Account Takeover Attacks Put Every Login at Risk
Cybercriminals use every tactic available to steal credentials and seize online accounts. From convincing phishing sites and voice scams (vishing) to text-based fraud (smishing) and malware across mobile and desktop devices, attackers stop at nothing.
Once credentials are compromised, threat actors can hijack customer accounts, execute fraudulent transactions, and cause not only major financial losses but also lasting damage to your organization’s reputation.
Stay Ahead of Sophisticated Phishing Attacks
Threat actors constantly evolve their tactics to slip past detection. By deploying new evasion techniques, scammers keep phishing campaigns active longer, maximizing their chances of success.
To limit damage, organizations need to detect and disrupt these campaigns quickly. Staying ahead of advanced evasion methods requires adaptive countermeasures that can spot threats the moment they emerge.
Fortra Brand Protection applies advanced anti-evasion technology to uncover and analyze active phishing campaigns. Our experts map the hidden infrastructure behind attacks and deliver high-fidelity intelligence that continuously strengthens detection systems. The result: faster, more precise identification of threats and the ability to shut down malicious campaigns before they launch or inflict damage.
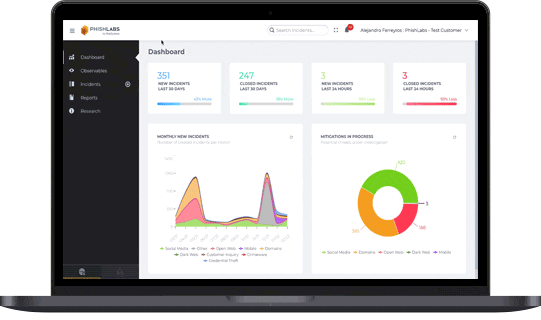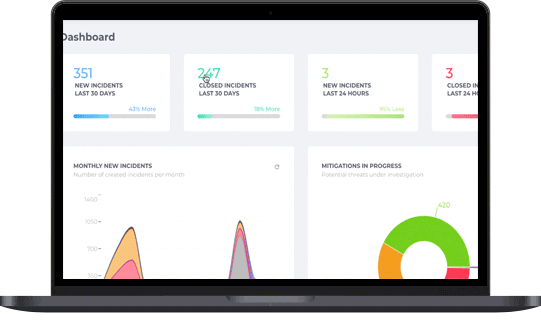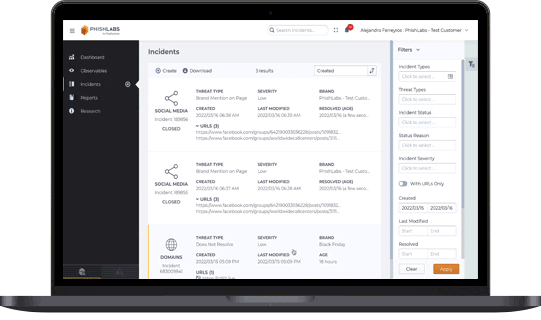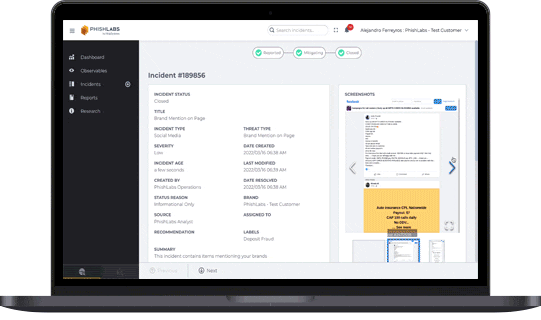
Protect Your Customers’ Most Sensitive Data Online
Cybercriminals are skilled at tricking users into giving up credentials and sensitive data. Once they gain access, compromised accounts become launchpads for data theft, malware distribution, and wider attacks.
Early detection is essential. Stopping phishing campaigns before damage occurs protects customer data and prevents account takeovers. Achieving this requires broad, proactive visibility across diverse online intelligence sources, ensuring threats are spotted and neutralized before they escalate.
Fortra Brand Protection technology consumes and monitors intelligence from a robust set of sources, including over 350 million potential phishing URLs daily from new domain registrations, SSL transparency logs, passive DNS data, active DNS queries, and DMARC failure reports. With advanced proactive detection, the largest phishing dataset, and world-class expertise, our ability to accurately detect phishing campaigns that lead to account takeover attacks is unparalleled.
Unrivaled Takedown at Enterprise Scale
Early detection is only part of the equation. Swiftly disrupting phishing infrastructure and taking down credential theft sites dramatically reduces the risk of account compromise. Yet navigating the slow, inconsistent processes of ISPs, hosting providers, and registrars can create critical delays.
Fortra Brand Protection accelerates your response. Through a global network of trusted provider relationships, automated integrations, and streamlined reporting, your organization can take down threats faster and more efficiently.
Fraudsters are using sophisticated automation to amplify attacks and increase success rates. Effective takedowns require not just speed, but scale — and the ability to act across high volumes of threats without delay. With direct access to automated killswitches and preferred escalation channels, Fortra Brand Protection delivers unrivaled enterprise-scale threat takedown, keeping attacks contained before they can inflict damage.