Cybercriminals routinely exploit legitimate websites to host malicious content—from phishing pages and exploit kits to redirect links and malware loaders. These compromised sites are essential to cybercrime operations for two key reasons:
They’re abundant. Countless insecure websites across the internet provide easy targets.
They’re trusted. Recently compromised legitimate domains are less likely to be flagged or blacklisted by browsers and security tools, allowing malicious campaigns to operate longer undetected.
A common attack vector? File upload functionality.
Many websites — from blogs and social platforms to e-commerce and file-sharing services — rely on user-generated content to operate. But features like comment forms, support ticket uploads, or media submission fields create opportunities for attackers.
Even when basic security measures are in place to block certain file types, cybercriminals often bypass them by exploiting vulnerable web applications that lack proper input validation or sanitize uploads improperly. Once in, they can plant malicious scripts, backdoors, or redirect links directly onto trusted domains.
The GIF89a exploit is a good example of this. It allows an attacker to disguise any file as an image/gif file and upload it to a webserver. The exploit works by taking advantage of weak file type validation. The header of the file to be uploaded is changed to include GIF89a in order to bypass a security measure put in place barring the uploading of non-image files (see Figure 1).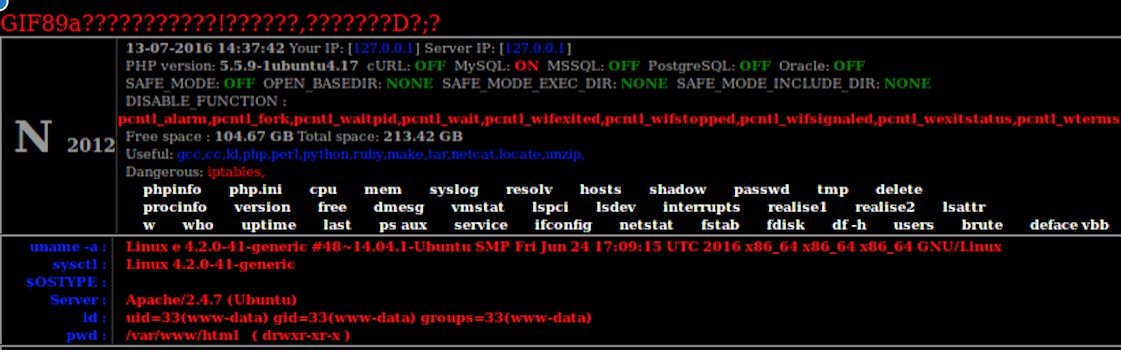
Figure 1 - Screenshot of GIF89a header manipulation
When the file is uploaded, the system checks the MIME type for a match. When the match is confirmed, the system uploads what it identified as an acceptable GIF file to the server. Once on the server, the system then runs any code hidden in the file, often by default. Attackers often use this exploit to trick the server into executing a PHP webshell that can be remotely accessed. This allows the attacker to then upload files to the compromised server or execute commands based on the type of access granted by the server permissions. This gives the attacker the ability to upload phish kits, malware, or any other content that they wish. Depending on the file permissions granted by the server, they may be able take over the server entirely.
The GIF89a exploit is neither new nor sophisticated, but it continues to be used successfully for a variety of reasons. Server administrators are failing to apply updates and patches promptly, choosing to blacklist file types instead of creating whitelists, enabling functions which aren’t required, and not setting file permissions appropriately. Simply put, basic operational security is not being implemented or maintained.
Key steps website administrators can take to prevent exploits:
Keep systems updated. Regularly patch known vulnerabilities in your CMS, plugins, and server software.
Use file whitelisting. Allow only approved file types instead of trying to block malicious ones—everything not on the list should be rejected.
Enforce least privilege. Set file and user permissions to the minimum required for functionality; never grant unnecessary access.
Limit access scope. Restrict users and processes from reaching resources they don’t explicitly need.
Be cautious with permissions. Avoid changing default file permissions without fully understanding the security consequences.
Reduce the attack surface. Disable unused services, features, or tools to limit potential entry points.
Avoid risky add-ons. Don’t use outdated or unverified plugins, themes, or extensions—they’re common targets for attackers.
Protecting your web presence is critical in today’s threat landscape. Fortra Brand Protection provides the advanced monitoring and expert intelligence needed to detect, disrupt, and prevent website compromises before they damage your brand. Don’t wait for attackers to strike — learn how Fortra can safeguard your digital assets today.