Domain impersonation underpins a wide range of online threats. Its dynamic nature makes it difficult for security teams to predict when and how a domain will be weaponized, requiring continuous monitoring to identify malicious behavior and justify takedown efforts.
In this Domain Impersonation Report, we analyze incidents involving look-alike domains to uncover the volume and most common types of threats targeting brands.
In this report, readers will learn:
- The average number of look-alike domains observed per brand, per month
- How look-alike domains are being used to target brands
- Common email display name spoofing techniques
- The most abused Top-Level Domains
Introduction
In the first half of 2023, the average brand was targeted by nearly 40 lookalike domains every month. Domain impersonation is involved in a vast number of online threats. Once a look-alike domain has been created, it may be used to host branded content, redirect to third parties, engage in malicious activities and more.
The domain landscape as a whole has been tumultuous so far in 2023. In Q1, top-level domain (TLDs) registrations tied to domain registry provider Freenom were halted, directly contributing to an 80% quarter over quarter decrease of free registrations tied to phishing attacks. While a large number of cybercriminals have since shifted to paying to register lookalike domains, the volume of country-code TLD (ccTLD) abuse remains high. In fact, for the first time since reporting on domain data, Fortra saw cybercriminals favoring ccTLDs over Legacy TLDs in Q2. What’s more, eight new Google TLDs were introduced to the domain pool in May, with newcomer .ZIP already associated with both credential theft and phishing redirect campaigns.
Domain records can be altered at any point in a domain’s lifecycle, making it difficult for security teams to detect threats early and collect actionable evidence for mitigation. This report leverages data from Fortra Brand Protection and Fortra DMARC Protection to examine the average volume of look-alike domains targeting brands in 2023 and the types of malicious content they hosted. The goal is to give security professionals a clearer picture of how look-alike domains are weaponized in cyberattacks.
For the purposes of this analysis, a look-alike domain is defined as a domain name that closely resembles a registered trademark or service mark. A brand refers to the name of a company, product, or service, and may appear across multiple domains, both legitimate and fraudulent.

Key Findings:
In the first half of the year, brands were targeted by an average of 40 lookalike domains per month.
77% of these domains were classified as malicious, with the majority hosting phishing sites.
Abuse of country-code top-level domains (ccTLDs) surged in Q2, accounting for 46% of all domain abuse, outpacing both legacy and new TLDs.
Over 62% of spoofed email display names impersonated high-profile brands, with Microsoft and Google among the most commonly abused.
Look-alike Domain Volume
Average look-alike domain per brand
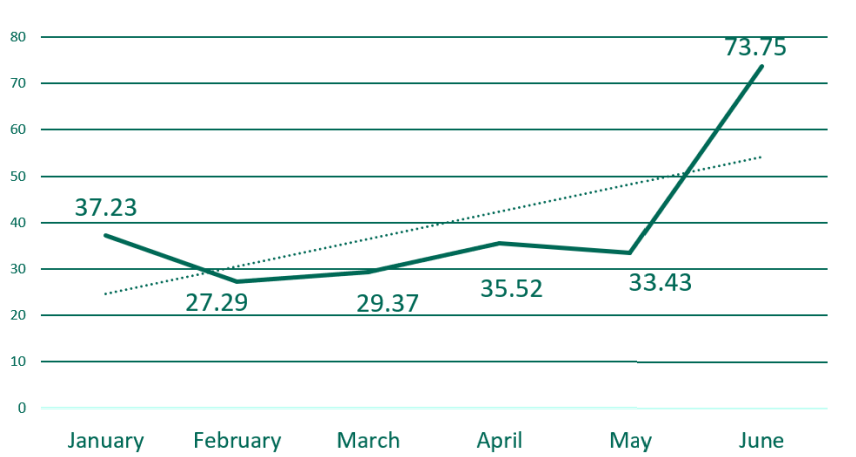
In the first half of 2023, the average brand was targeted by 39.4 look-alike domains per month, with volumes steadily increasing throughout the period. From January through May, monthly impersonation ranged between 27 and 37 domains per brand. However, in June, the volume spiked by more than 120%, with the average brand targeted by 73.75 look-alike domains.
This surge was largely driven by increased targeting of the technology, retail, manufacturing, and financial sectors, including a sharp rise in attacks impersonating a top three webmail provider. February recorded the lowest activity, with an average of 27.29 look-alike domains per brand.
How look-alike domains fuel cyberattacks
Look-alike domains can be leveraged in various ways to target a brand. In this report, we classify the types of content hosted on these domains into four distinct categories:
No Relevant Content: Parked domains, monetized links, unavailable content, or domains with no active content.
Branded Content: Domains displaying content related to the organization, including logos or industry-specific information.
Redirects: Domains that redirect visitors to third-party or competitor websites.
Malicious: Domains hosting phishing pages, counterfeit goods, cryptocurrency scams, or malware.
In the first half of 2023, 86% of look-alike domains fell into the No Relevant Content category. While these domains often mimic brand attributes, they typically do not host harmful content and may only serve advertisements. However, it’s important to recognize that domain content can change at any time, potentially escalating the threat and necessitating timely mitigation.
Top Look-alike Domain Threat Types
Branded content, redirects, and malicious content represent the three primary threat categories hosted by look-alike domains. In the first half of 2023, the majority of these domains — 53.4% — hosted branded content that mimics legitimate organizations. Redirects were the second most common tactic, accounting for just over 36% of threat volume by sending users to third-party or competitor websites. Malicious activity, including phishing and malware, comprised 10.3% of the look-alike domain landscape.

Below are examples of each category.
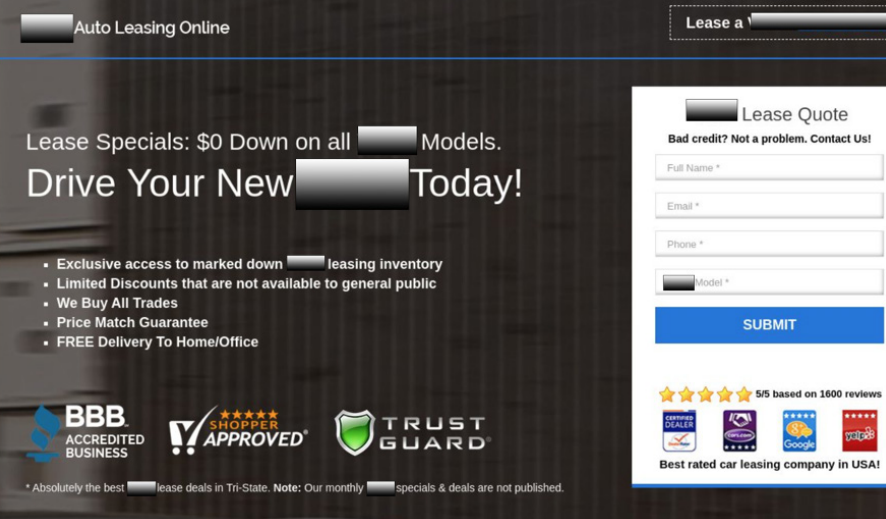
Branded Content targeting a global automotive manufacturer
Look-alike domain redirecting to an email provider

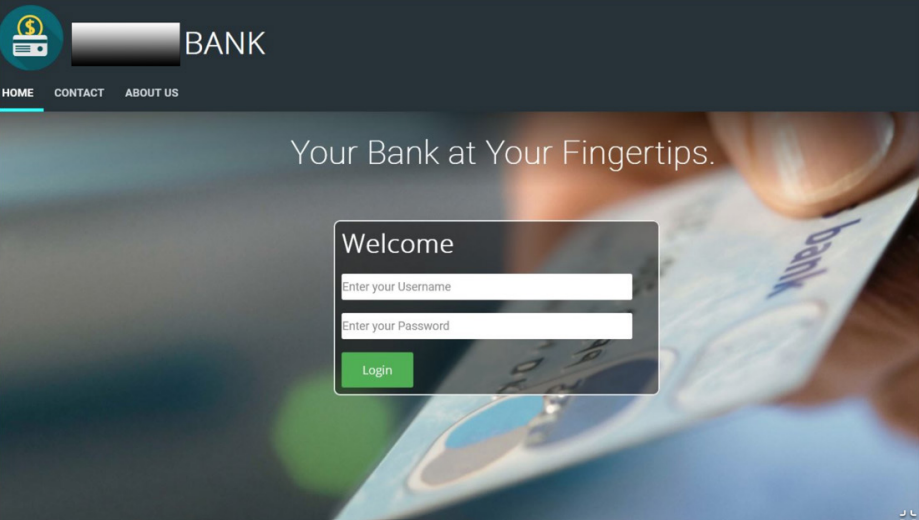
Look-alike domain hosting phishing content
Malicious Content
Fortra categorizes malicious content hosted on look-alike domains into four main types:
Phishing content
Cryptocurrency scams
Counterfeit Sites
Malicious activity, including potential malware distribution
In the first half of 2023, phishing accounted for the vast majority of malicious content, representing over 75% of activity in this category. Cryptocurrency scams were the second most prevalent, making up just over 17%. Counterfeit sites contributed a smaller portion, at 4.4%, while malware-related malicious activity was the least common, at 1.4%.

Top-Level Domain Abuse
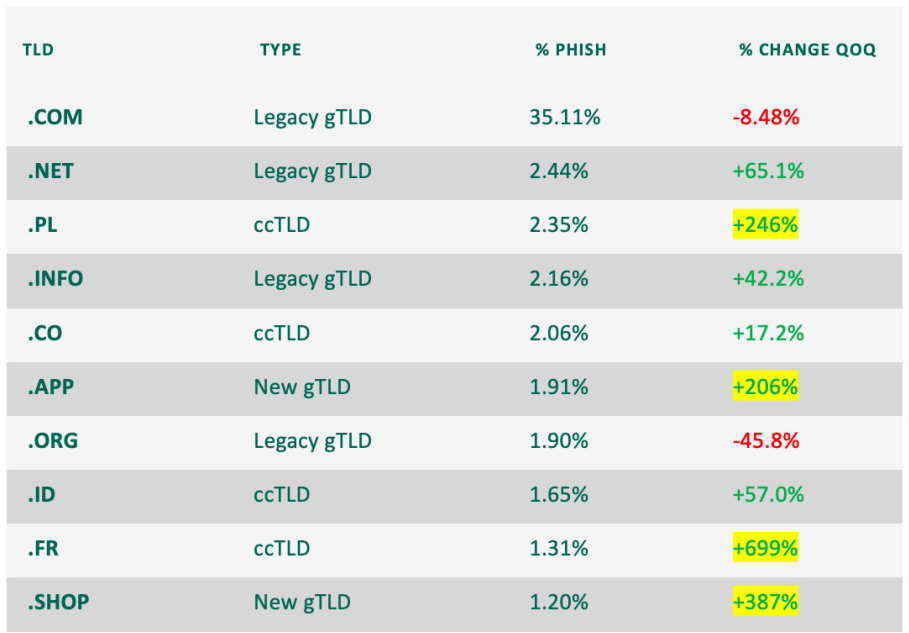
The top-level domains used in phishing campaigns fluctuated widely in H1. While TLD abuse can be inconsistent from quarter to quarter, the first half of 2023 saw a move away from commonly seen free registration providers, to new and paid TLDs within the top 10.
In Q2, half of the top 10 abused TLDs were new to the group, with many seeing dramatic changes in volume. Notably, multiple TLDs within the top ten are clearly capable of misleading targets if used in conjunction with a brand or industry-related URL. New gTLDs .APP and .SHOP are two examples of TLDs demonstrating large jumps in abuse that, if used in phishing attacks, would be ideal choices in targeting a technology company or retail brand.
Taking a look at TLD types, for the first time since reporting on TLD data, ccTLDs made up the majority of abuse, with nearly 46% of overall volume. The ccTLDs among the top 10 were .PL, .CO, .ID and .FR. While all four ccTLDs showed a quarter over quarter increase from Q1, .PL and .FR jumped considerably, with .PR growing nearly 250% and .FR a sizable 700%.
Legacy gTLDs were abused 18.5% less than they were in Q1, making up 41.7% of volume. While Legacy gTLD .COM declined 8.5% over Q1, it remained the most abused TLD over all others. Legacy TLD .ORG also saw a decline, moving from the second spot in Q1 to the 7th in Q2.
New TLDs contributed to just over 12% of abuse in Q2, with .APP and .SHOP jump to the sixth and tenth spots, respectively. This is due to a 206% quarter over quarter increase for New TLD .APP and 387% increase in .SHOP.
While insignificant in volume, newly released Google TLDs .ZIP and .DAD were detected hosting phishing content in June, with two known incidents attributed to .ZIP in Q2 and eighteen associated with .DAD.
Email Domain Spoofing - Imposter Type
In addition to look-alike domains, cybercriminals also forge email sender addresses without actually registering the impersonated domain, otherwise known as domain spoofing. In domain spoofing attacks the brand is not impersonated by the domain itself, but rather the display name.
The most three most common domain spoofing types are:
- Brand display name imposter - The email address is irrelevant. The attacker is relying on the fact that most mail clients only display the name portion of the From: header to impersonate a well-known brand.
- Look-alike domain - The attacker uses an email domain that is similar to the actual domain of the organization they are trying to impersonate.
- Individual display name imposter - The email address is irrelevant. The attacker is relying on the fact that most mail clients only display the name portion of the From: header to impersonate an individual.
In this report, we took a look at the volume of email spoofing attacks during the last month of Q2. At this time, display names impersonating a well-known brand such as Microsoft or Google made up 62.36% of attacks.
More than 34% of domain spoofing attacks were manipulated to appear as though they came from a specific individual such as a member of a corporate team or third-party vendor.

Final Thoughts
Domain impersonation is a critical factor in the success of many online threats. Understanding how look-alike domains appear and the types of content they host is essential for early detection and swift removal.
In the first half of 2023, the average brand faced 40 look-alike domain attacks per month, with numbers trending upward as the year progresses. The most common use of these domains was hosting Branded Content, often displaying brand logos or related industry material.
Malicious content appeared on look-alike domains over 10% of the time during this period, with phishing accounting for the majority of attacks. Cryptocurrency scams followed, representing just over 17% of malicious activity.
In Q2, several new top-level domains (TLDs) entered the top ten due to spikes in abuse, with some New and country-code TLDs (ccTLDs) doubling or tripling in volume. For the first time, ccTLDs accounted for 46% of overall look-alike domain activity, surpassing legacy and new TLDs.
When launching email attacks, cybercriminals most often impersonated well-known brand names, with over 62% of spoofed display names mimicking recognized brands. High-ranking individuals and third-party vendors were the second most impersonated, accounting for 34.4% of attacks.
Because domains can be altered at any time during their lifecycle, continuous visibility into their behavior is vital to spotting suspicious activity and eliminating threats. To effectively minimize risk, security teams must proactively monitor for new and suspicious domains and gather evidence to support rapid takedown efforts.
Don’t Be Fooled: Spot and Stop Domain Look-Alike Threats
Fortra provides advanced solutions to safeguard your brand against domain impersonation and look-alike threats.