Impersonation allows threat actors to manipulate victims into revealing sensitive information and enables more sophisticated fraud schemes. By co-opting an organization’s name, logo, or messaging, attackers can embed themselves into nearly any type of cyber threat, making impersonation both easy to execute and hard to defend against. Because of its wide-ranging applications, organizations must understand the many ways impersonation can be exploited to effectively protect themselves.
In this blog, we examine various impersonation tactics targeting a single financial institution, highlighting the diverse risks any organization may face.
Look-alike Domain
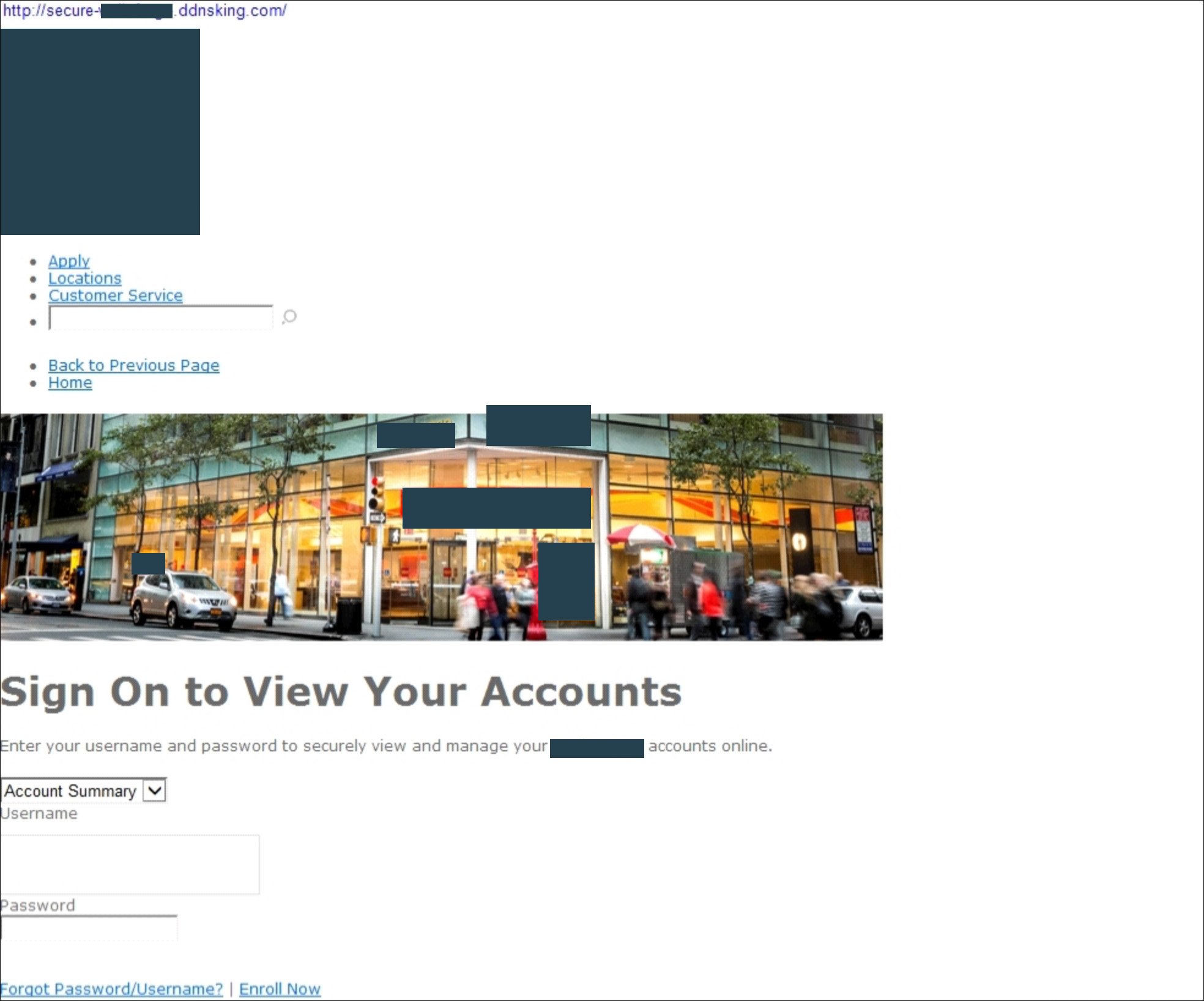
Social Media Impersonation
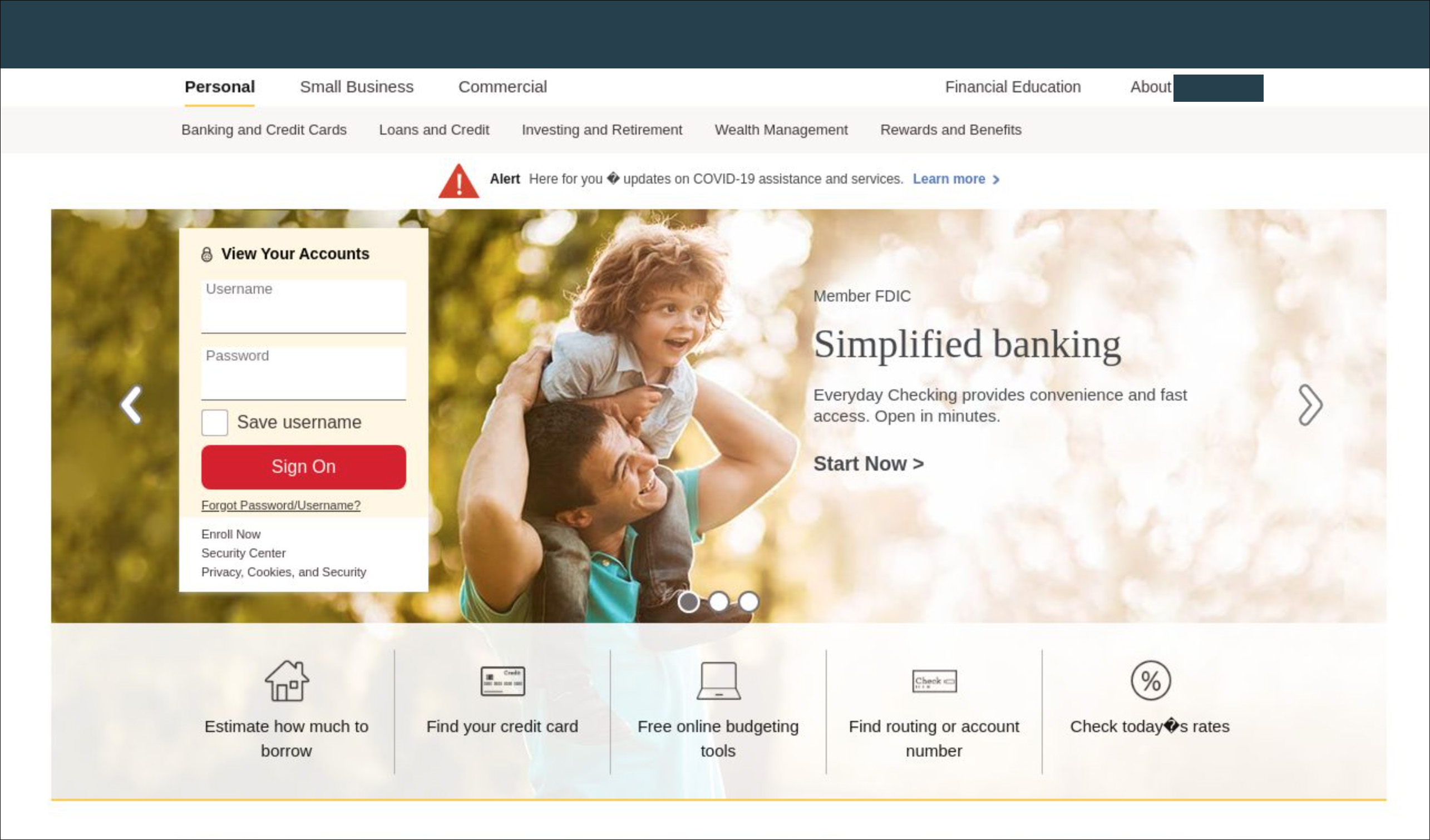
Brand Impersonation
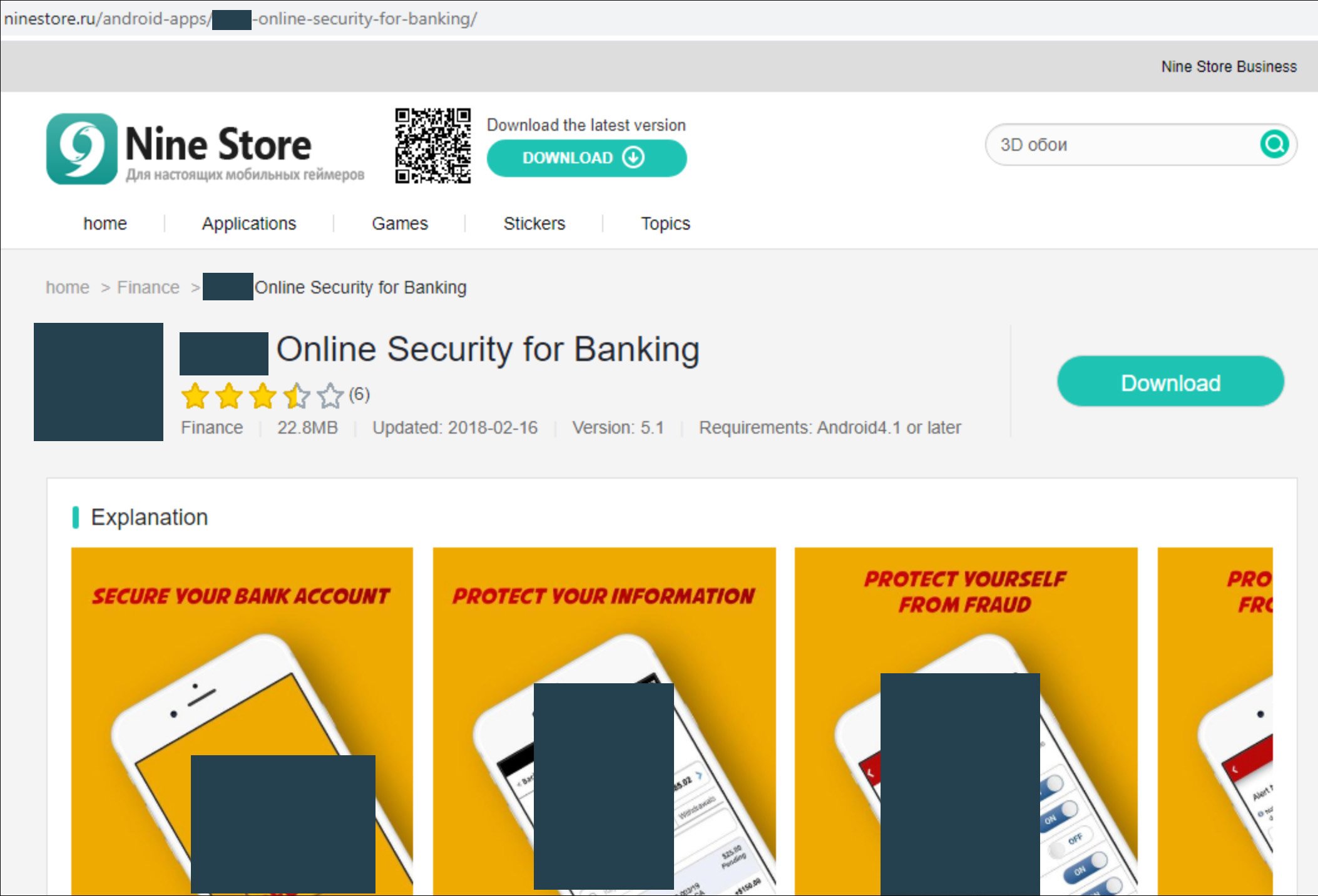
Mobile App Impersonation
Executive Impersonation
Advanced Email Threats
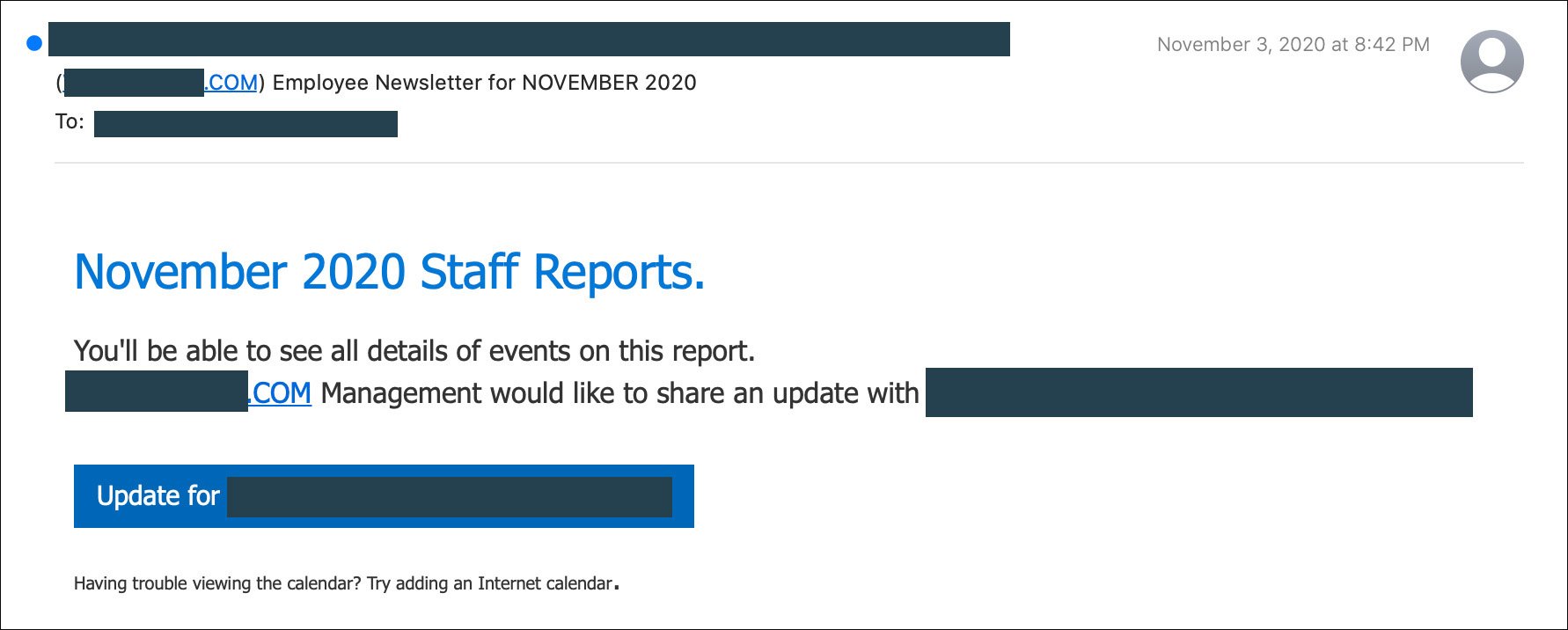
Phishing remains the top attack vector, accounting for one-third of all security breaches. In the example above, a threat actor impersonates management to deliver a fake staff report, using a spoofed sender address and referencing the financial institution to increase credibility.
Impersonation is a highly versatile tactic that leverages a brand’s reputation to boost the success of cyber attacks. It spans various threat types, making it a favorite method among cybercriminals. Detecting impersonation threats can be complex and resource-intensive, requiring comprehensive data collection and careful analysis. Fortra Brand Protection Digital Risk Protection helps organizations with unmatched threat intelligence for brand impersonation.
- Defending Against Look-Alike Domains
- Securing the C-Suite: Advanced Executive Protection
- Disrupt Counterfeit Threats
