Email impersonation is the fastest growing and most successful means of bypassing email security controls. In Q4 2022, the response-based and credential theft attacks that make up email impersonation reached their highest percentage of share of all email threat volume, contributing to more than 97% of attacks reported by end users. In this series, we look at the top email impersonation threats based on the reported volume in user inboxes through our SEA solution. Below, we focus on business email compromise (BEC), common tactics, and real attacks associated with the highest volume campaigns in 2023.
BEC by the Numbers
The threat types that encompass email impersonation can be damaging regardless of quantity or classification. Within the group, the category considered most costly to organizations is BEC. According to the FBI’s Internet Crime Report, losses associated with BEC topped 2.7 billion in 2022. BEC attacks are particularly damaging because they target employees with financially-driven requests from false authority figures or partner vendors. BEC attacks reported in end user inboxes grew more than 43% from 2021 - 2022, indicating an increased interest by threat actors in an already popular means of manipulation. The content within a BEC email is constructed to look unassuming and includes spoofed materials to enhance its legitimacy. As with other email impersonation attacks, BEC instances lack malicious indicators that would typically flag traditional security controls.
BEC Campaign 1
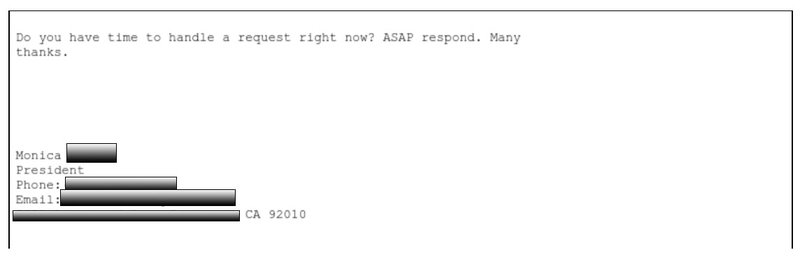
Email subject: RE: URGENT! Sender: [email protected]
Display Name: Monica [Redacted]
One of the largest BEC campaigns reported by end users in 2023 targeted a global retailer just after the new year. In the attack, the cybercriminal spoofs the display name of a legitimate, now expired domain, marketsneakers.com. This attack bypassed the targeted organization’s Secure Email Gateway (SEG) with a Microsoft Spam Confidence Level (SCL) of 1, indicating the message was safe. Threat actors abuse domains via display names, exact spoofing, and by creating lookalikes. Display name deception is the most common form of abuse and involves changing the display value on an email to show a trusted individual or brand. This is cheap and often successful, as the display name may be the only sender information visible to the victim. Email spoofing takes place when a cybercriminal uses the exact email address of the individual or brand they are impersonating. While it is possible for this tactic to exploit some email protocols, email spoofing can be identified through email authentication standards such as DMARC. A threat actor may also register a lookalike domain that relies on homoglyphs or characters to impersonate the legitimate domain, such as travelbo0kings.com versus travelbookings.com. The intent of lookalike domains is to trick the email recipient, as email authentication will not usually flag these as malicious.
BEC Campaign 2

Email Subject: TREAT URGENTLY
Sender: [email protected]
Another large BEC campaign targeted a national financial institution in mid-February. The email subject closely mirrors the first example and is a good representation of how BEC subject lines use common, persuasive language to inspire urgency. This attack also bypassed the targeted organization’s SEG with a SCL of 1. The sender address originated from a Google webmail account. Google is the most abused free webmail provider and contributed to nearly 68% of BEC reports in February 2023. Free webmail accounts represent significantly more BEC campaigns than attacker controlled, as no-cost infrastructures require less investment from cybercriminals.
BEC Campaign 3
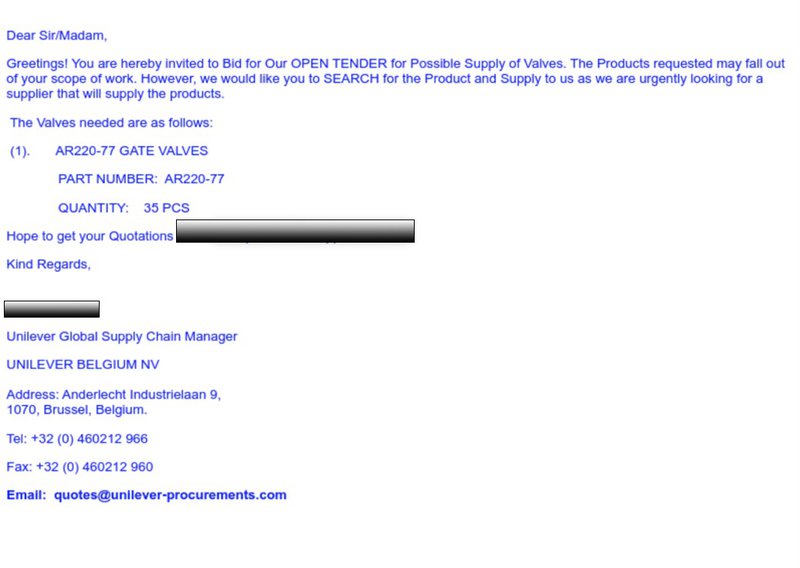
Subject: Request for Quotation
Reply To: [email protected]
The third BEC example targeted a multinational manufacturing organization with email impersonation of a third party vendor. Vendor impersonation, otherwise known as vendor email compromise (VEC) or a supply chain attack, is a common subset of BEC. Like the previous examples, this too was given a SCL score of 1. VEC messages are particularly difficult to identify because they incorporate lookalike domains or originate from compromised third-party accounts. If a network is compromised, VEC actors will spend time gathering intelligence on the victim and/or organization prior to launching their attack to make the message more targeted. Incorporating details characteristic of their victims allows the actor to request large sums of money or sensitive information without raising alarm. If the actor uses a legitimate email address from a compromised network, the attack will also pass domain authentication without suspicion.
Preventing BEC Attacks
Email impersonation attacks such as BEC are commonly referred to as advanced, however their methods do not rely on technical acumen. Instead, the success or failure of a BEC attack is determined by the bad actor’s ability to convince victims that they are someone else. This lack of malicious indicators and reliance instead on written and verbal communication renders traditional security controls ineffective. Identifying actual BEC threats among the countless number of legitimate messages should be approached the following ways.
Domain Monitoring and Implementation of DMARC
Security teams should proactively monitor for spoofed and lookalike domain registrations that could be used to launch attacks. Email authentication standards such as DMARC will prevent the exact spoofing of an organization’s domain and should be implemented. Identifying lookalike domains can be accomplished by monitoring the following:
- New domains
- Existing domains
- SSL certificate logs
- DNS Data
- Zone files
A malicious domain must be taken down completely in order to remove the threat. This can be done by submitting all evidence of abuse to the appropriate registrar.
Machine Learning
Because searching for signature matches will fail to flag email impersonation threats, security teams should use AI to model sender-receiver relationships and isolate the bad. This is done by mapping sender identities, adding context to their decisions, and authenticating who they communicate with. Creating a baseline of normal behavior will allow AI to detect anomalies and deviation from good, so that identity-based threats can be blocked at scale.
Analysis of Suspicious Emails
Processing suspicious emails requires both human insight and automated analysis. By combining these approaches, security teams can leverage critical threat intelligence to improve detection and disrupt ongoing campaigns. Suspicious Email Analysis includes removing false positives, adding contextual insights, and accurately classifying threats.
Email impersonation attacks, such as business email compromise (BEC), remain the most reported threats reaching user inboxes. These scams rely almost entirely on social engineering to commit fraud and access sensitive data. Because they often lack traditional indicators and exploit legitimate services, detection can be challenging.
To proactively defend against email impersonation attacks, security teams should:
Continuously monitor attacker infrastructure
Implement identity-based detection
Integrate intelligence from analysis into existing security controls
Stay ahead of BEC threats by turning insights into action and safeguarding your organization before attackers strike.
