Whaling phishing attacks specifically target C-suite executives, putting highly sensitive, mission-critical data at serious risk. These sophisticated scams often involve cybercriminals impersonating executives to deceive employees into revealing confidential information or executing fraudulent transactions. Because they focus on high-value individuals and assets, these attacks pose a significant threat, but with the right safeguards in place, organizations can defend against them.
Understanding Phishing: The Basics
Phishing is a form of cyber deception where attackers impersonate trusted individuals or brands—typically through email or text—to trick recipients into revealing sensitive information or installing malware. These attacks have surged in recent years, making them one of the most pervasive threats to network security.
In whaling attacks, cybercriminals go a step further by impersonating executives or senior leaders within an organization, exploiting trust to gain access to confidential data or prompt fraudulent actions.
To evade detection, attackers use a range of techniques to mask their true identity, including:
- Sending emails from a spoofed domain
- Sending emails from a lookalike domain
- Using stolen brand images in the email to convey trust
- Using stolen email signatures to look legitimate
- Hiding malicious embedded links inside innocent looking URLs
- Using scare tactics and urgency to get recipients to act
- Pretending to be a key figure within an organization to get recipients to act
While there are numerous methods attackers use to phish unsuspecting victims, there are equally just as many strategies organizations can use to implement phishing defenses. Let’s take a look at the different types of phishing attacks, and how they compare to whaling.
When Cybercriminals Go After the Big Fish
Whaling is a highly targeted form of spear phishing that preys on trust by impersonating senior executives within a company. Unlike broad phishing attacks that are sent to thousands of recipients at once, whaling is precise, calculated, and designed to deceive specific individuals — usually employees with access to sensitive data or financial controls.
Attackers often pose as a CEO or CFO, leveraging their perceived authority to pressure employees into taking urgent actions, such as sharing financial records, clicking malicious links, or wiring funds to fraudulent accounts.
What sets whaling apart is the level of research behind it. Cybercriminals often use publicly available or stolen data, such as names, titles, email addresses, and internal terminology, to craft convincing messages that mimic legitimate communications. The result is a scam that feels authentic and is far more likely to succeed.
When the Boss Isn’t Really the Boss: Whaling Email Examples
What does a whaling campaign look like? Let's run a mock scenario:
- After weeks of reconnaissance, attackers have gathered detailed information on ABC Company and are ready to launch their whaling campaign. Armed with the names and email addresses of key C-level executives, they craft a convincing message designed to trick the recipient into opening an attachment, one that quietly installs spyware behind the scenes.
- This spyware steals company secrets, financial information, and even assets that will aid in future whaling campaigns.
- Attackers have registered a fake domain that looks exactly like ABC Company — for example, instead of the real abccompany.com, they create abcconpany.com, a misspelling that is tough to spot.
- The attackers then spoof the CEO’s email address and send a message to the company’s accountant, claiming an invoice is overdue and requires immediate payment.
- The attachment appears to be a legitimate PDF invoice, but it’s actually a malicious payload that installs malware when opened. To make matters worse, the payment details in the fake invoice are tied to the attacker’s account, so the victim not only compromises their system but also unknowingly transfers funds directly to the attacker.
Whaling like the above example can have a devastating impact on organizations of all sizes, as the attack focuses on stealing the most sensitive forms or confidential personal data and financial information, such as tax returns and bank account numbers. This can lead to fraudulent wire transfers, stolen identities, and even more coordinated follow-up attacks.
Whaling Emails: The Red Flags to Watch For
- "I need a personal favor ..." — This type of message ingratiates the recipient to the sender so that they are inclined to think, "Wow, the CEO is asking me directly to help him/her out!" and as a result, they act on it quickly.
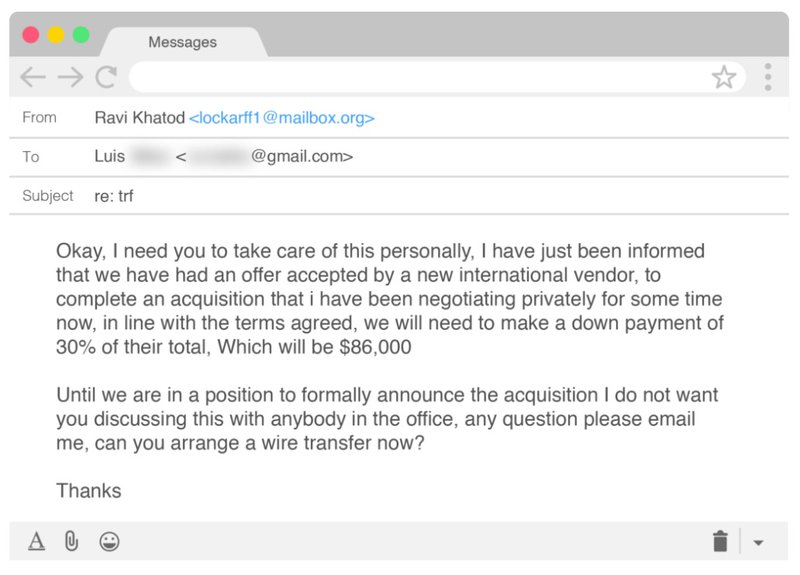
- "I can't take calls right now ..." or "I'm really busy ..." — This discourages the recipient from calling the sender and pushes them to reply to the email without questioning first.
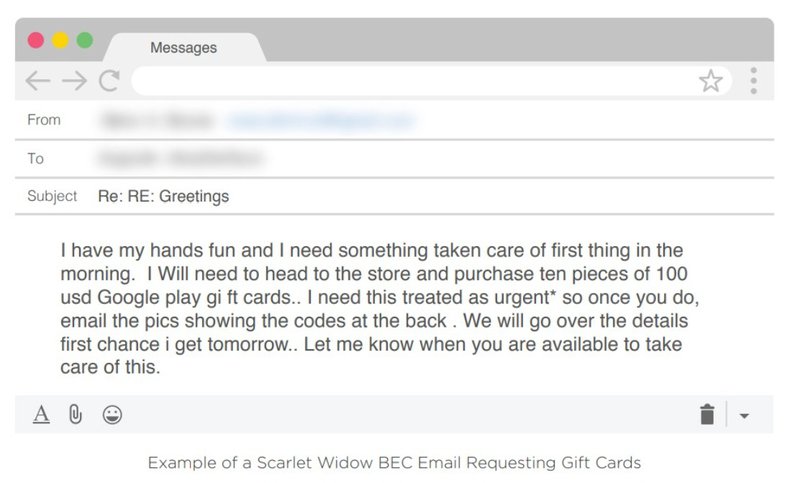
- "Here's an overdue invoice that needs to be paid immediately!" — This demands the recipient expedites the sending of payment for an outstanding invoice, most commonly via wire transfer.
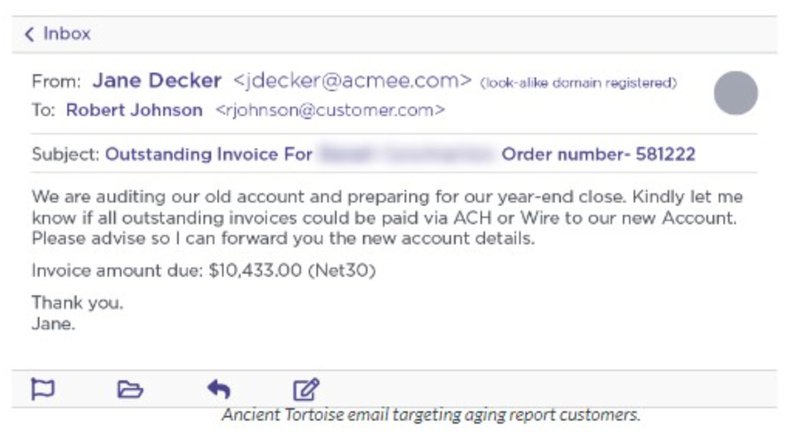
- Emails with links embedded asking the recipient to open/view a document and often require logging in with their credentials.
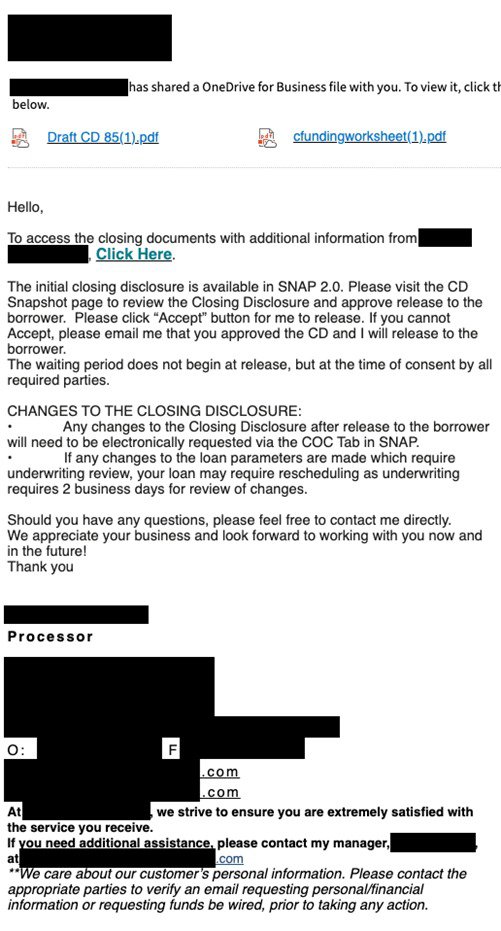
Defending Your Business Against Whaling Scams
Preventing phishing, or more specifically whaling, is never as simple as installing a program. It takes a dedicated phishing response plan in order to remain protective and minimize the impacts of phishing attacks. Here are a few steps you can take to prevent whaling:
- Implement email rules that tag external emails as “outside of the organization.” This helps users know right away when an email is coming from outside the company. This capability is often part of a larger data loss prevention (DLP) solution.
- Create policies and procedures for sensitive tasks such as wire transfers or sending financial information. Having someone approve these requests or use a secondary channel helps catch phishing attempts in action before it’s too late.
- Implement phishing training across your organization. Staff training uses a combination of fake phishing emails along with customized training to measure how knowledgeable staff members are in email security.
- Invest in professional defense. There are a lot of moving parts when it comes to defending against whaling attacks. Companies can partner with organizations like Fortra to build a phishing defense plan that prevents these attacks from ever making it to the inbox.
Email phishing
In contrast, email phishing is the most widespread type of scam and is what most people mean when they say “phishing.” It’s estimated that nearly half of all emails sent contain some form of phishing attempt. These messages often impersonate trusted companies or business contacts, using tactics like fake password reset requests, fraudulent invoices, and bogus shipping notifications to deceive recipients. Learn more about email phishing tactics >
Spear phishing
While similar to whaling, spear phishing targets a specific organization by leveraging detailed online research to impersonate trusted companies or individuals the target frequently interacts with. Attackers may pose as a reliable third party or an insider within the company. These highly tailored attacks focus on individual departments or employees, with every detail from the subject line to the sender’s name, crafted to appear familiar and credible. Unlike broad email phishing that casts a wide net, spear phishing aims with precision, using a single spear to catch one valuable target. Learn more about spear phishing >
SMiShing
SMiShing is an attack that uses text messaging (SMS) in order to deliver a harmful message. These can be either targeted attacks or widespread phishing campaigns that attempt to trick users into clicking fake links and entering their information. The most common forms of SMiShing are fake shipping updates, customer rewards, and, especially recently, messages impersonating the IRS regarding stimulus check updates. SMiShing and vishing (also referred to as Hybrid Vishing) have gained traction over the last few years. Learn more about sMiShing >
Vishing
Vishing involves attackers using voice communications to steal information. Commonly, victims receive voicemail messages claiming they owe money, have been hacked, or face legal issues with agencies like the IRS. The goal, as with all scams, is to illegally obtain sensitive information or funds.
Vishing can also occur when users call fake phone numbers prompted by malicious websites. These sites display alarming pop-ups claiming the user’s computer is hacked and urge them to call a “tech support” number. In reality, there’s no issue. But once contacted, the scammer may gain remote access to infect the machine or charge for fake repairs.
Hybrid vishing attacks combine email and phone tactics, embedding fraudulent phone numbers in emails with urgent language designed to trick victims into calling and sharing sensitive information with impostors. Learn more about vishing >
The Fortra Advantage
Fortra delivers a comprehensive, turnkey solution to stop whaling attacks with automatic phishing detection, response, remediation, and containment. By combining signature-based defenses with advanced behavioral analysis, our system effectively blocks malicious files and neutralizes threats in real time.
Want to safeguard your business from whaling scams? Discover how Fortra’s Phishing Response can protect your organization with proactive, intelligent security.