Every year, cybercriminals spin up hundreds of thousands of look-alike domains — tiny, deceptive variations of real web addresses that exist purely to trick people and steal money. A look-alike domain is a nearly identical domain name, registered with intent to impersonate a legitimate brand. In this post we’ll show how domain names power online communication, break down the anatomy of these deceptive addresses and the psychological tricks that make them effective, explain how attackers create and scale them, and tell you the first, practical steps to protect your brand and your users.
Read on to learn how to spot the subtle differences, stop the scams, and reclaim control of your online identity.
Domains: The Foundation of Online Communication
At its core, the Internet is about connection. Every device has an IP address, a unique number that allows information to flow back and forth. But numbers aren’t easy to remember and as the Internet grew, people needed a simpler way to navigate it.
That’s where domains come in. A domain name translates into an IP address, directing browsers and email clients to the right website or mail server. Just like a name distinguishes a person, a domain gives a business its digital identity.
Think of it like a phone number: you could dial the digits directly, but most of us just tap a saved contact. In the same way, domains spare us from memorizing long strings of numbers and make online communication human friendly.

Thanks to our modern Domain Name System, businesses can send customers to a user-friendly website name like www.acmebank.com rather than 65.154.128.12. Attackers know we use domain names to interact with our preferred vendors. They are also aware that we enter credentials to log in to websites, make purchases by inputting credit card details, and exchange emails with these vendors.
Anatomy of a Look-alike Domain
Domain names act as a map to tell browsers and other applications how to find what we're looking for. Explaining the full structure of domain names and their hierarchy is more complex than this, yet here are the basics:

- The top-level domain portion on the far right can identify the location where the domain registrant resides, their organizational purpose, or even the industry of the business that registered it.
- The second-level domain section is the address name and unique identifier often manipulated to impersonate domains used for legitimate purposes. They enable our computers to find the server where a website or email is hosted.
- A subdomain is a part of the domain that helps registrants organize a website into different sections or categories. Subdomains can also use to create look-alike domains., like phishlabs.000webhost.com.
Using our everyday habits to their advantage, threat actors register look-alike domain names to create confusion. They lead us to believe we are visiting the websites or responding to emails of the brands we trust. Although their uses vary widely, threat actors typically register look-alike domains to profit from a recognizable brand's credibility. Also called a spoofed domain, fake domain, cousin domain, or doppelgänger domain, they typically include a company name, service name, or trademark with a typographical variation.
How Our Brains “Hack" Look-alike Domains
Research shows that look-alike domains appear legitimate for a reason. The human brain doesn’t read words letter by letter; it processes the word as a whole. This means we often overlook spelling errors that, if examined closely, would seem like nonsense. Our brains constantly anticipate what comes next, using context, current input, and past experience to predict and fill in gaps.
Even if the letters within a word are jumbled, we can still recognize the word correctly. This phenomenon is known as Typoglycemia, which suggests that readers can understand text despite misplaced or scrambled letters. Here’s an example:
Aoccdrnig to rscheearch at Cmabrigde Uinervtisy, it deosn't mttaer in waht oredr the ltteers in a wrod are. Tihs is bcuseae the huamn mnid deos not raed ervey lteter by istlef, but the wrod as a wlohe.
Reading words instead of letters provides a cognitive shortcut for our brains. We're able to see dominant patterns, batch information together, and conserve mental resources. Since look-alike domains usually have small variations from the original domain, most people don't even notice the difference. Scammers know that anyone reading a look-alike domain containing a slight variation will automatically correct any misspellings, and they use this to their benefit.
What’s Behind the Surge in Look-alike Domains?
Threat actors register look-alike domains to impersonate well-known companies, leverage their credibility, and make a profit from various scams. The process is inexpensive, and threat actors will see a large return on their investment if they know what they're doing and move quickly to evade detection.
Here are some examples of how attackers create look-alike domain names:
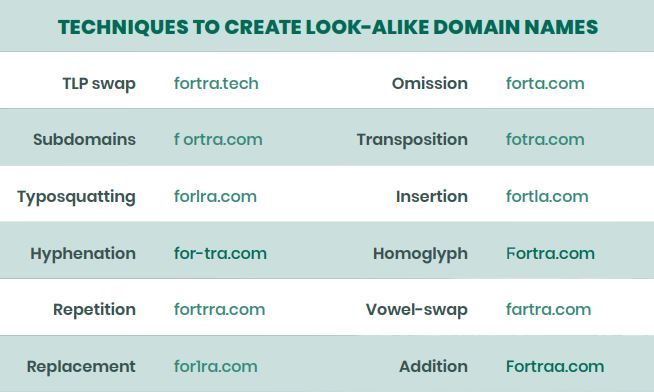
With millions of permutations available, scammers have endless choices when registering a look-alike domain.
The Cybercriminal’s Favorite Shortcut
Look-alike domains are among the most adaptable tools in a threat actor’s arsenal. Why? Because they can be used in multiple ways to launch a wide range of attacks. Whether hosting a fake website, sending deceptive emails, or both, these domains lay the groundwork for phishing, business email compromise (BEC), and even ransomware campaigns.
What makes them especially dangerous is how easily they bypass traditional email security. Since these domains are fully registered and operate through legitimate email servers, they don’t raise red flags. They pass authentication checks like SPF, DKIM, and DMARC, making them appear trustworthy to both users and security systems. That’s what gives attackers a clear path to compromise.
Reputation Damage Is Hard to Undo
Criminals eagerly use brand impersonation to target prominent organizations online for financial gain. When they register look-alike domains, create poorly designed websites with recognizable logos, and send emails that appear to be legitimate, they diminish the targeted brand's value. Look-alike domains tarnish a business' reputation, too, resulting in customer churn and financial impact. Once they've been duped, customers get angry at both the attacker and the brand. They usually start looking for alternate vendors and tell people they know about their experience.
Building a Strong Defense Against Look-alike Domains
One of the most common questions we hear when organizations begin building a Digital Risk Protection (DRP) program is: “Where should we start?” The answer: start with domains.
- Create a domain protection program. Domains are a common foundation for many different types of threats. Starting with domains is also easier than creating other external threat programs. If you are looking to protect your organization from brand impersonation and build out a domain protection program, start by collecting new domain data, then put in place a practice of filtering or curating data that leverages technology and people.
- Create your playbooks for mitigation using a combination of domain takedown services and/or IT security controls.
- Continuously monitor new and existing domains. Domain monitoring should be a high priority for any security team. Watching for indicators of brand impersonation such as mail record changes or new infringing content will keep you ahead of the game and possibly lead to disrupting an attacker's infrastructure before it goes live or causes any damage.
