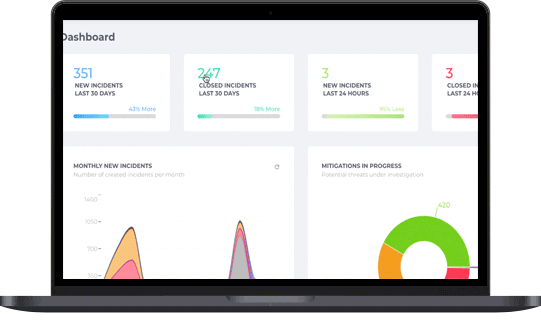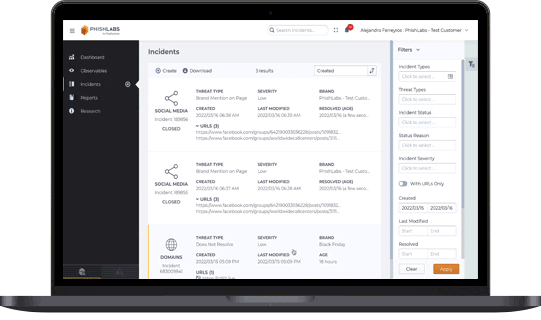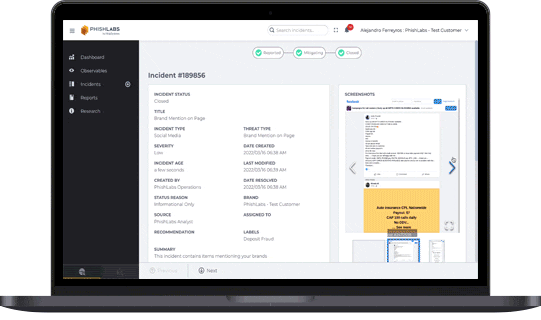
Fortra Brand Protection gives enterprises 24/7 visibility across digital channels, enabling proactive data leak detection, continuous monitoring of stolen credentials circulating among threat actors and malware, and rapid takedown of exposed data on the open web and social media.
Web: Continuous data collection from the surface web, deep web, dark web, and mobile app stores
Code Repositories: Data monitoring of widely used code-sharing platforms, paste sites, and underground marketplaces
Automation: Unparalleled breadth of automated data collection combined with expert mining methods
Client-specific: Targeted collection according to client's business needs
Monitoring: Proactively guard against attacks with broad visibility into actionable stolen credentials uncovered from the dark web and harvested through malware
Accelerate Data Leak Mitigation
Data leaks can be catastrophic — not just financially, but also in terms of reputation and operational disruption. Once sensitive information is compromised, organizations often struggle to pinpoint when the breach occurred, where the data has ended up, and how it’s being distributed or sold. The lack of visibility makes remediation even more difficult. In many cases, businesses don’t even know where to begin looking.
Fortra Brand Protection helps mitigate the impact of data leaks by swiftly removing actionable threats from the open web and social media, automatically, with no client review required. When credentials are compromised, we provide clear visibility into what was stolen, empowering your team to take immediate steps like locking accounts or enforcing password resets to prevent further damage.
Focus Your Response on Verified Leaks
The sheer volume of web activity creates excessive noise — false positives, irrelevant data, and benign chatter — that slows down security teams as they search for real threats.
Fortra Brand Protection filters out the noise with verified, human-vetted intelligence tailored to your organization. Our experts assess each finding in context — evaluating threat severity, data exposure, visibility, status, and related activity — to determine whether it's informational or actionable. This targeted approach enables security teams to focus on real threats, respond faster, and reduce potential impact.
Fortra Data Protection: Additional Solutions
Looking for broader protection for your critical data and IP? Fortra delivers market-leading data security solutions that seamlessly complement our data leak detection solutions. Our integrated offerings — including data loss prevention, data classification, and secure collaboration — safeguard sensitive data while enabling users to stay productive and compliant.