Threat actors are increasingly registering new domains to launch malicious campaigns against enterprises. Identifying suspicious domains, as well as monitoring existing ones for changes, is an overwhelming and reactive task for many organizations. In order to minimize the risk spoofed domains pose, security teams must be able to efficiently detect abuse and understand what is required to mitigate threats.
Using a fraudulent domain to conduct a cyber-attack is an optimal choice for threat actors because a domain string can be manipulated an endless number of ways. A spoofed domain can be used to host malicious or unauthorized content, lead to a phishing site, or redirect to an unintended page.
The consequences of a spoofed domain can be damaging for an organization and result in everything from loss of brand trust to data compromise.
Following are a few examples that demonstrate how domains can be used to harm an organization.
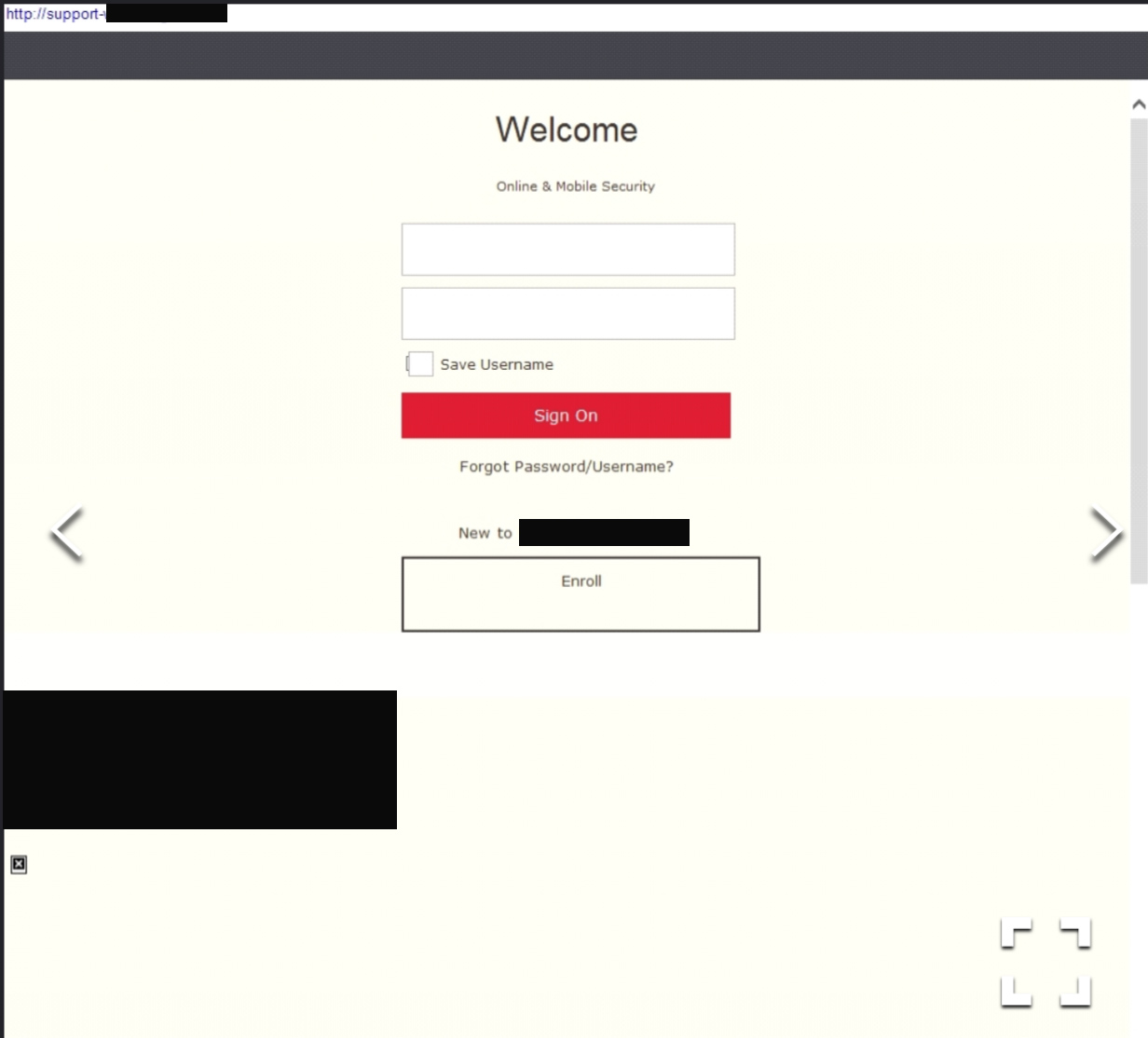
In the first example, the domain name impersonates technical support for a large enterprise to execute a credential theft scam. After this page was identified as malicious it was promptly taken offline.
Domain: http://support-{redacted}-{redacted}.com
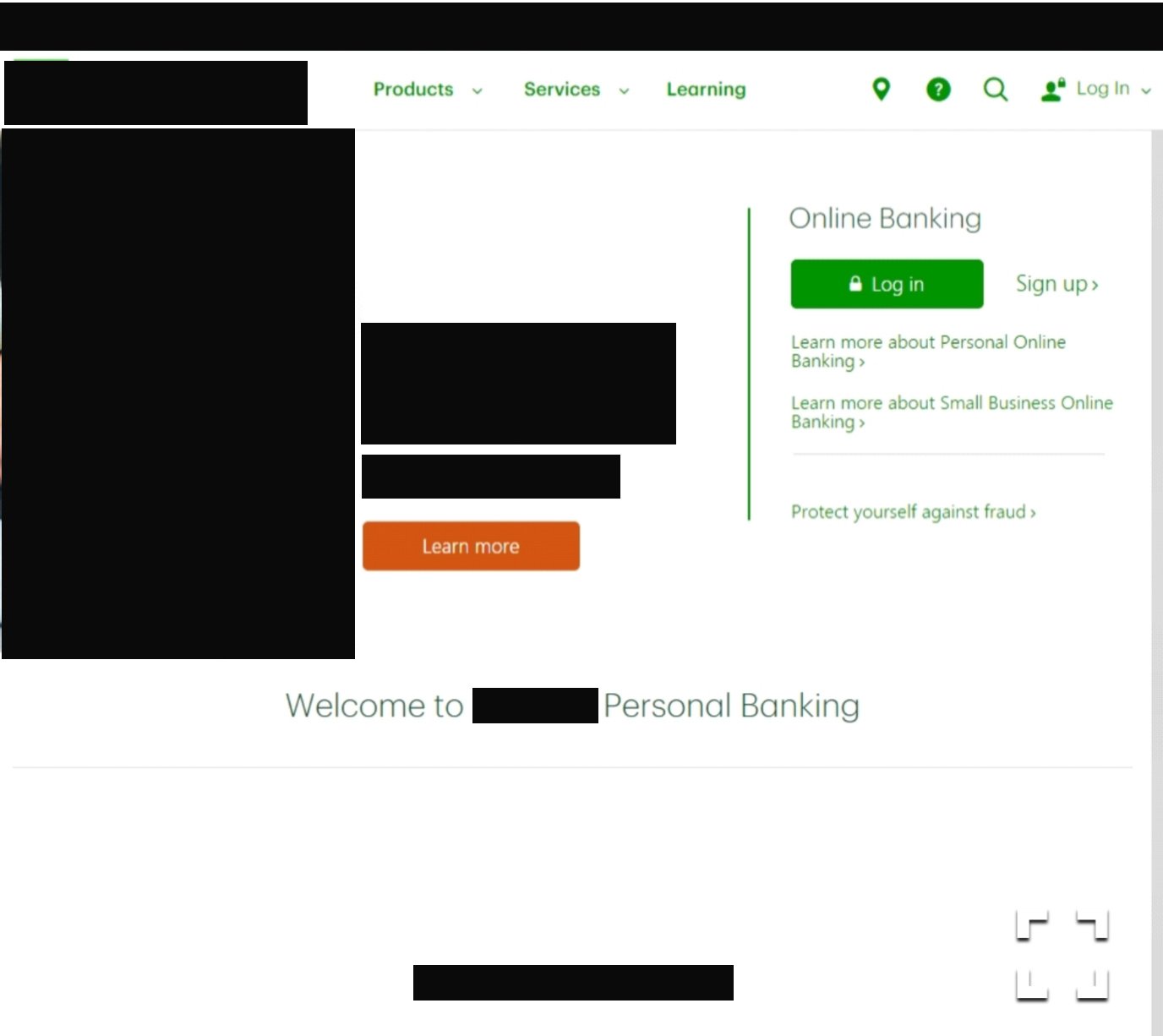
The second example uses typo-squatting to resemble a large financial institution. The domain has a live mail exchanger (MX) record, giving the threat actor the capability to conduct malicious email campaigns.
The domain ecosystem offers numerous opportunities for manipulation, and the ease of domain registration makes it an attractive attack vector for threat actors. In the past year alone, we observed a year-over-year increase in the use of free domains to host phishing sites, which accounted for 32.6% of total phishing volume.
Enterprises can manage spoofed domains more effectively by establishing a mature, continuous process for domain collection and curation. Once a domain is identified as malicious, security teams need a comprehensive mitigation strategy — one that not only focuses on takedown efforts but also leverages indicators to prevent internal users from accessing the threat.
Off