Since early 2022, Fortra has been monitoring a significant ongoing upward trend in fraud activity originating from various Phishing-as-a-Service (PhaaS) operations. Some of these services have thrived, while the popularity of others has diminished. One PhaaS operation that has notably been present throughout is Strox (aka Strox.su or Strox Pages). Strox is one of the most complete phishing solutions for fraud actors available, offering advanced phishing kits, hosting services, mail spam scripts, and an automated market for selling stolen credentials.
Strox, which reportedly launched in June 2021, initially offered phishing kits impersonating 11 U.S. financial institutions. Retrospective analysis by Fortra traced Strox-linked phishing activity back to November 2021. Since its debut, the platform has added just one more brand to its kit library. However, its page customization feature enables threat actors to easily adapt templates to impersonate virtually any brand by modifying images and text.
Though much of Strox’s infrastructure is found on Russian-based bulletproof hosting services, the group most likely operates out of the Middle East. While communication from the threat group is typically kept professional, stray comments found in phishing files and telegram channels speak on politics within the region.
Phishing-as-a-Service Analysis
Phishing kits
Analysis of phishing pages linked to the Strox platform suggests that many, if not all, of its kits are not original creations. Instead, widely used phishing kits appear to be modified to include advanced live phishing features typical of a PhaaS operation. As a result, phishing URLs alone may not reliably indicate that Strox was the source of the attack.
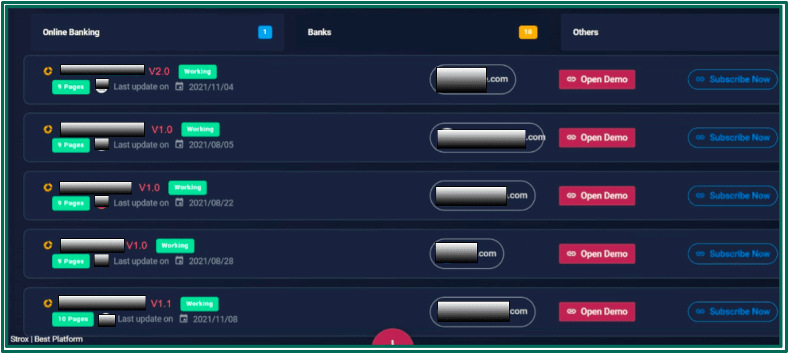
Twelve phishing kits are sold on Strox for $90 each. Each kit includes a unique API key that promises the buyer continued development and updates of the page content and antibot information. Customers can view demo phishing pages before buying them for use and may customize which pages are active when an attack is live. All available kits automatically translate phishing content to match the victim’s browser language, with the service claiming support for more than 230 languages.
Live phishing capabilities
All scam kits available from Strox include a real-time admin panel which allows the phisher to control and monitor their active attacks. Logging information on the pages provides a live look at the number of people currently looking at phishing content and the actions that are being taken. This functionality is also used in man-in-the-middle-style attacks to intercept two-factor authentication codes and bypass additional security measures. When threat actors are unavailable to actively monitor an attack, they may place phishing pages in a dormant state, reducing the risk of detection during periods of inactivity.
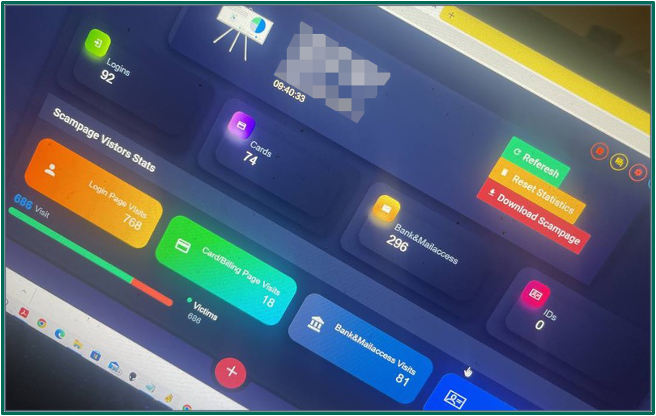
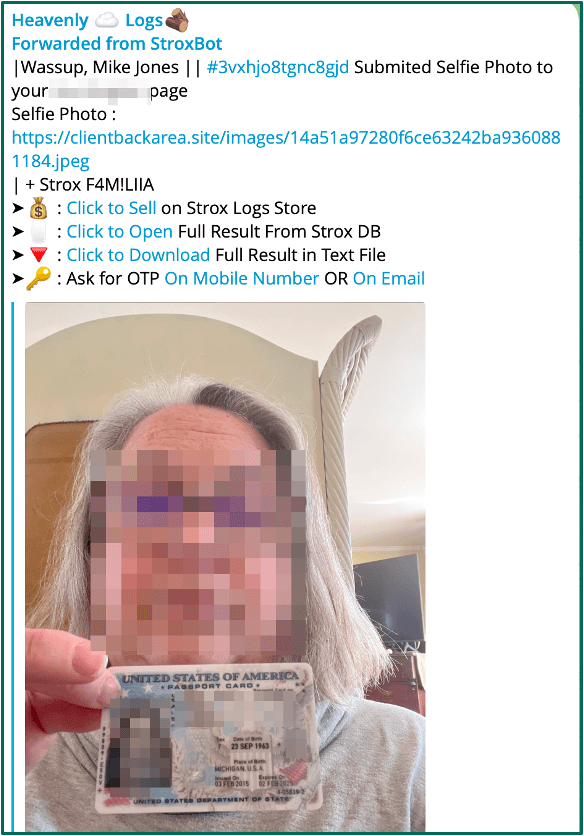
Strox phish exfiltrate stolen credentials through a centralized Telegram bot rather than through a drop email address. This Telegram API provides end-to-end encryption and has the capability to package up this personal information for sale as logs on a marketplace on Strox’s own domain. This makes Strox.su a potential complete closed ecosystem for threat actors, where captured banking information can be sold and the funds reused to purchase more phishing and hosting services within the Strox platform.

Server hosting
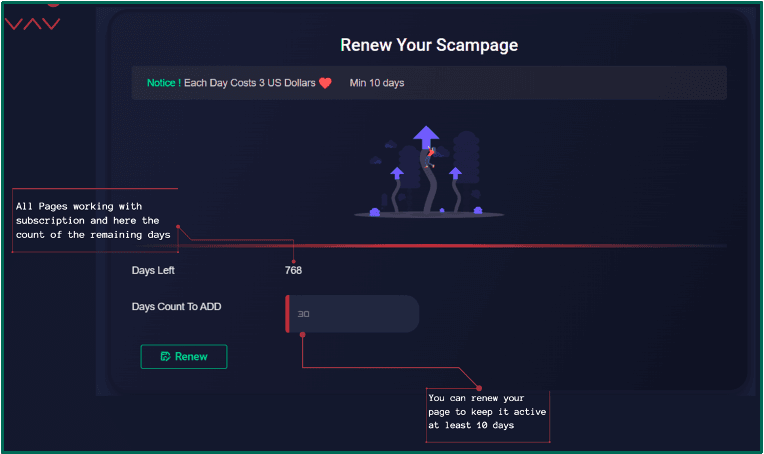
One factor that distinguishes Strox from many other popular PhaaS platforms is that the service offers to setup hosting infrastructure for the user. Bulletproof hosting of a cPanel installation is offered at a rate of $3 a day. Highlighted features for this server space includes:
- 30-Day No ‘Red Flag’ Guarantee
- Unlimited Bandwidth
- DDoS Protection
- HTTPS SSL Certification
Notably, Strox does not assist with domain registration. Threat actors are responsible for registering their own domains and linking them to the provided cPanel installations. A disclaimer on the hosting services page advises users not to include bank brand names in domain URLs to avoid detection by anti-phishing systems.
Based on Fortra’s visibility, Strox’s choice of “bulletproof” host has changed over the life of the operation. Recorded campaigns in 2022 utilized VPS installations on Digital Ocean servers. In Q4 2022, attacks linked to Strox had migrated to Ponytech, FranTech Solutions, and Russian provider Dolgova Alena Andreevna. In 2023, servers hosting Strox attacks have increasingly been found behind CloudFlare’s DDoS protection services, however those that are not continued to use one of the hosting providers seen in 2022.

Leads and lures
Consistent with their other offerings, Strox vies to be a one-stop shop for phishing threat actors. In order to help facilitate phishing campaigns, available materials include phishing email lures (“letters”), target email lists (“leads”), and PHP mailing scripts ready to install on Strox cPanel setups.
Strox also offers higher-priced SMS phishing (smishing) services. According to the platform, lures can be sent to victims in the U.S. and Canada across all major carriers. Unlike other SMS spamming tools, this turnkey service does not require threat actors to supply their own mobile SIM cards.
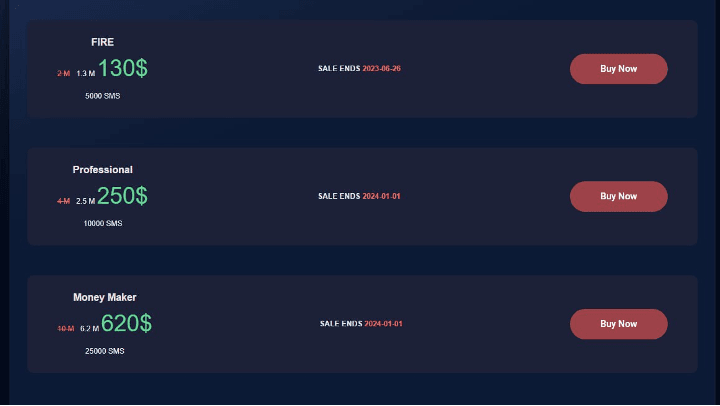
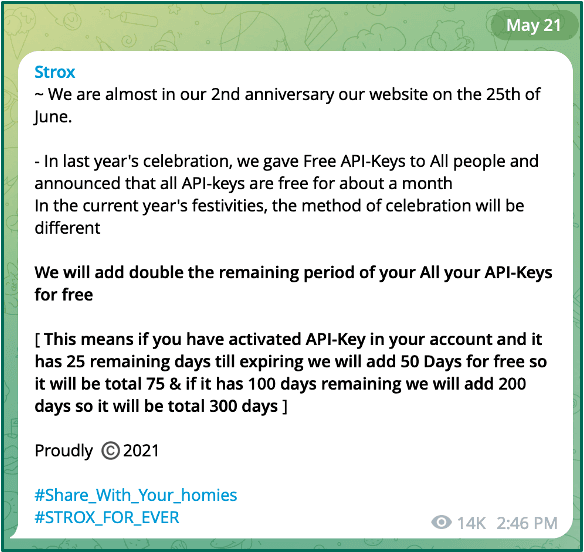
Anniversary Sales & Phishing Impact
A key trend over the past few years is a spike in Strox-linked phishing campaigns in Q2. Strox marked anniversaries with sales in June 2022 and 2023, and Fortra saw increased activity across all brands targeted by Strox in the months surrounding these events.
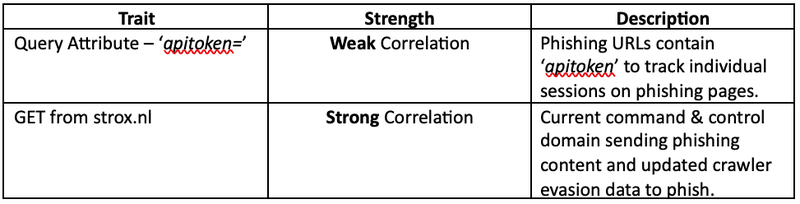
Appendix A – Strox Indicators
See how Fortra Brand Protection shuts down phishing sites and defends your brand with powerful Digital Risk Protection.