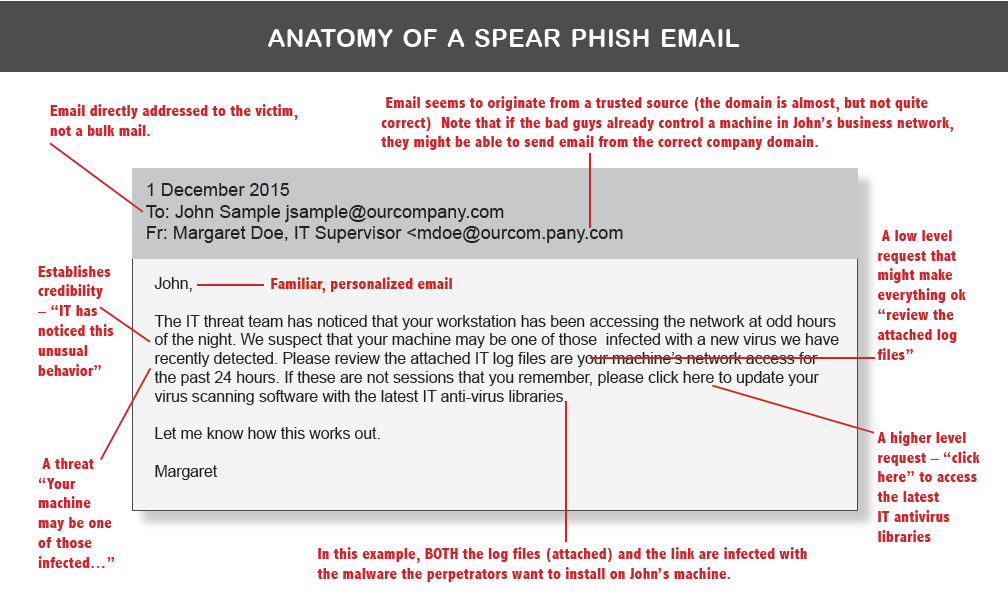
Spear phishing is one of the most dangerous forms of email-based cyberattacks. Unlike broad phishing campaigns sent to thousands of recipients, spear phishing is highly targeted. Each email is custom-crafted, often using detailed personal information, to deceive a specific individual.
These attacks are convincing because they feel personal. Threat actors often spend hours researching their target, learning names, job roles, recent projects, and even nicknames. The resulting email seems familiar, credible, and trustworthy, lowering your defenses and increasing the likelihood of engagement.
What Makes a Spear Phish So Effective?
1. It Feels Personal: Spear phishing emails don’t use generic greetings. Instead of “Dear Sir or Madam,” you’ll likely see “Hi Eliza” or even something more casual, like “Hey Liz.” They might reference specific colleagues, initiatives, or events to increase their legitimacy.
2. It Appears to Be from Someone You Know: Attackers often spoof or slightly alter familiar email addresses (e.g., [email protected] instead of [email protected]). In more advanced cases, they may compromise real accounts to send emails from legitimate addresses—making detection even harder.
3. It’s Backed by Research: The attacker may reference actual work-related topics, projects, or people:
“Eliza—Henry and I just finished the first draft of our guide on Iberian Meteorology. Can you give it a quick review? I’ll call you later today.” This makes the message feel natural and trustworthy, especially if you are indeed working on something similar.
4. It Makes a Reasonable Request: Spear phishing messages typically ask you to perform a small, seemingly harmless action such as clicking a link, opening an attachment, or reviewing a document. That action, however, may install malware, steal credentials, or open the door to larger breaches, including financial fraud or data theft.
5. It Exploits Trust and Authority: The email might appear to come from a manager, executive, or even a close friend. Because of the sender’s perceived authority or familiarity, you’re more likely to follow through — no questions asked.
5 Steps to Reduce Your Risk
- Pause Before You Click: If an email asks you to open an attachment or click a link, slow down and assess its legitimacy.
- Verify the Sender: Look closely at the email address and domain. Small differences can be easy to overlook but are a common red flag.
- Ask the Right Questions: Would this person really ask me to do this? Does it make sense given our relationship and context?
- Confirm Outside the Inbox: If you’re unsure, contact the sender using a different channel (phone, text, chat)—never by replying to the suspicious email.
- Keep Security Software Up to Date: Modern antivirus and email protection tools help flag malicious links and attachments. Ensure your systems are current and properly configured.
Stay Vigilant
A well-crafted spear phishing attack can fool even the most seasoned professionals. It leverages familiarity, trust, and context to lower your guard. But with awareness and caution, you can protect yourself and your organization from these highly targeted threats.
When in doubt, don’t click. Don’t respond. Verify first.