Cyber-attacks targeting retail brands have increased dramatically over the last year. Since Q3 2021, retail has experienced a nearly 500% increase in attacks on social media alone. Counterfeit websites and look-alike domains are also among the top threats to online retailers. Attackers incorporate stolen designs and trademarks to stand up counterfeit sites, outbid legitimate businesses with fraudulent advertisements, and impersonate brands and their executives with bogus social media accounts.
Ecommerce sales are expected to exceed $7 trillion by 2025, and online buying behavior will be driven by the online relationships between consumer and brand. Protecting your digital presence is critical to the health of your organization. Below, we break down the top four online threats targeting retail brands.
Unauthorized Social Account Pages
In Q1, retail became the second most targeted industry on social media with attacks having skyrocketed nearly 500% since Q3 2021, according to our Quarterly Threat Trends & Intelligence Report.
The rise in social commerce has positioned retail brands’ social media presence as a key differentiator among competitors. A high level of engagement is critical to attracting and retaining customers, and misinformation or brand abuse related to a retail brand can have devastating consequences. Threat actors take advantage of this industry-wide investment in brand-building and consumer engagement via social platforms in a number of ways, including using brand abuse to create phony account pages. Brand abuse on social media encompasses the unauthorized use of copyrighted material, trademarks, and other IP to create fake account pages and advertisements.
From January to March, nearly 96% of all attacks targeting retail on social media used stolen copy or images to impersonate legitimate brand or executive accounts. The volume of unprotected data and ease of account creation makes mimicking account pages an undemanding operation for threat actors. Additionally, impersonation enhances the credibility of the fake site and aids in its ability to avoid detection.
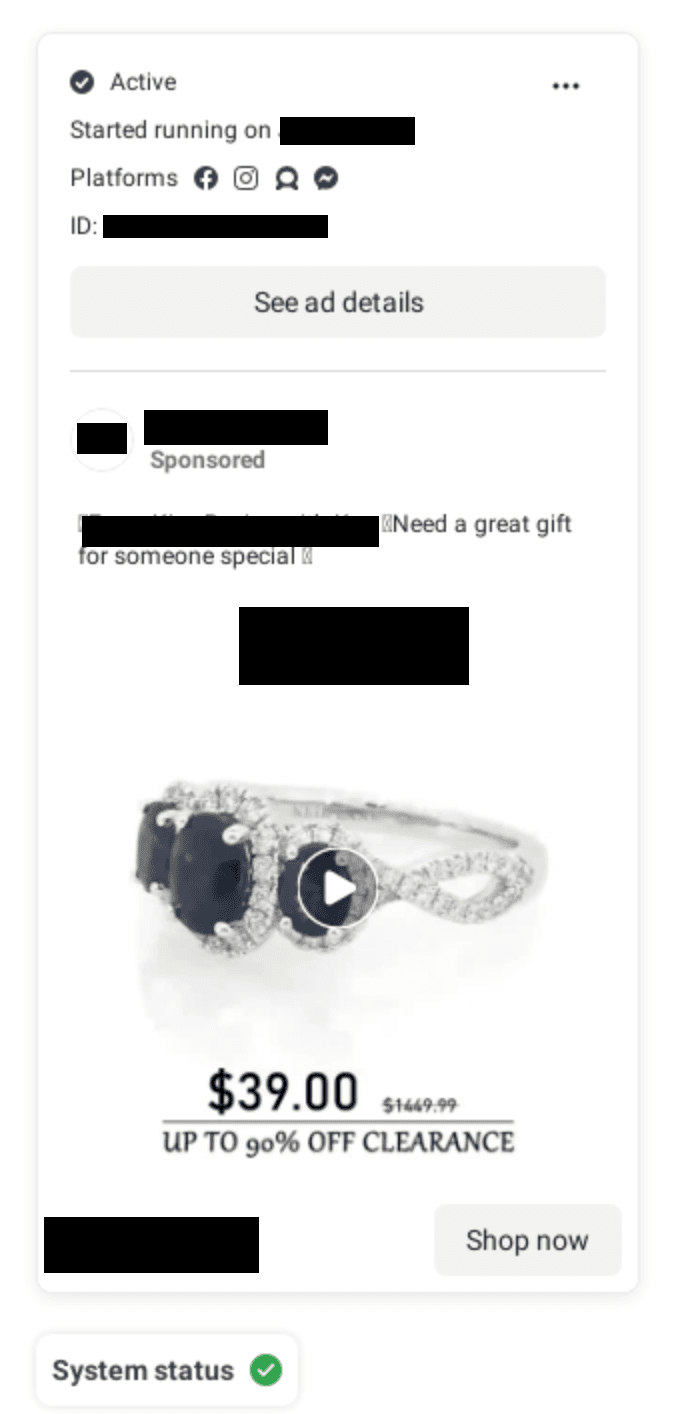
Fraudulent Ads
Sponsored advertisements on social media are increasingly responsible for promoting fake products, redirecting traffic to counterfeit websites, and driving ad prices for legitimate organizations. Sponsored ads are created via falsely branded business accounts using stolen copy, imagery, and a strong call to action such as a flash sale. Threat actors can tailor these ads to the audience of their choice and determine the budget and duration of their attack.
As fraudulent advertisements grow in popularity, retail brands are finding themselves forced to compete directly with criminals for advertising space. Fraudulent advertisements populated through Google search are also targeting retail on the open web. These malicious advertisements have a low-cost barrier to entry and abuse geofencing to target victims.
Broad social media monitoring is necessary to capture intelligence for accurate detection and takedown. Threats targeting retail on social media are difficult to identify because they are expert impersonators. Security teams should employ a wide range of sources including technology and expert human analysis to identify suspicious activity. Additionally, it is important to build strong relationships with social platforms to ensure the rapid remediation of confirmed threats.
Counterfeit Sites
Online storefronts driving counterfeit sales are targeting retail customers with stolen logos and imagery on the open web. These sites mimic reputable brands by using look-alike domains, misleading copy, and stolen intellectual property. Actors are also integrating trusted payment applications such as PayPal to conduct seemingly reputable transactions and enhance the site’s overall sense of legitimacy.
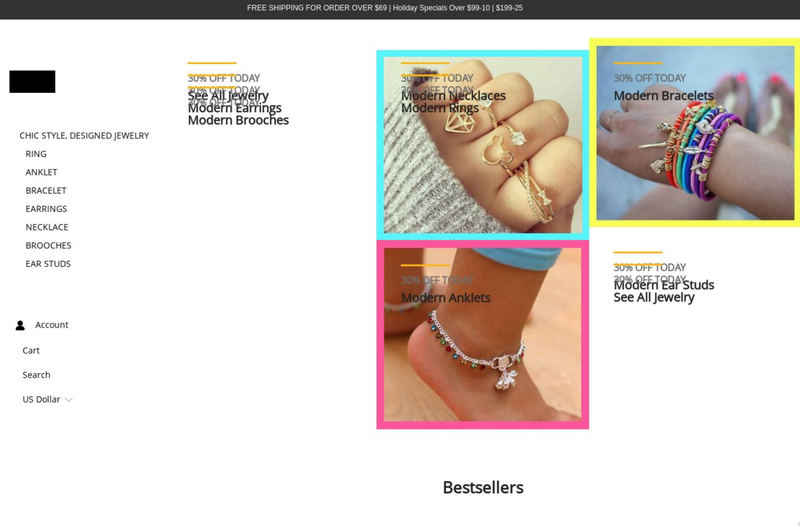
The unauthorized use of trademarked material on counterfeit sites may lead to brand damage far beyond frayed customer confidence. Cannibalized sales, operational costs, and inflated online advertising rates all affect a bottom-line equaling billions of dollars globally.
Email phishing lures and falsely branded pay-per-click lures on social media play a significant role in convincing victims they are interacting with a legitimate retail brand. Disrupting counterfeit activity requires sourcing intelligence through a combination of technology and human analysis across multiple channels. In order to detect and mitigate these threats, security teams should broadly monitor for the unauthorized use or impersonation of your brand in addition to building strong relationships with hosting providers, ISPs, and registrars.
Look-alike Domains
Malicious domains serve as the foundation for a wide range of threats targeting retail brands. Threat actors can easily stand up a look-alike domain, tailor it to their target, and launch a variety of campaigns including phishing emails, ads, and counterfeit websites.
Look-alike domains are incredibly effective because impersonating a legitimate brand allows them to leverage that brand’s reputation. Domains can impersonate a brand the following ways:
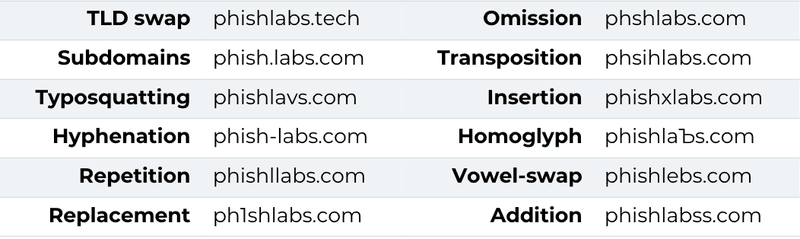
Attacks that use look-alike domains can lead to significant brand damage, financial loss, and data compromise. In order to protect against abuse, retail brands should implement comprehensive collection measures that source sufficient domain intelligence and give visibility into new and existing registered domains. Additionally, comprehensive curation through a combination of human and technological analysis should be used to identify real threats. Finally, security teams should prioritize understanding and supplying registries with the evidence needed to initiate swift takedown of a malicious domain.
Most retail brands are adopting an ecommerce-heavy business model, giving the consumer access to a direct relationship with the brand. Threat actors have the ability to compromise these relationships and cause lasting damage to a retail brand’s reputation. In order for a retail brand to succeed and survive online, it is essential that security teams prioritize proactive measures to identify and remediate threats most pertinent to their business.
Learn how Fortra Brand Protection can break the attack chain for your organization.
