One often overlooked but valuable clue in social media threat investigations is the threat actor’s username. While it may seem trivial at first glance, usernames can carry personal significance, hinting at patterns, affiliations, or behaviors that help expand an investigation across platforms.
As we discussed in our previous OSINT post, mapping all known social media accounts to a single user is a foundational step in assessing risk. That process often begins with a close analysis of the username. In this article, we’ll explore why usernames are worth investigating and how they can unlock new, actionable paths in your research.
First Steps
Depending on the platform, the username which appears on the actor’s account can lead to other monikers you can explore that could act as investigational pivots. Questions security teams should consider include:
- Is there indication of an interest toward a niche hobby?
- Do the numbers within the username resemble a date?
- What could be the significance of this date?
- Is the username inclusive of their real name or a variant of it?
Security teams should also confirm the username displayed is the threat actor’s chosen name. Some social networks do not display a chosen username within the profile, but rather within the URL of the account. For example, we may see the username “PhishLabs” on the account’s page, but within the URL it may show www.examplesocialnetwork.com/PhishL0308. This opens the door to a pivot that should be scrutinized.
Usernames are often shared by the same individuals across different platforms as an identifier. By finding links to other social profiles within newly discovered accounts, security teams can create paths of investigation. Cross-referencing a username works best with unique names, and this will help you begin linking the usernames and their significance to one threat actor.
Username Background
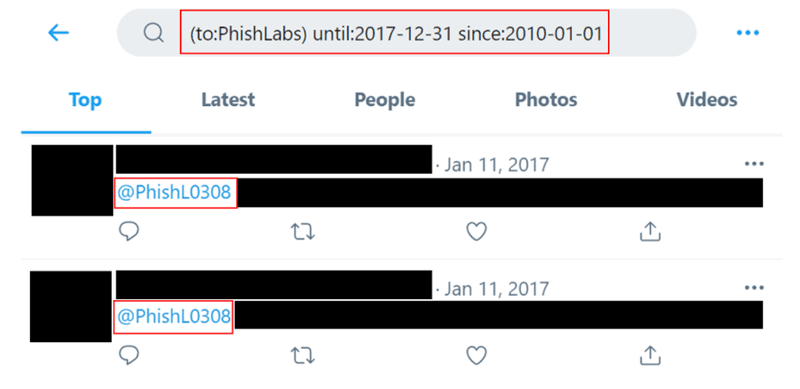
It is also important to explore any historical usernames associated with the user. Previous usernames could still be used elsewhere online. On X, for example, you can use the advanced search feature to discover other usernames which once belonged to the same user. In the (altered and redacted) example below, we ran a historical search for other Twitter users mentioning the PhishLabs account to identify any previously used usernames. These historical tweets do not change when the mentioned user changes their username.
From our search, we see two tweets posted by another user who mentions @PhishL0308, meaning that @PhishLabs once operated under this username. We can now begin to dive deeper into investigating other mentions of this account. Then, if applicable, build an idea of when and why the usernames were changed.
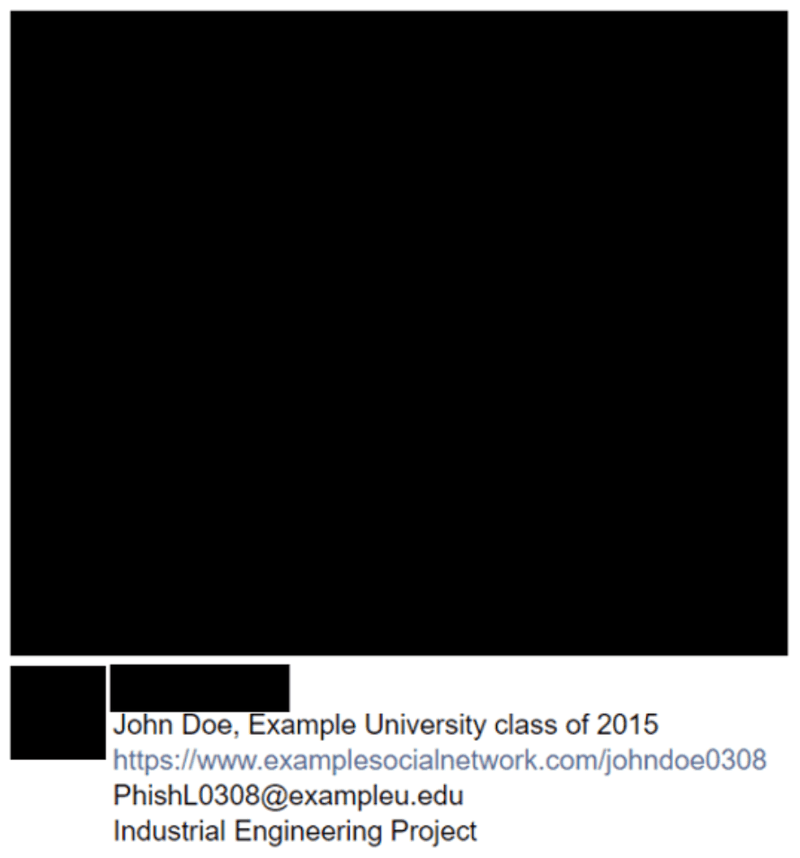
Usernames are often shared with the operating individual's email address. Running a search of PhishL0308 on other social networks led us to a post using this unique name as an email address, in addition to providing us with useful information regarding the individual’s name, school, graduating class, area of study, and link to a profile. This data can all be used as pivot points to further drive the online investigation.
As with everything online, shared usernames across different platforms and email addresses should never be taken at face value. It is important to complete your due diligence in making connections between the threat actor’s known profile and the information that becomes available to you in the course of your research, and to use sound judgement when coming to conclusions and gauging probabilities.
Learn about how Fortra Brand Protection can help: