The novel coronavirus defined 2020, and cybercriminals were quick to exploit its impact. By early March, the first pandemic-themed attacks appeared, and throughout the year, these campaigns evolved to reflect both local and global developments.
COVID not only served as a common theme across multiple threat types but also accelerated the shift to remote work. In this piece, we explore how the pandemic reshaped the cybersecurity landscape.
Malicious email campaigns using COVID as a tactic began appearing at the beginning of the year, shortly after WHO declared a global health emergency. COVIDs rapid spread quickly normalized updates from healthcare experts and government leaders, and as a result the CDC and WHO became some of the first and most frequent organizations impersonated.

Lure Impersonating the CDC
Initial lures took the form of fake information regarding the virus, access to a cure, and biotech authorities communicating critical data. The threat types varied, but each ultimately encouraged victims to click on a link, open a document, or communicate with the sender.
Lure examples:
- Business Email Compromise (BEC)
- Malware
- 419 Scams
- Phishing Lures
- Docuphish
- SPAM
- Job Scams
Over the course of March, the cyber community saw a 667% surge in covid-themed phishing emails. The rapid increase in virus-led fears such as job loss, an unstable economy, and lack of basic needs like health insurance coverage gave threat actors a treasure chest of content to use against unsuspecting and concerned victims.
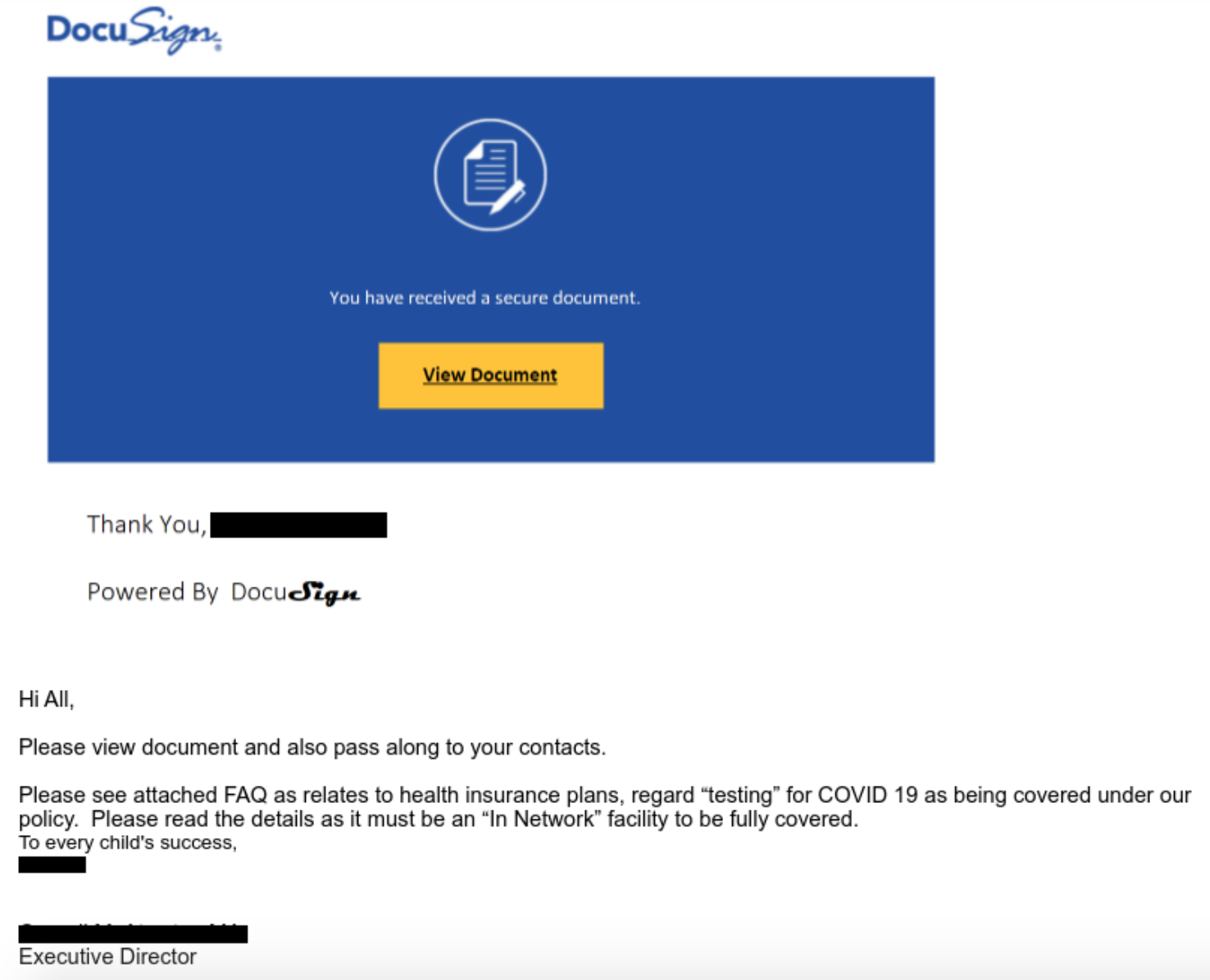
Fake Insurance Policy Lure
By April, threat actors were attacking victims via mobile devices and social media platforms. Social media is increasingly a preferred channel for criminals because of its ability to instantly distribute information and leak data on a global scale. Criminals used these platforms to engage in a variety of attacks, including money-flipping scams that promised free cash to those economically affected by COVID.
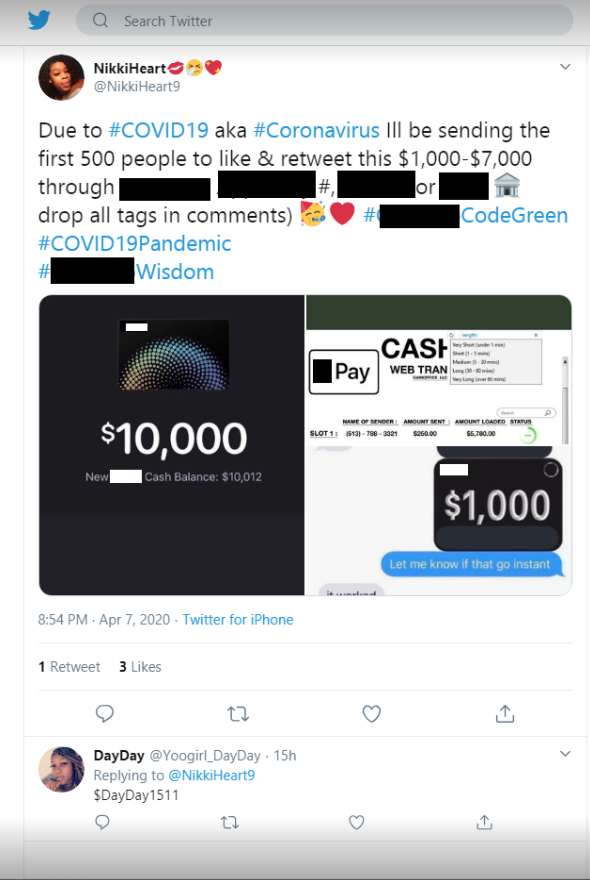
Money-Flipping Scam on Twitter
There was a 273% increase in data breaches during Q1 of this year, when vulnerabilities brought on by accelerated digital transformation gave threat actors access to systems that might otherwise have been protected. The pandemic forced many businesses to rapidly change how they used technology, and as a result, initiatives that normally would have spanned years were implemented in a matter of weeks and months, leaving weaknesses exposed. Credential theft was a huge contributor to compromise, with 80% of hacks occurring as a result of stolen data through phishing lures and sites.
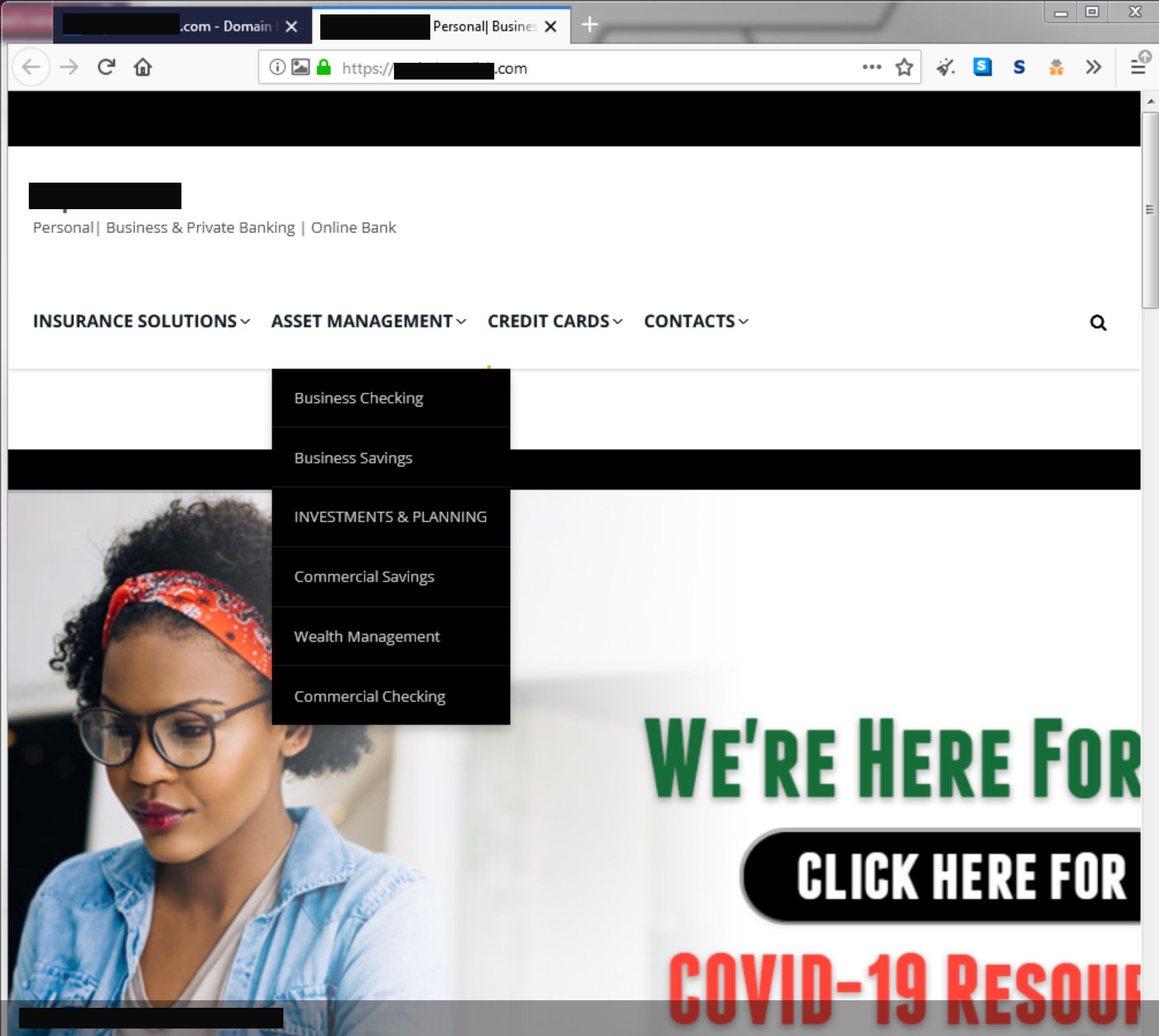
Credential Theft Site
Ransomware also made headlines in the wake of COVID. Maze ransomware operators stood out early on, promising to cease attacks on healthcare. This proved to be a lie when in May they listed stolen medical data for sale on the dark web.
The sale of compromised data is a change we have seen by operators in 2020, with ransomware and data leaks overlapping into the hybrid tactic known as double extortion. In Q3, ransomware attacks increased 50% from the first half of the year, indicating the tactic is aiding in its popularity. Healthcare, COVID-19's most vulnerable industry, is the most targeted by ransomware operators globally.
As we wrap up the year, the cyber security community is still grappling with the many faces of COVID-19 threats. Work environments and societal priorities have changed as a result of the virus, and attackers are taking advantage of the new encyclopedia of ways they can manipulate the vulnerable. As criminals continue to repurpose attacks exploiting the ongoing crisis, security teams must continue to pivot as well. Fortra Brand Protection's Digital Risk Protection and Email Intelligence & Response help organizations detect and mitigate threats that abuse the novel coronavirus.
Off
