Threat actors exploit the dark web to trade stolen data and illicit goods anonymously, often without the victim organization’s awareness. Malicious activity takes many forms across underground channels, but the technical barriers to accessing the dark web limit visibility — making it challenging to identify which assets may be exposed.
If sensitive information is undetected on the dark web, businesses risk brand damage and monetary loss. Organizations must identify the dark web threats most relevant to them and actively monitor underground channels to detect and respond to brand-related activity before it escalates. The most common threats targeting the retail space on the dark web include:
- Gift cards/rewards/promotions fraud
- Account credentials
- Consumer goods/counterfeit goods
- Refund services
In this two-part series, we address these threat types and provide examples of real examples found on dark web platforms. Below, we highlight promotions fraud and account credentials targeting retail brands on the dark web.
Gift Cards, Rewards & Promotions Fraud
Fraudulent gift cards and rewards are a common commodity on the dark web. Bad actors favor these promotions because they’re easier to exploit, with far fewer safeguards than credit or debit cards.
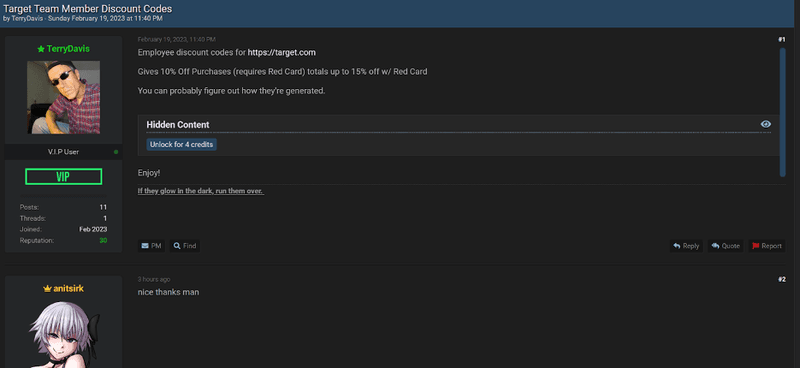
Fraudsters acquire gift cards two ways: by buying stolen, legitimately issued cards from complicit employees and by purchasing counterfeit cards produced by other criminals. Underground forums also host threads for gift-card generators and collections of card configuration data, making large-scale abuse easier to organize. Following are common examples of gift card configuration collections, gift cards, and team member discounts for sale.
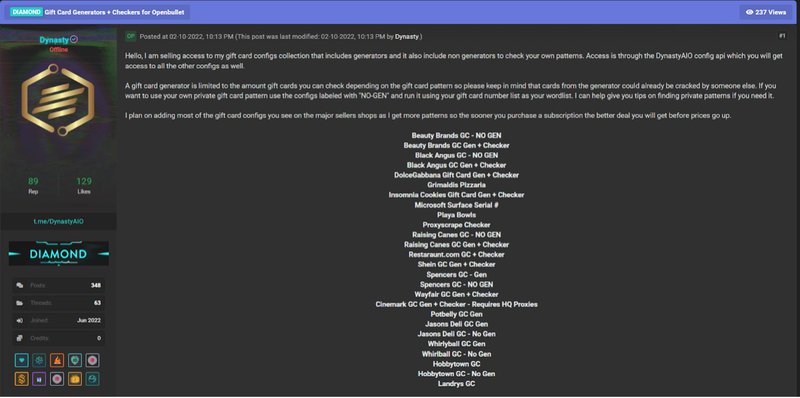
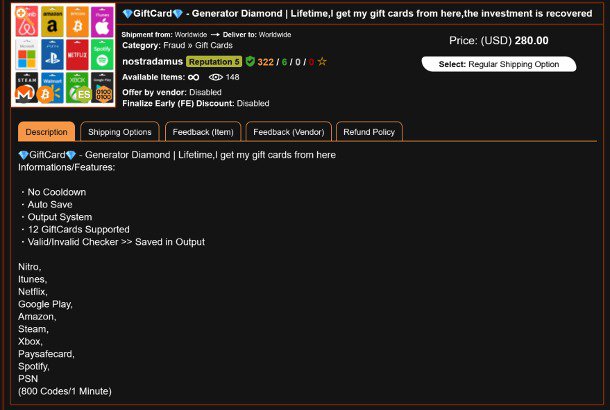
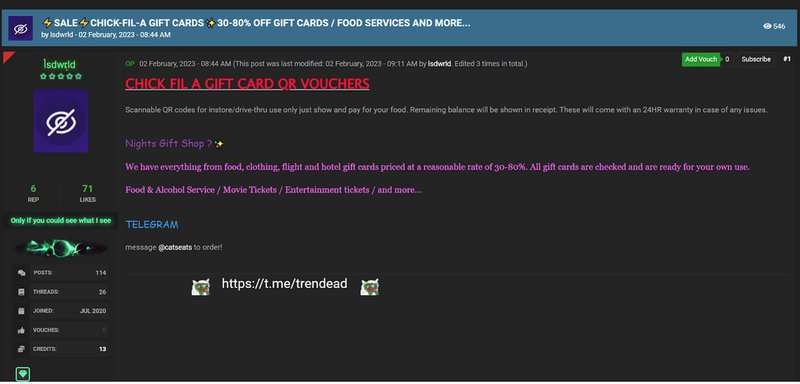
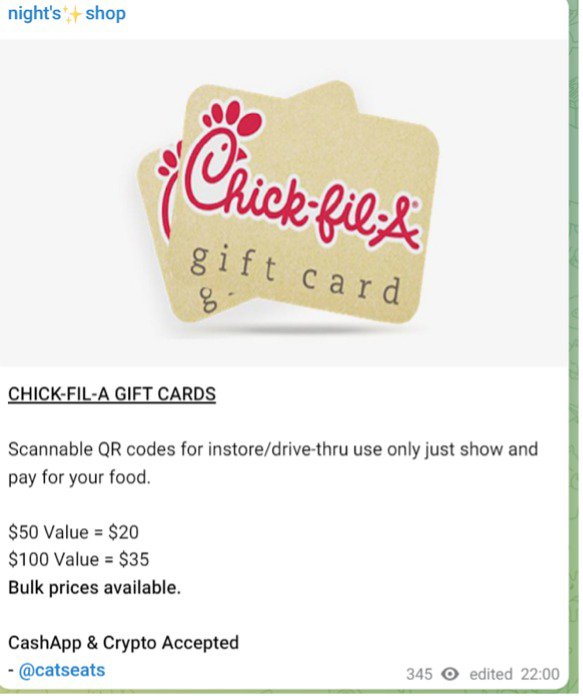
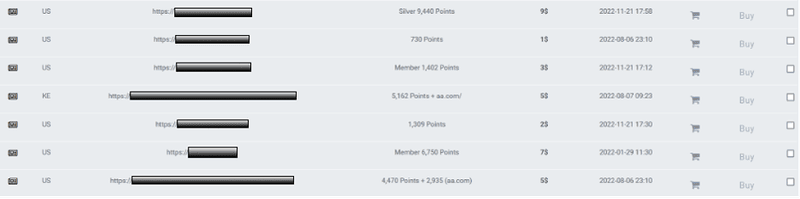
Content targeting rewards programs for the airline and hotel industry are highly sought after on account-based marketplaces on the dark web. The examples below have various points attached to the accounts. The threat actor has added print screens (now redacted) to show that the accounts are legitimate, and the logins captured are active/working. Airline accounts with status are also popular with buyers.
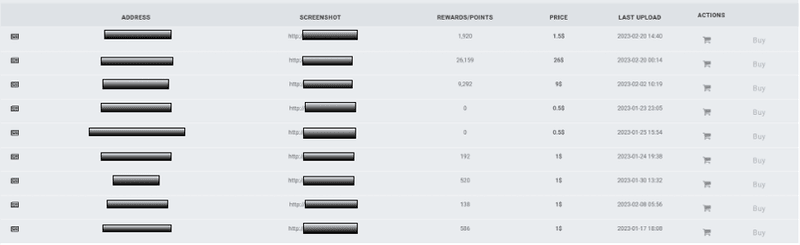
Account Credentials
Marketplaces that specialize in the sale of account credentials made up nearly 20% of Dark Web activity in Q4 2023. These marketplaces are in steady supply of newly compromised data often sold for minimal fees. Security teams must closely monitor credential marketplaces, where varying levels of consumer PII are often exposed. Early detection in these forums helps identify compromised customer data before it’s purchased and circulated further.
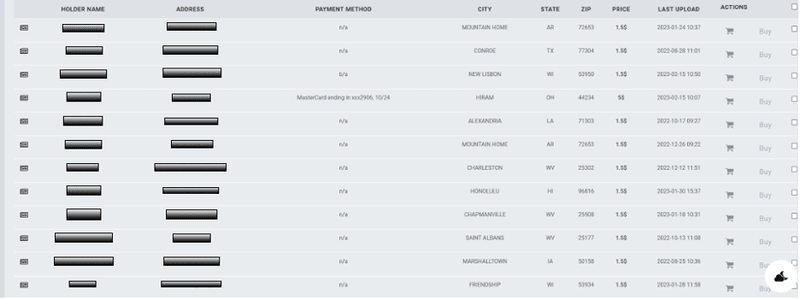
Following are examples of holder names and address information of Home Depot and Kohls customers on credential marketplaces.
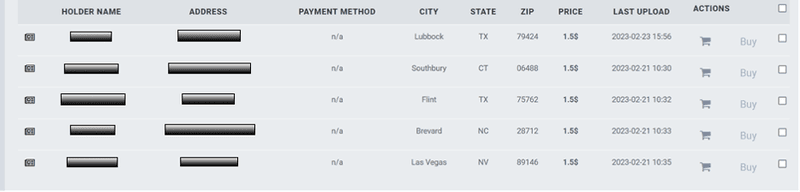
Marketplaces that specialize in the sale of retail-based account information are common. The image below is a typical example of a vendor selling Sephora accounts with linked credit card credentials, as well as Sephora accounts with reward points attached. Similar to traditional account-based marketplaces, these accounts can be purchased for a small fee.

Free data dumps of customer data and alleged insider access to organizations are also readily available within account marketplaces.
The screenshot below shows both Kohls and Target employee logins being sold over a popular dark web hacking forum.
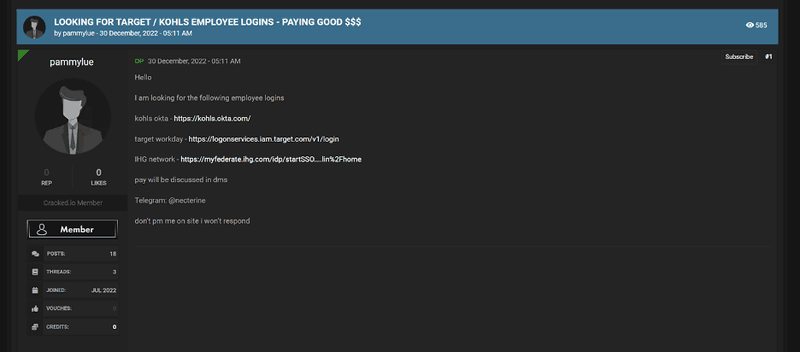
Cybercriminals exploit the dark web to trade stolen or falsified assets tied to legitimate retail brands. Because marketplaces and communication channels constantly shift and remain hidden, tracking this activity is difficult. Left unchecked, compromised data can fuel targeted attacks against both enterprises and their customers. Protecting against these risks requires a clear understanding of dark web threats and continuous monitoring of the underground sources where they surface.
