Digital Risk Protection is defined as an operational process that combines intelligence, detection, and response to mitigate attacks across the external digital risk landscape.
Today's enterprise attack surface is not limited to the corporate network. In fact, the network is just a small slice. When it comes to deciding how and where to attack an enterprise, threat actors have ample opportunity beyond the network perimeter. As a result, enterprises are investing in operational capabilities to detect and respond to external threats across the digital risk landscape. This is Digital Risk Protection (DRP).
The Importance of Digital Risk Protection
External digital threats are growing in scale and sophistication. As business increasingly moves beyond traditional networks — through channels like social media, mobile apps, and web platforms — organizations face greater exposure than ever before. The shift to remote work and accelerated digital transformation only intensified this trend, often leading to rushed adoption of tools outside the enterprise’s direct control. The result? A perfect storm for cybercriminals. It’s never been easier for threat actors to impersonate brands, hijack accounts, and exfiltrate data. Risks like account takeover, brand abuse, and data leaks have reached unprecedented levels, putting defenders in a tough, uphill battle.
DRP levels the playing field by detecting and mitigating external threats across the surface web, social media, app stores, dark web, and deep web.
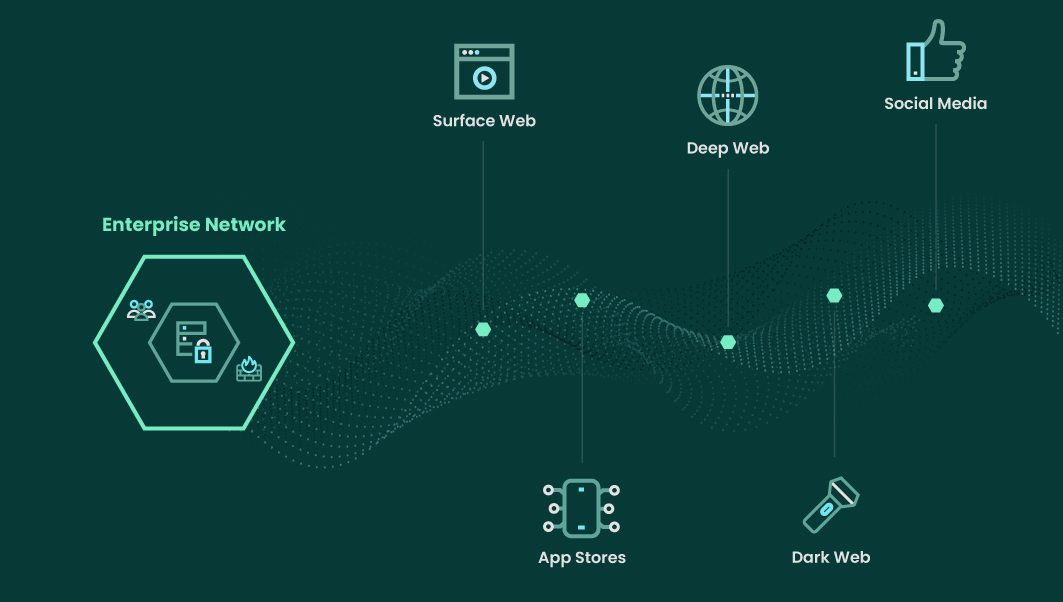
Digital Risk Protection Use Cases
The most common use cases for DRP include:
- Domain Monitoring
- Social Media Protection
- Brand Protection
- Account Takeover Protection
- Data Leak Protection
- Executive Protection
Many enterprises first adopt DRP in response to a specific incident or persistent threat, typically focusing on one or two urgent use cases. Over time — as threats evolve and organizational needs shift — these programs often expand to cover a broader range of risks.
Figuring out which use cases to prioritize isn’t always straightforward — threat categories often overlap, and tackling them usually involves collaboration across various teams and stakeholders.
Managing Digital Risk with DRP Solutions
According to the Gartner Hype Cycle for Security Operations, “DRP solutions help improve the ability to predict, prevent, detect, and respond to issues presented by the prevailing threat landscape in a cost-effective, expedient and efficient approach." Organizations rarely have the skill set to implement DRP on their own. As a result, DRP often requires partnering with solution providers.
3 Key Functions of a DRP Solution
There are three components' organizations need to incorporate into their DRP process in order to effectively protect against external threats: collect, curate, and mitigate.
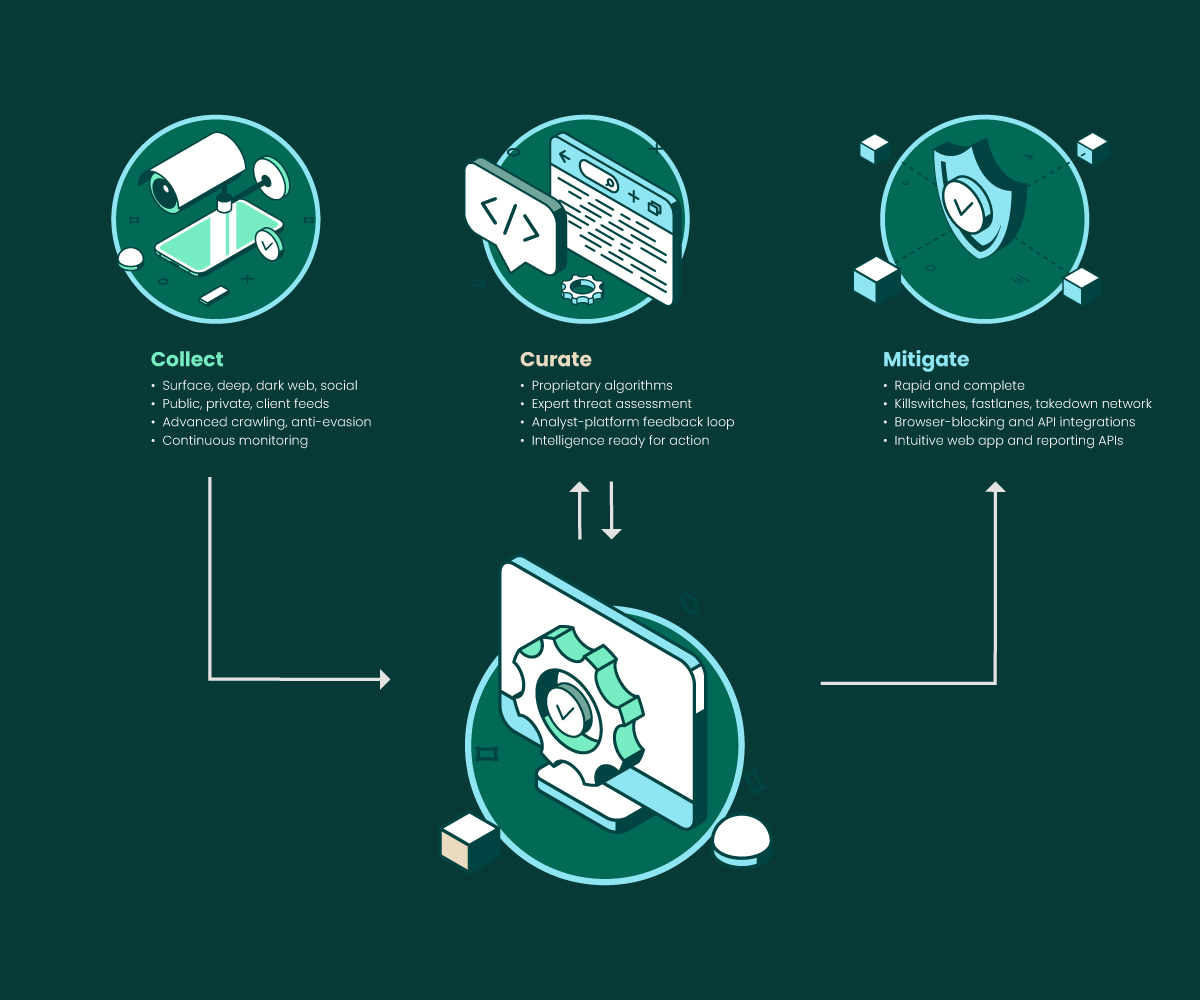
1. Collect
Effective threat visibility starts with robust data collection. While free and paid data feeds offer value, they are often insufficient on their own. Direct collection is essential to achieve the depth of visibility needed to support most DRP use cases. This process can span thousands of sources across the digital risk landscape. Given the scale of DRP, a high level of automation is crucial. However, certain sources may still require manual collection. Ultimately, the most effective approach combines automation wherever possible with human expertise where necessary.
2. Curate
An effective threat collection process often produces a large volume of potential risks. Curation filters out the noise, highlights what’s most relevant to the organization, adds essential context, and assesses the level of risk. To curate at scale, automation is essential. Algorithms and machine processing help score threat relevance and prioritize items for review, while expert analysts provide deeper context and evaluate severity.
A successful DRP program hinges on a smooth transition from automated filtering to human analysis. In the early stages, many organizations struggle with the volume of threats requiring expert review. As a stopgap, they may prioritize only the highest-scoring threats, a strategy that risks overlooking serious issues. In contrast, mature DRP programs continuously refine their automated analysis using feedback from analysts, steadily improving accuracy. This ongoing optimization is essential for striking the right balance between efficiency and thorough threat detection.
3. Mitigate
Mitigation is the purpose of DRP. The intelligence gathered through collecting and curating holds no real business value unless it is used to actively reduce risk. The quality of these upstream processes directly impacts the effectiveness of mitigation. Complex external threats often consist of multiple components, all of which must be identified and addressed to truly neutralize the risk. In many cases, being able to effectively mitigate also requires gathering evidence to support action by service providers or legal authorities. In this stage, the focus should be on two areas:
- Removing the threat from the infrastructure or platform it lives on. This is often referred to as performing takedowns.
- Blocking access to the threat. This limits the potential impact.
Performing domain takedowns is often the most difficult and time-consuming part of DRP. Different types of threats require different procedures, and there is no uniform global process across platforms, registrars, hosters, or other service providers. Most enterprises lack the local expertise and established relationships needed to efficiently execute threat takedowns. Despite the challenges, takedown is a critical component of effective mitigation as it ensures the threat is fully neutralized. There is no substitute for this final step in the mitigation process.
To effectively mitigate a threat, organizations should supplement takedown efforts with measures that block access to the malicious content. For users within the enterprise, this can be done by adding threat indicators into security controls (such as firewalls) that can enforce blocking policies. Security teams can usually automate this through API integration between DRP platforms and other security tools. To block access to threats by users from outside the corporate network, malicious URLs and domains identified via DRP can be submitted to browser-blocking services including Google Safe Browsing and Microsoft SmartScreen. There is no guarantee the submission will be used by these services in a timely fashion, if at all.
Getting Started with DRP
DRP is a vital operational process that, when executed effectively, halts the damage caused by external threats. It supports a growing range of use cases that evolve alongside our increasing reliance on digital services and platforms beyond the traditional corporate network. DRP integrates collection, curation, and mitigation into a cohesive process. By uniting these capabilities, DRP empowers security teams to level the playing field and effectively counter external threats.
Ready to see digital risk protection in action? Schedule a demo with Fortra Brand Protection to discover how we can protect your organization against external threats.