In Q2, four out of five phishing sites were staged using infrastructure that required no investment on the part of threat actors, including Compromised Sites and Free Tools and Services, according to the Agari & PhishLabs Quarterly Threat Trends & Intelligence Report. Although the volume of Paid Domain Registrations associated with phishing sites grew slightly, threat actors continue to choose no-cost methods when building malicious websites.
Every quarter, Agari and PhishLabs analyze hundreds of thousands of phishing and social media attacks targeting enterprises, their brands, and their employees. In this post, we analyze phishing activity targeting organizations, their brands, and customers.
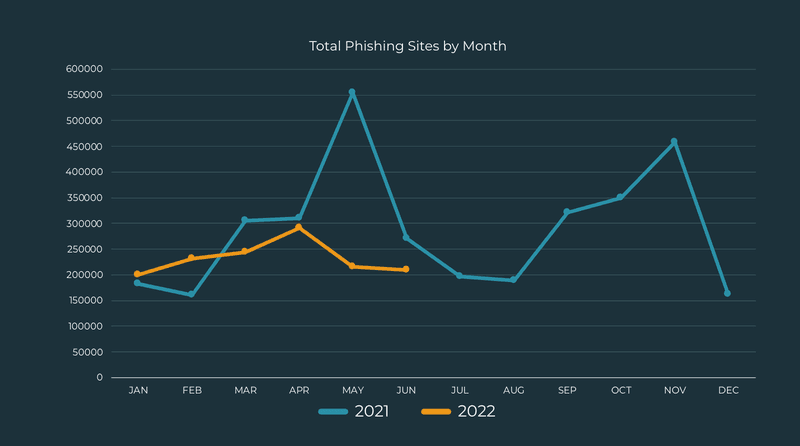
Phishing volume climbed in Q2, with observed phishing activity increasing nearly 6% over Q1. Month-to-month volume trended down from April to June and generally lacked the erratic activity that characterized much of 2021.
Top Industries Targeted
Financial Institutions experienced the greatest number of phishing attacks in Q2, representing 42% of share of total volume. This is a decrease of nearly 12% over Q1, and the second consecutive quarter incidents targeting the industry have declined. Finance is historically the top targeted industry.
Telecommunications businesses were targeted 23% of the time, after jumping nearly 9% in share from Q1. This was the largest increase among top targeted industries and pushed Telecoms to the second most targeted spot within the group.
Social Media was the only industry other than Finance to experience a decrease in attacks in Q2, accounting for 21% of share of incidents. Other targeted industries in the technology sector include Webmail (7.9%), Ecommerce (3%), and Cloud Storage/Hosting (2.5%). Combined, the four industries made up 34.4% of Q2 credential theft phishing incidents.
Methods of Staging Phishing Sites
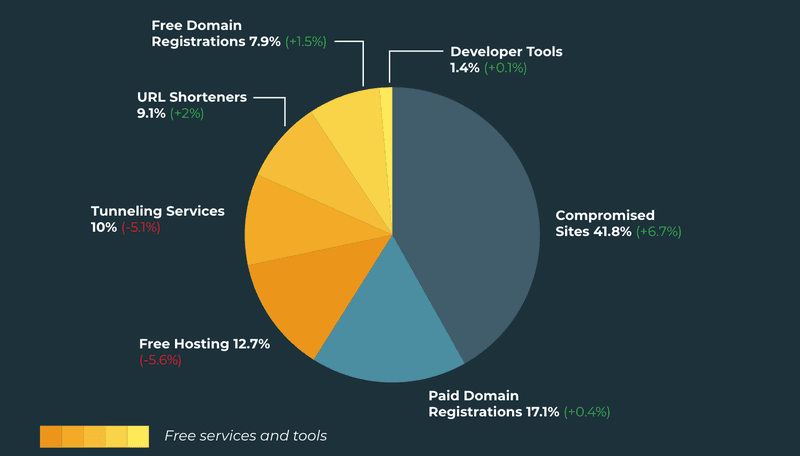
The majority of bad actors used no-cost infrastructures to stage phishing sites in Q2. These methods, including Compromised Sites or Free Tool and Services, made up nearly 83% of observed phishing volume.
Compromised websites were the top method of staging phish in Q2, reaching nearly 42% of overall share. This is a 6.7% increase over Q1 and the greatest growth in activity among the categories. Paid Domain Registrations also increased, representing 17.1% of phishing sites.
Free Hosting accounted for 12.7% of abuse within the group despite experiencing a decline of 5.6%. Use of Tunneling Services also decreased yet represented 10% of overall share of activity. The drop-in activity for both Free Hosting and Tunneling Services suggests providers are putting security measures in place to deter abuse.
URL Shorteners (9.1%), Free Domain Registrations (7.9%), and Developer Tools (1.4%) rounded out the top five free services, each experiencing a nominal increase.
Top-Level Domain Abuse
In Q2, Legacy Generic Top-Level Domains (gTLDs) .COM, .ORG, and .NET were used to stage nearly 60% of observed phishing sites. This is despite a combined 6.4% decrease in abuse from Q1. Legacy gTLD .COM represented the majority of staging volume, contributing to 46.9% of share.
Country Code Top-Level Domains (ccTLDs) accounted for 32.9% of Top-Level Domains, doubling Q1 volume. The majority of ccTLD volume was primarily made up of abuse by .CV, which also happened to be the second most abused TLD during Q2. Nearly 9% of phishing sites were staged using .CV.
New Generic Top-Level Domains were abused less in Q2, making up 7.5% of overall share. New gTLD .XYZ was the only representative within the top ten.
Phishing remains the top online threat to enterprises. While phishing in Q2 grew nearly 6%, increases in attack volume during the first half of 2022 have been steady and lacking the high-volume campaign activity representative of 2021. In order to protect against phishing threats targeting your organization, security teams should invest in the proactive detection of suspicious online activity involving their
