PhishLabs has observed a spike in malicious emails distributing ZLoader malware. The spike is notably one of the greatest upticks for a single payload observed in a 24-hour period over the past year, and is the first significant sign that another botnet may be stepping up in the aftermath of the Emotet takedown.
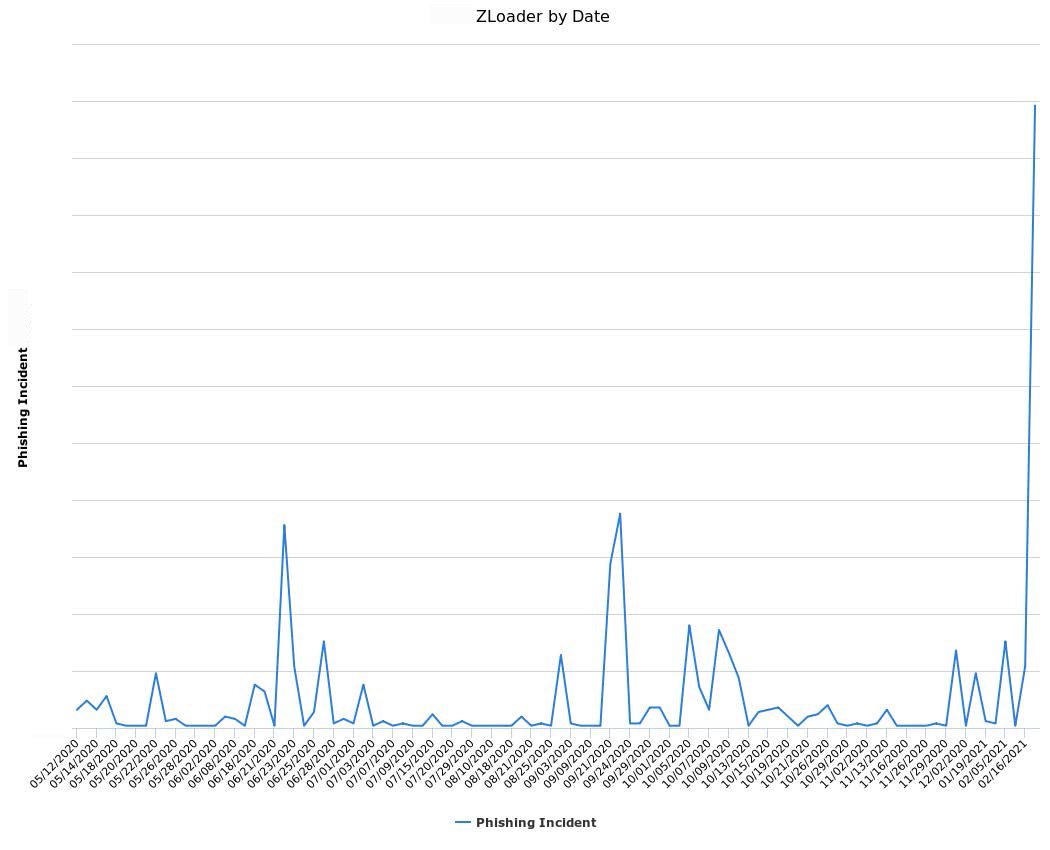
May 2020 - February 2021 ZLoader Activity
ZLoader is one of the most frequently reported malware strains since June 2020. This particular campaign uses three legitimate file sharing platforms to distribute attacks: WeTransfer, Google Docs, and box.com. Emails are delivered through a variety of compromised accounts. The payload is delivered via malicious files and download links.
WeTransfer Example
WeTransfer Sender Address: [email protected]
WeTransfer Subject Line: sent you files via WeTransfer
WeTransfer URL:
hxxps://wetransfer[.]com/downloads/52d55eeb42591d9ebbffe5326326858320210218183005/8b80cbbd9c1b8f7695b8de69e995ebee20210218183005/8c0cd5?utm_campaign=WT_email_tracking&utm_content=general&utm_medium=download_button&utm_source=notify_recipient_email
WeTransfer Phishing Lure
Additional Lures
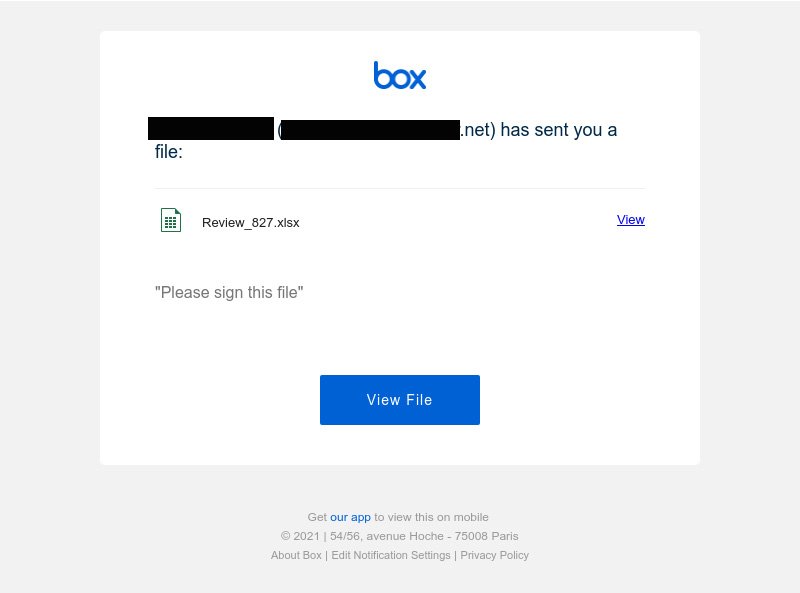 Box.com Phishing Lure
Box.com Phishing Lure
Google Docs Phishing Lure
ZLoader is a popular banking trojan often purchased for distribution by threat actors through Malware-as-a-Service (MaaS). It is a derivative of the Zeus banking trojan and commonly known for stealing victim's credentials through web injects.
ZLoader is delivered through email phishing and there are indications that it is linked to Ryuk and Egregor ransomware strains.
Learn about how PhishLabs helps organizations defend against ransomware risks with Ransomware Protection.
Additional Resources:
