Protect Your Organization with Domain Monitoring
Threat actors frequently exploit malicious domains to launch a variety of online attacks. With domain registration being inexpensive, quick, and widely accessible, virtually anyone can create fraudulent websites to steal login credentials, redirect web traffic, or sell counterfeit goods.
Scammers also impersonate trusted brands using spoofed domains to send phishing emails, execute business email compromise (BEC) schemes, and lure victims into ransomware attacks. Defend your organization against these domain-based threats with best-in-class domain monitoring.
Gain Comprehensive Visibility into Domain Threats
Every year, cybercriminals register hundreds of thousands of look-alike domains to try to fool users. The ultimate goal of domain spoofing is to prompt interaction with a malicious email or have the user perform an ulterior motive like visiting a phishing site so the threat actor can steal personal information (PII). By detecting threat actors targeting your brand, you can protect against a variety of online threats.
However, detecting abuse requires visibility into new and existing domain registrations and the ability to mine those registrations for brand-related keywords and variations. Fortra Brand Protection’s domain monitoring solution continuously analyzes SSL certificate logs, passive DNS data, and DNS zone files to identify every active domain across more than 2,000 top-level domains (TLDs), including both generic (gTLDs) and country-code (ccTLDs) TLDs.
We also leverage multiple active DNS sourcing methods to proactively gather large volumes of domain data. This approach delivers broad visibility into the domain threat landscape, accelerates threat detection, and enhances the identification of various risks compared to traditional methods.

Reduce the Noise So You Can Focus on Threats

Intelligence tools built to monitor new and existing domains for brand matches and variations can generate large volumes of false positives. Sorting through endless domain names can get in the way of detecting threats, yet security teams must sift through this noise to single out malicious domains that pose material risk to their organizations.
Eliminate the headache of searching for look-alike domains. Our digital domain monitoring solution combines advanced automated analysis and expert vetting of domain variations. This removes false positives from the haystack, allowing your team to focus on verified threats targeting your organization.
How to Defend Against Look-Alikes

This playbook outlines the domain threat landscape, common methods of domain abuse, techniques for detecting malicious activity, and the steps required to mitigate domain threats. By following its guidance, security professionals can reduce the risk that domain spoofing and related threats pose to their organizations.
Streamline the Takedown of Malicious Domains
The only method of fully mitigating the risk posed by a malicious domain is to take it offline. Our service facilitates domain takedown by working directly with the domain registrar.
The domain takedown process can prove to be highly complex and time-consuming depending on the type of threat and the registrar involved. Entities requesting domain takedown must provide detailed evidence of abuse, and ultimately it is up to the registrar to determine if the offending domain should be removed.
Fortra Brand Protection's domain monitoring service gathers the evidence needed and gets malicious domains taken offline quickly. We know what types of abuse qualify for takedown and what evidence each registrar requires.
Having cultivated an extensive network of trusted registrar partners, our customers benefit with access to automated killswitches, preferred escalation procedures, the highest success rate, and the fastest speed of malicious takedown in the industry.

Reduce Your Security Team's Burden and Workload

Security teams are often left to shoulder the responsibility of identifying and mitigating domain threats. This typically involves constant tuning of data collection parameters, reviewing large volumes of potential threats, and managing the mitigation process for those they can confirm.
Fortra Brand Protection’s Domain Monitoring service lifts that burden by handling the entire threat detection and mitigation process as an extension of your security team. We manage it all without adding to your operational workload — one of the key reasons why some of the world’s most targeted organizations trust us to protect their brands from digital threats.
Augment Domain Monitoring
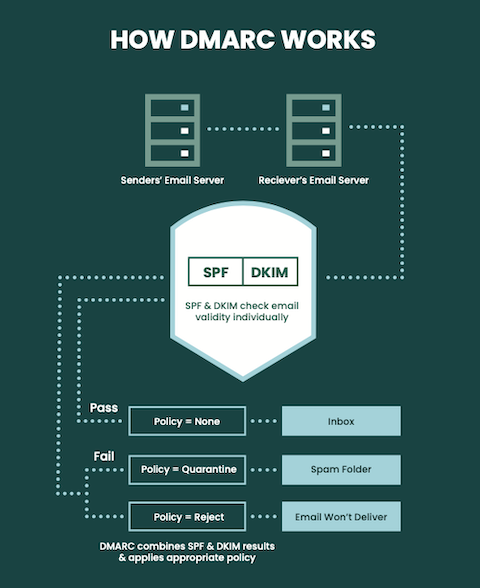
Fortra DMARC Protection combined with our Domain Monitoring solution can provide organizations with comprehensive domain protection.
This is because Fortra DMARC Protection stops phishing by automating the process of DMARC email authentication and prevents look-alike domain attacks by continuously monitoring your ecosystem, even as cybercriminals switch to other attack types to circumvent filters and legacy email security controls.
Fortra DMARC Protection has been proven to deliver a higher rate of enforcement than any other vendor and has helped more organizations realize business value by bringing their domains to a DMARC policy of reject.
The solution also includes email cloud intelligence, which automatically identifies, monitors, and manages emails being sent on your behalf by third-party email senders. This enables businesses to easily identify and authorize legitimate email communications, block malicious emails from cybercriminals, and protect consumers and partners from email attacks.
Domain Monitoring Features
Defends Against Common Threats
- Look-alike domains
- Fake websites
- Brand impersonation
- Website traffic redirection
- Credential theft phishing
Collection Methods
- New domain registrations
- Historical domain registration
- SSL certificate registrations
Analysis and Intelligence
Domain analysis includes the capture and review of the following information when available:
- Screenshots
- Threat URLs
- MX records
- WHOIS data
Threat Mitigation
Fortra Brand Protection automatically pursues mitigation of confirmed malicious domains and will notify you of potential unauthorized domains for review.
Domain Monitoring
Fortra Brand Protection monitors confirmed malicious or unauthorized domains for changes and provides notifications if material changes are detected.
PhishLabs made the entire process–from procurement to deployment and ongoing monitoring–SIMPLE. The portal UI makes monitoring easy for potential abuse cases requiring the organization’s attention. I have full confidence in the level of protection obtained as a result of the service from PhishLabs.
Gartner Peer Insights