We've all seen them before. The late prince Abdul has left us millions in inheritance and we need only provide a minor convenience fee to receive the funds. Advanced fee scams are nothing new and have been circulating the Internet since its inception. Until now, scammers have relied on email correspondence and convincing legal jargon to con victims out of their hard-earned dollars.
Recently, PhishLabs discovered an advanced fee scam with a twist - an elaborate but faux bank website. The scam begins with a classic lure purporting to be a lawyer from the African nation of Togo. The reader is informed that the inheritance money is in a foreign bank account and a link to the fake bank holding the funds is provided along with login credentials. The fraudsters registered a fake domain name to further deceive users.
Worried about consumer-focused phishing?
Watch our free on-demand webinar to learn everything you need to know about the latest consumer phishing scams.
The credential theft site was built from the ground up, even utilizing a database structure to handle user accounts.
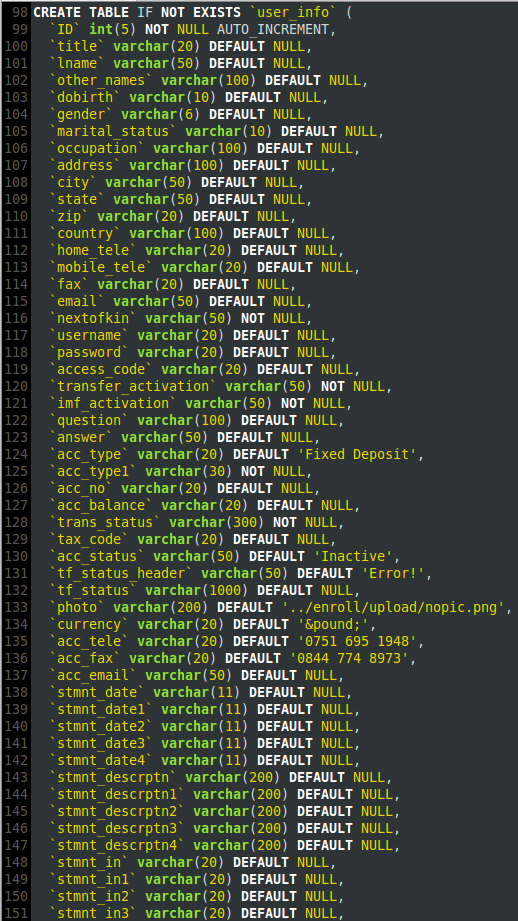
Figure 1. MySQL database creation script for fake website.
The login page is easily mistaken for a legitimate banking login page (see Figure 2). Once on the site, the user then enters the previously provided login information.
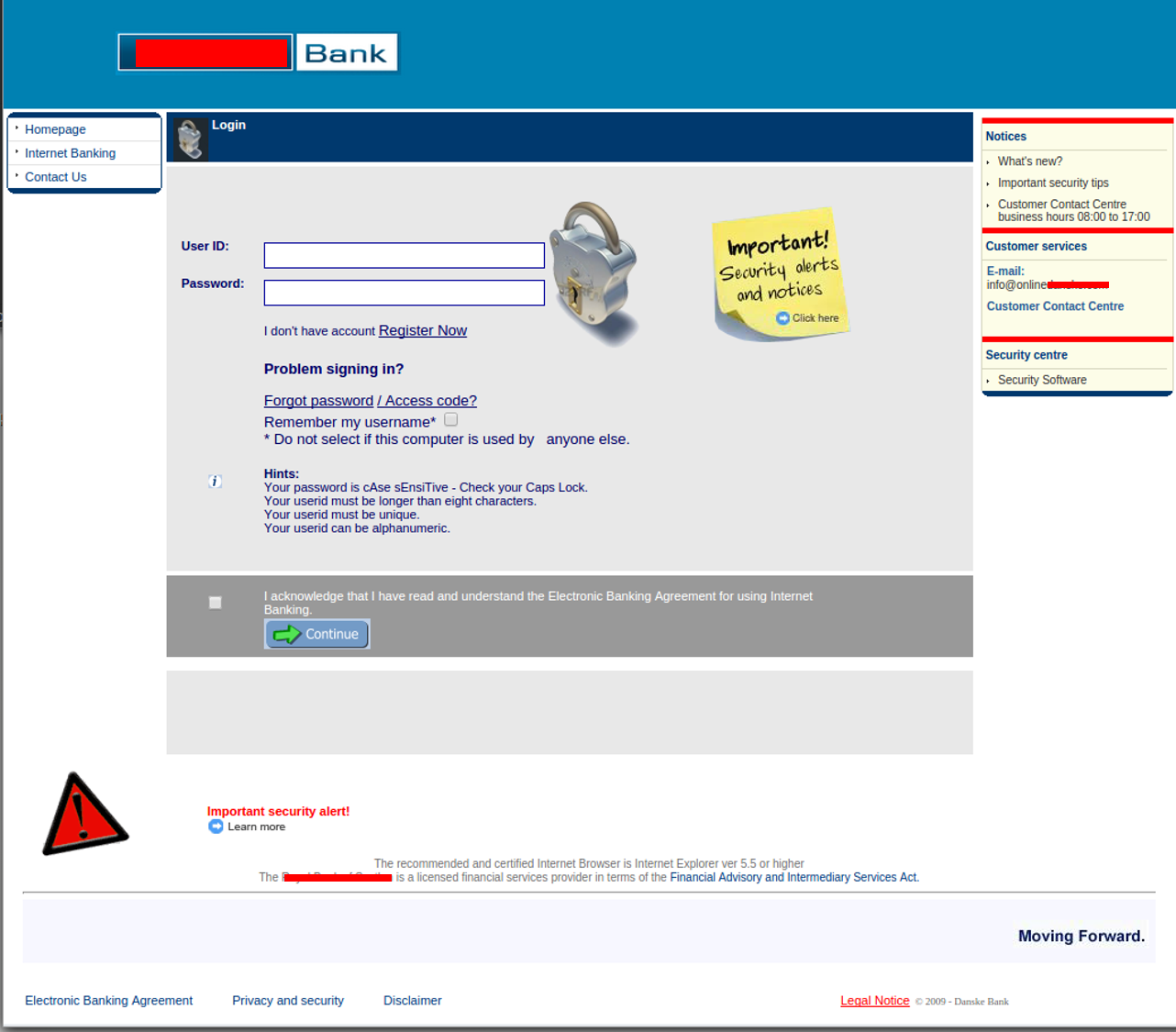
Figure 2. Fake login page allowing users to log in to transfer funds in scam.
After logging in, the reader is shown a large account balance with a conveniently placed transfer button. To boost confidence that the site is authentic, the faux bank portal even includes functionally to edit account details and upload a profile image.
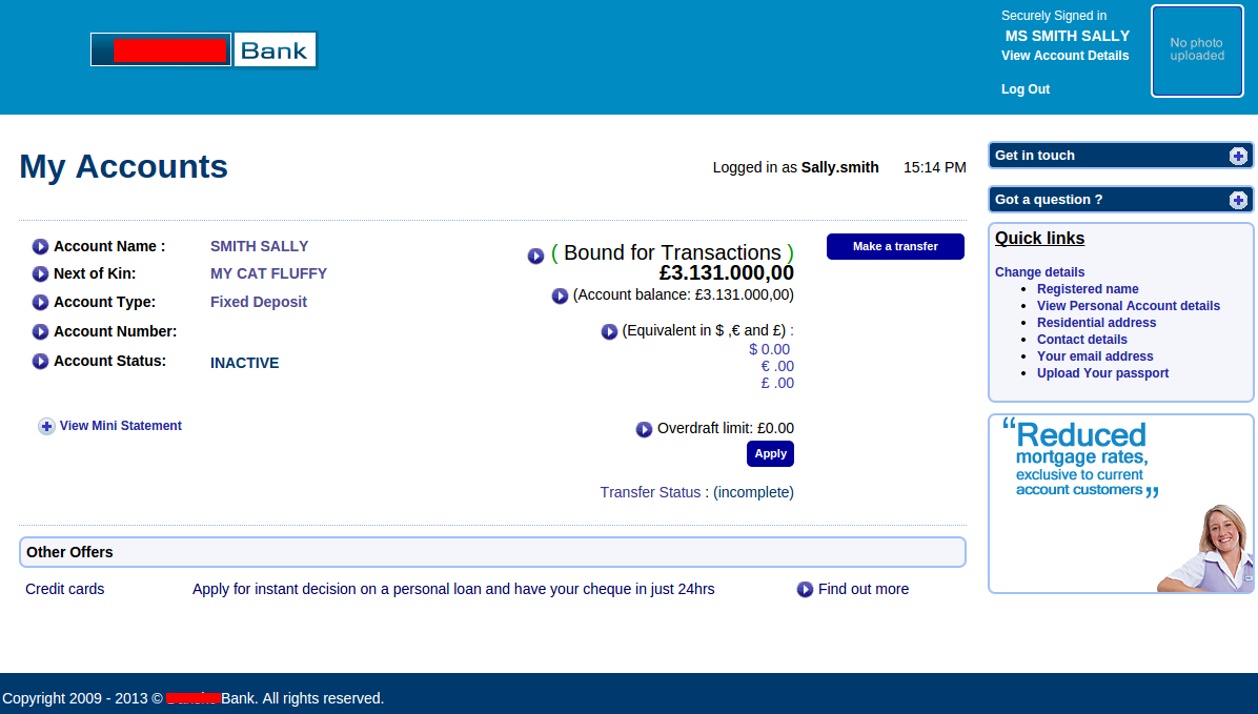
Figure 3. Fake bank account showing available funds for transfer in advanced fee scam.
The user is asked for a required “Cost of Transfer Code" which requires several thousand dollars - a small price to pay for a soon-to-be millionaire. After agreeing to pay the fee, the curious individual, now turned victim, can proceed with the fictitious transfer.
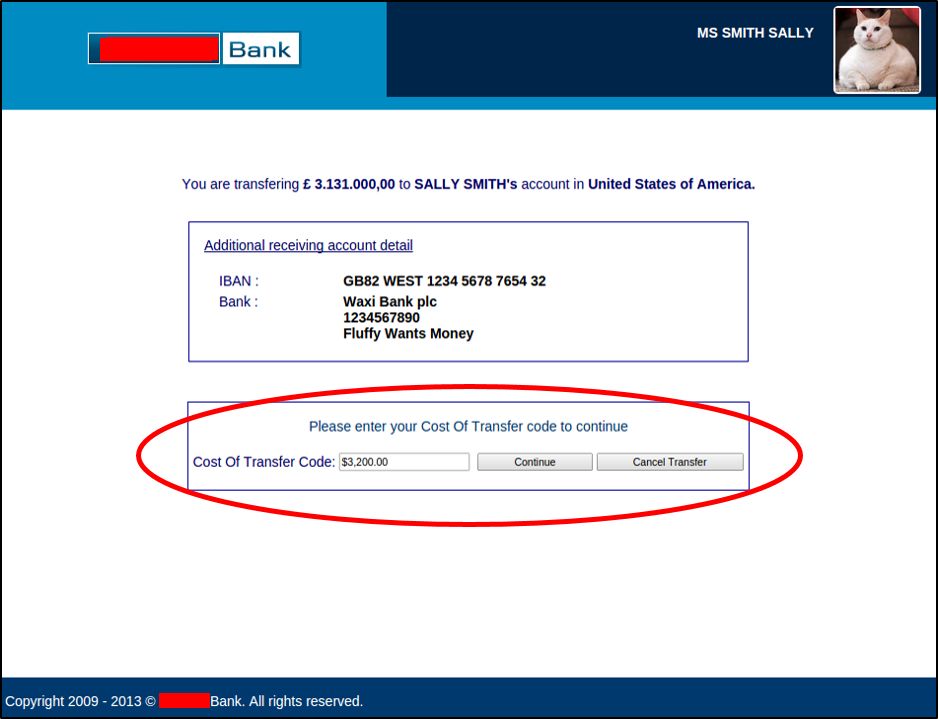
Figure 4. Cost of transfer code ($3,200) required to “transfer" funds.
The victim is required to enter bank account details, further convincing him or her that funds will be transferred.
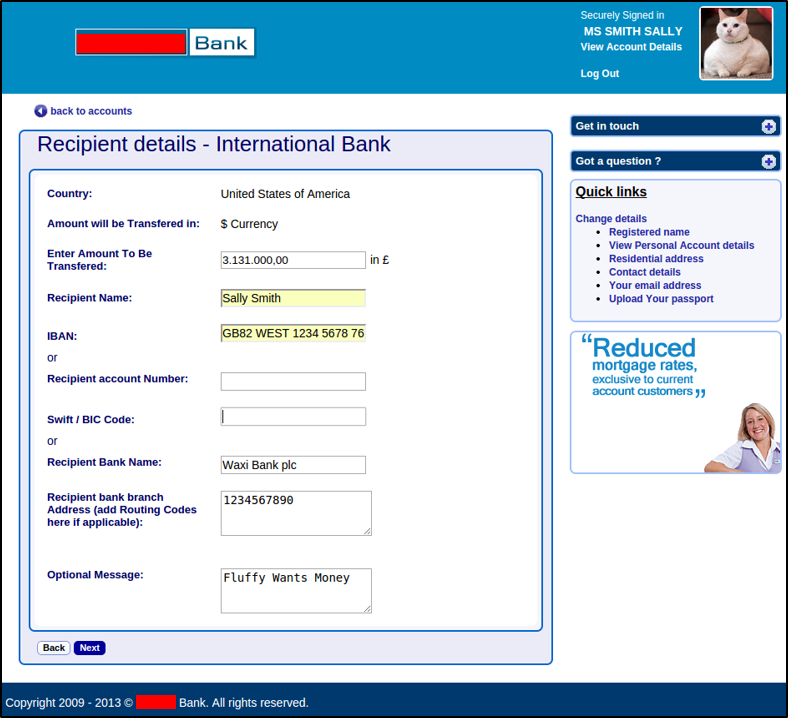
Figure 5. The fake login site requires bank account information to transfer funds.
The victim is taken through a series of convincing pages covering everything from international banking details, to disclaimers, to transfer progress pages. This convoluted fake banking site is all meant to distract and delay the victim from realizing they've been duped.
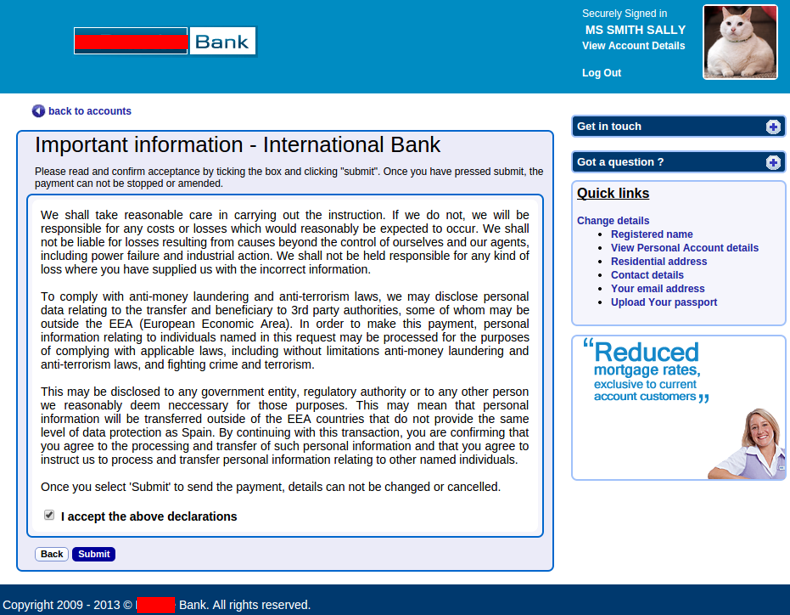
Figure 6. Declarations and acceptance requirements designed to deceive victims.
Not Your Typical Advanced Fee Fraud
Originally categorized as a phishing site, further analysis revealed this scam to be much more than just a fake login page. Instead, the site was designed to fool individuals into thinking it was a legitimate banking portal with fake balances to deceive victims for advanced fee fraud.
Financial institutions should be sure that account holders are aware of such scams and are suspicious of emails purporting to offer lump sums of money. This kind of scam not only has serious financial repercussions for account holders but it is also very damaging to banks that are being used to lure victims.
Additional Resources:
Phishing isn't a new threat... but it is a constantly evolving threat.
Register for our free on-demand webinar called "Best Practices for Enterprise Phishing Protection" and learn how your organization can combat the threat of phishing with powerful simulations & training.

