How It Works
Our core software platform powers our Digital Risk Protection solution. Built over a decade alongside the world’s most targeted brands, it offers comprehensive data collection, expert curation, and full mitigation of digital threats — including brand impersonation, data leaks, social media risks, and account takeovers — all within a single, unified solution.
A Leading DRP Solution
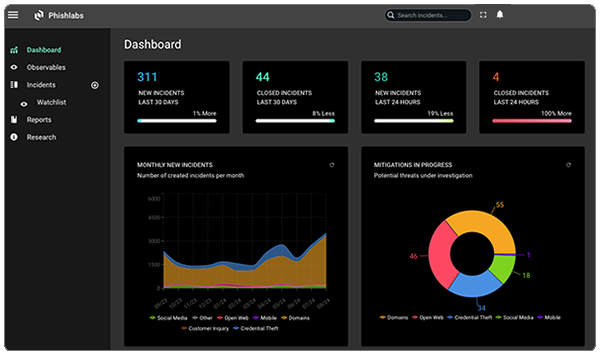
Our web-based platform gives customers full visibility into digital risk protection, allowing them to easily view, track, and manage the threats we detect and resolve on their behalf, all in one centralized dashboard.
Prioritized alerts for critical threats ensure you never miss an important update. The dashboard allows for clear, actionable insights into threat trends and key performance indicators that matter most. Easily sort, search, and review threats with a centralized, chronological view that simplifies decision-making.
Detailed screenshots provide a secure view into malicious activities without any direct interaction. Incident filtering lets you quickly pinpoint specific threats, save your preferred filters, and stay focused on what matters most.
Gain Visibility into External Threats
Brand impersonation, data leakage, and other external threats can happen anywhere online. Without extensive visibility across digital channels, these threats can easily go undetected and cause substantial harm.
Our Digital Risk Protection solution provides deep, comprehensive visibility by continuously collecting data across the surface, deep, and dark web. We monitor thousands of social media sources and integrate hundreds of public, private, and client-specific feeds, including referrer logs and third-party data.
Using automated crawling, parsing, anti-evasion, and pivoting techniques, we process this data at scale to generate actionable intelligence. Our expert analysts then enrich these insights with advanced sourcing methods to ensure maximum relevance and accuracy.
Machine and Human Collection Methods
Web
Surface, Deep, Dark Web, Mobile App Stores
Data Feeds
URLs, Passive DNS, SSL Certs, Email and SMS Spam, Malware

Social
Social Networks, Paste Sites, Gripe Sites, Blogs

Client Sources
3rd Party Feeds, Referrer Logs, Abuse Reports, Web Beacon
Comprehensive Intelligence Sourcing

Parsing
Flexible Parsing Automates Data Ingestion Across Sources

Anti-evasion
Anti-Evasion Techniques Detect Hidden Malicious Content

Crawling
Advanced Crawling Technology Captures Web Data

Pivoting
Pivoting Processes Identify Related Threat Infrastructure
Reduce Noise, Find Threats

The vast and ever-expanding volume of online data overwhelms most intelligence tools, flooding security teams with false positives, low-fidelity alerts, and time-consuming analysis. Valuable resources are pulled away from strategic priorities to sift through noise.
Our Digital Risk Protection solution cuts through that noise. By combining advanced automation with expert validation, we eliminate false positives and deliver high-fidelity, action-ready intelligence.
The platform continuously processes massive data volumes in near real-time, using risk-scoring algorithms to identify potential threats to client assets. Our analysts then validate and enrich these results, ensuring every alert is accurate, relevant, and prioritized.
This curated approach dramatically reduces manual review, shortens threat lifecycles, and eases the burden on internal teams. It ensures faster, more confident response and allows organizations to focus on what matters most.
Address Threats Quickly and Completely
Effective Digital Risk Protection demands a comprehensive mitigation strategy, one that swiftly and fully neutralizes online threats. Partial measures, like feeding indicators into internal controls, fall short and leave brands, customers, and employees exposed to real harm.
Fortra Brand Protection delivers a complete mitigation strategy through our extensive global takedown network, browser-blocking, and automated integrations with internal controls.
Instead of relying primarily on automated form submissions and emails, our system connects directly to service providers via proprietary Killswitches and takedown APIs. This enables the fastest, most effective threat takedowns in the industry. By combining takedown actions with browser blocking and seamless integration into internal security controls, we ensure threats are rapidly identified, neutralized, and fully contained.

Global Takedown Network
Killswitch Integrations, Takedown APIs, Strategic Relationships, Browser-blocking, DMCA Takedowns

Client Web App
Executive Dashboard, Incident Management, Intuitive Workflows, Reporting and Analytics

Reporting APIs
Threat Intelligence Indicators, Incident Data Reporting, Incident Creation
Explore Our Digital Risk Protection Solutions
Brand Protection
Continuously harvests vast volumes of data across the surface, deep, and dark web — as well as social media — to detect brand mentions, keyword variations, and potential threats in real time.
Account Takeover Protection
Leverages a vast global network of trusted providers to disrupt phishing infrastructure, mitigate active attacks, and rapidly take down malicious sites, minimizing the risk of account compromise and brand damage.
External Data Leaks
Delivers 24/7 visibility across a broad range of digital channels to proactively detect data leaks, track stolen data shared by threat actors, and rapidly remove exposed information from the open web and social media.
Human Risk Management
Delivers targeted, engaging training with a practical, people-first approach, using interactive modules and real-world simulations to reduce risk and build a resilient human defense against cyberattacks.
Social Media Protection
Collects data from thousands of social media platforms, categorizes it, and enriches threats with precise automated risk analysis, enhanced by expert review for deeper context and accuracy.
