The dark web is a haven of stolen goods and data, and limited visibility into activity targeting your brand leaves organizations at risk. Malicious behavior takes many forms, and a lack of understanding of what or how an asset is exposed on underground channels can lead to brand damage and financial loss.
Detecting stolen data on the dark web is challenging, as navigating volatile marketplaces is both technical and time-consuming. To effectively protect against abuse targeting your organization, security teams should prioritize dark web threat intelligence including understanding of the types of threats relevant to your brand and where they live.
The most common dark web threats targeting the retail space include:
- Gift Cards/Rewards/Promotions Fraud
- Account Credentials
- Consumer Goods/Counterfeit Goods
- Refund Services
In the previous piece in this series, we focused on promotions fraud and account credentials targeting retail organizations on the dark web. In this blog, we take a look at real examples of consumer/counterfeit goods and refund services found on underground channels.
Consumer Goods/Counterfeit Goods
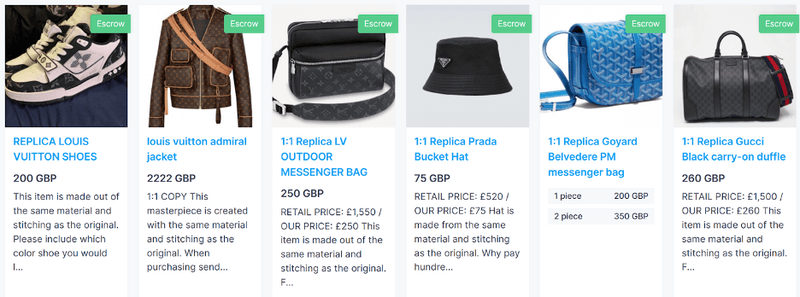
Counterfeit consumer goods are common across dark web marketplaces, where entire sections are devoted to replicas of clothing, shoes, jewelry, electronics, and other high-value items.
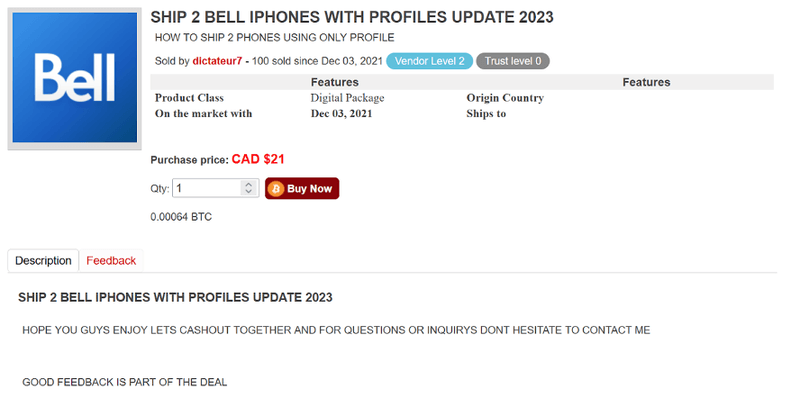
These marketplaces also often include guides or methods on how to obtain goods for a small fee. In the image below, threat actor “dictateur7” is selling guides/methods that will allow the buyer to ship two Bell iPhones to their location.
Refund Services
There are many dark web forums solely dedicated to refund services. These services include mentorship programs, documents, and virtual trainings. The examples below show refund mentorship services offered for $200+ specifically targeting Nike, Adidas, and Target.
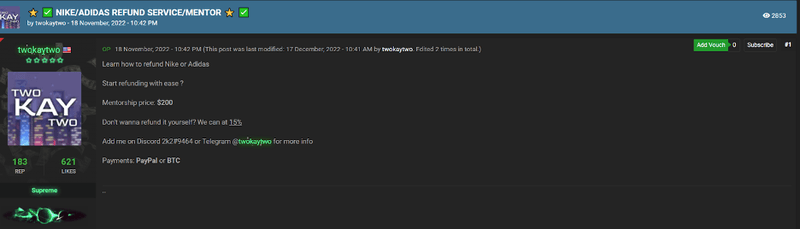
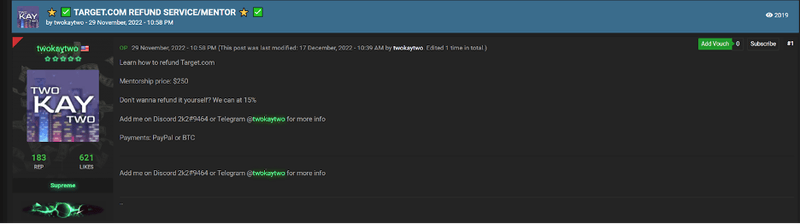
Threat actors use models similar to ransomware-as-a-service or phishing-as-a-service in the refund environment. In these operations, potential customers typically reach out to threat actors through dark web forums to perform the refund fraud on their behalf. After services have been rendered the threat actor will take a percentage of the refund or a set amount as payment.
In the image below, the threat actor “Fullex” has set guidelines on the various limits of the refund and the payment needed to perform the scam.
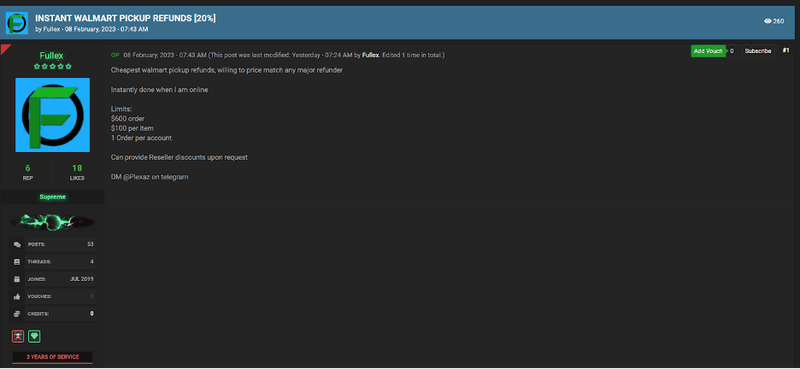
Below is an example of a post within Telegram of how a popular refund service operates for Amazon.com.de refunds.

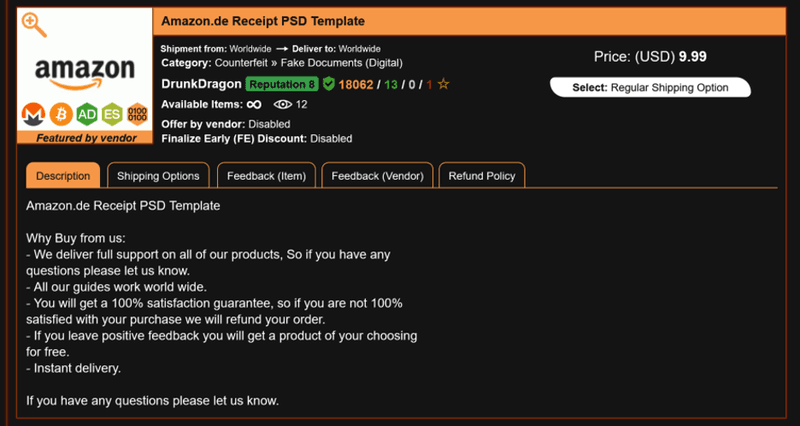
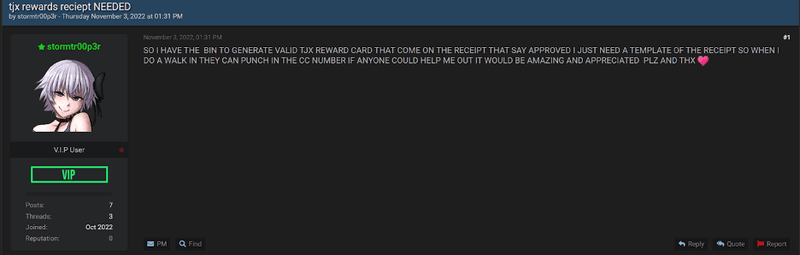
On traditional dark web marketplaces, it is common to see sections of the market dedicated to editable templates used to create document-based fraud. One example of this is an editable receipt template such as the one below. These templates are usually low in cost for potential buyers.
Threat actors exploit the dark web to buy, sell, and trade stolen retail data. Hidden marketplaces and forums make detection challenging, leaving organizations blind to emerging threats. Without timely dark web intelligence, businesses risk costly attacks. Security teams must understand the threats targeting their brand and actively monitor underground channels for signs of compromised data or criminal activity.
