Last updated on August 05, 2025.
Threat actors employ look-alike domains in a variety of ways. While business email compromise (BEC) and phishing are among the most recognized tactics, these domains serve many other malicious purposes. The sheer range of use cases, combined with inconsistent registrar policies for domain takedown, makes mitigation a complex, time-consuming, and often ineffective process.
To mitigate a malicious domain, security teams need a comprehensive strategy that includes protecting users within the network perimeter as well as externally. Measures for securing a network include using indicators to prevent access to the threat. Finally, threats outside the perimeter must be removed completely.
This blog explores the essential steps organizations must take to reduce the internal and external risks associated with look-alike domains.
Integrate Look-Alike Domains into Enterprise Security Controls
Many network and endpoint security controls can ingest malicious domain intelligence for enhanced threat detection and prevention. By integrating look-alike domains into these tools, security teams can block delivery of the threat or at least keep internal users from interacting with it. Automated integration of look-alike domain intelligence is a best practice.
While this provides an efficient layer of protection for corporate users on the network, it does not address the risk posed by look-alike domains to users outside the corporate network or to the organization's brand.
Taking Down Look-alike Domains
The only way to fully eliminate the risk posed by a look-alike domain is for it to be removed by the registrar. Accomplishing this is not always a straightforward process.
Depending on how the look-alike domain is used, its registrar may not consider it to be malicious. Registrars have various evidentiary requirements to demonstrate a domain is being used for nefarious purposes and should be removed. Without sufficient evidence, registrars are under no obligation to remove the offending domain.
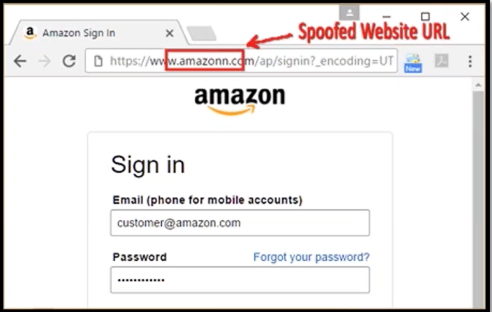 Example of a look-alike domain
Example of a look-alike domain
It's essential to have a process in place to
investigate look-alike domains and capture evidence sufficient to warrant the threat being removed. Domain registries generally have broad anti-abuse authority and with sufficient evidence will remove domains being abused for:
- Hosting phishing sites
- Hosting malware
- Botnet command and control
- Distributing child exploitation materials
- Delivering spam
Not all domain abuse is overtly obvious, and removal requires additional evidence. For example, fraud can be viewed as intellectual property or a trademark dispute, and most registrars will not issue removal without a court order or law enforcement request. Because of the ambiguity surrounding less defined threats, security teams need to prioritize the rapid gathering of incriminating evidence and ensure it is aligned with registrar requirements.
The fastest way to mitigate a domain threat is to provide clear, indisputable evidence that the domain is engaged in fraudulent activity. Registries are far more likely to take action when abuse is evident and well-documented. Additionally, your organization’s reputation and track record in handling domain threats can significantly improve the chances of a successful takedown.


