Cybercriminals register hundreds of thousands of look-alike domains each year to impersonate reputable brands and generate profit. These domains support a wide range of attacks, including phishing emails, fraudulent websites, traffic diversion, and malware distribution.
Designed to deceive, look-alike domains create the false impression that customers are interacting with trusted brands. The result is often reputational damage, financial loss, and data compromise for legitimate organizations. Because creating these domains is inexpensive, and attackers can quickly evade detection, the return on investment can be significant.
In this post, we examine how frequently the most common look-alike domain threats occur, walk through how attackers create and deploy these domains, and share practical resources to help security teams reduce the risk these threats pose to their brands.
Distribution of Common Threat Types
Look-alike domain attacks reach millions of Internet users each year. The graph below represents a sampling of 50,000 threats we typically encounter and the pervasiveness of each type.
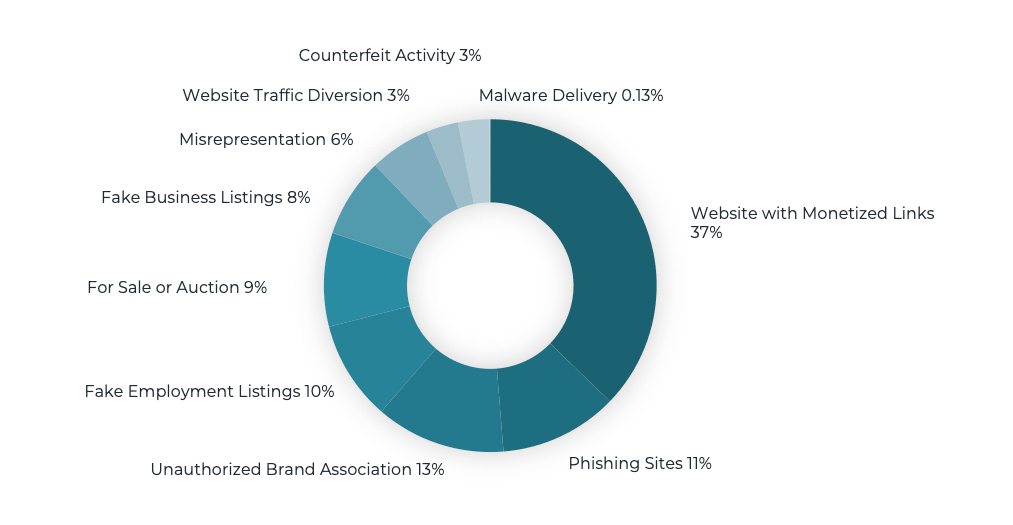
Distribution of Look-alike Domain Threat Types
The most common use of a look-alike domain is to set up a Website with Monetized Links. This approach is not necessarily malicious, yet it accomplishes multiple objectives:
- The registrant parks a domain and capitalizes on visiting traffic by adding monetized links. The link topics are typically related to the impersonated brand's keywords, increasing the probability that visitors will click through to the destination website.
- They let a domain “age" before using it. Most scammers typically use new domains quickly, yet some will maintain them for weeks or months. Recently registered domains garnered low reputation scores and are a telltale sign of malicious activity, making them targets for security teams.
- If the related organization decides they want to buy the domain, the registrant can name their price for the transfer of ownership.
Phishing sites are the second most popular type of threat and often lead to account takeover attacks. Customers are prompted to enter their credentials on a fake website, and scammers take control of their online accounts with little effort to engage in fraudulent activity.
Unauthorized brand association is a common method that scammers use to piggyback on a trusted brand's reputation. Brand impersonation typically involves using an organization's logo and colors to lend credibility to their company or event.
The most dangerous threat, malware delivery, happens to be the least common we observe in connection with look-alike domains. These typically manifest as banking trojans or ransomware attacks, and they are extremely effective as just one incident can cause a significant amount of damage.
The Mechanics of a Look-Alike Domain Attack
Most look-alike domain threats have a common structure. Following are the steps in the creation process.
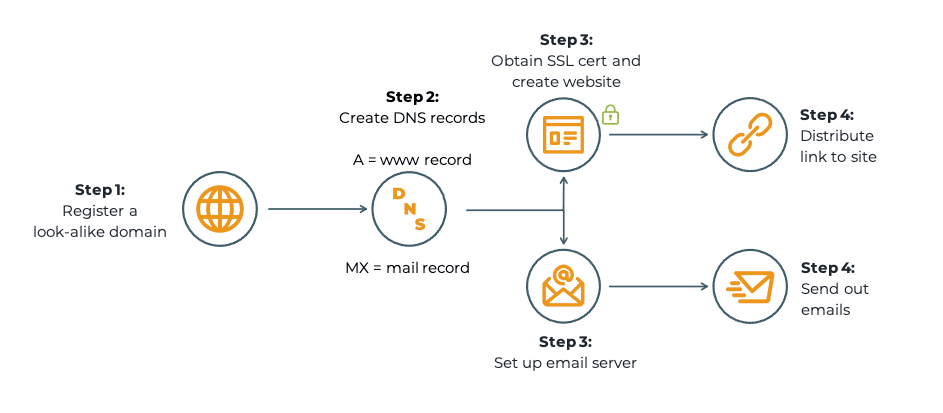
Steps to Create a Look-alike Domain Threat
Step 1: Create, find, and register a look-alike domain
Scammers will first scout out successful brands to impersonate, then find legitimate domains the company already owns or uses. They'll use techniques to slightly modify the domain like changing the TLD, using hyphenation, and transposing, adding, or omitting letters.
As they formulate new names, they will usually check for availability against the WHOIS database using free online search tools. If they can't quickly find a name or decide to create a large-scale attack, a more sophisticated scammer might automate this part of the process by writing a script that generates hundreds or thousands of variations and programmatically query the WHOIS database to find which ones are available.
Once they find their preferred name(s), they'll choose a registrar and register it online. Most scammers select from several registrars that are cheap or free and allow them to hide their identity.
Step 2: Create DNS records
Most web hosting companies offer domain, website, email, and DNS hosting with simple tools to add or update DNS resource records. However, threat actors sometimes choose to use a different provider for each service. Spreading their attacks across multiple vendors adds a layer of complexity and can make takedown more difficult.
To set up an attack using a website, the next step is to configure an “A" or “Address" record. As the most fundamental type of DNS record, A records map the domain or a subdomain to an IP address. An AAAA record, also known as a quad A record, is similar to an A record yet it points to the newer IPv6 address records.
If a threat actor plans to send emails as part of their attack, they would configure an “MX" or “Mail Exchanger" record to indicate which mail server is responsible for sending and receiving email messages on behalf of the specified domain name.
Steps 3 and 4 (website): Build the website and distribute links
Most threat actors obtain SSL certificates for fake websites to add a layer of legitimacy. SSL certification can be anonymous, obtained at no cost, and very effective at giving an appearance of safety.
Once they build a website, they'll share a link in various ways - usually via spam, SMS, blog comments, or in phishing emails.
Steps 3 and 4 (email): Set up email server and send emails
For an email based threat like a Business Email Compromise (BEC) scam or ransomware attack, a scammer might visit LinkedIn or other social media platforms to find names and email addresses of company employees to use when setting up email accounts. This added step may take time, yet it can significantly increase the appearance of authenticity.
Emails might be sent from servers where the domain was registered, the website hosting provider, or a mailer program on a compromised or third party website. The goal is to increase deliverability rates and evade detection, so attackers will change tactics as often as needed.
The last step in the process includes crafting emails, distributing them to targets, and waiting for the results.
How to Protect Your Organization
Enterprises can effectively defend against look-alike domain threats by establishing an ongoing process for data collection, intelligence curation, and threat mitigation.
However, identifying and disrupting a single attack is often not enough. Cybercriminals can quickly swap out websites, phone numbers, and hosting infrastructure to restart their campaigns.
Because look-alike domains can seriously — and sometimes permanently — damage an otherwise healthy organization, security teams must take a proactive and comprehensive approach to prevent domain abuse and fraudulent activity.
