QBot was the most frequently reported malware payload targeting employee inboxes in Q4, marking the fourth consecutive month it has dominated malware activity. Previously, in Q3, QBot ranked second behind RedLine Stealer, highlighting its rapid rise as threat actors maintain high-volume, persistent attack campaigns against organizations.
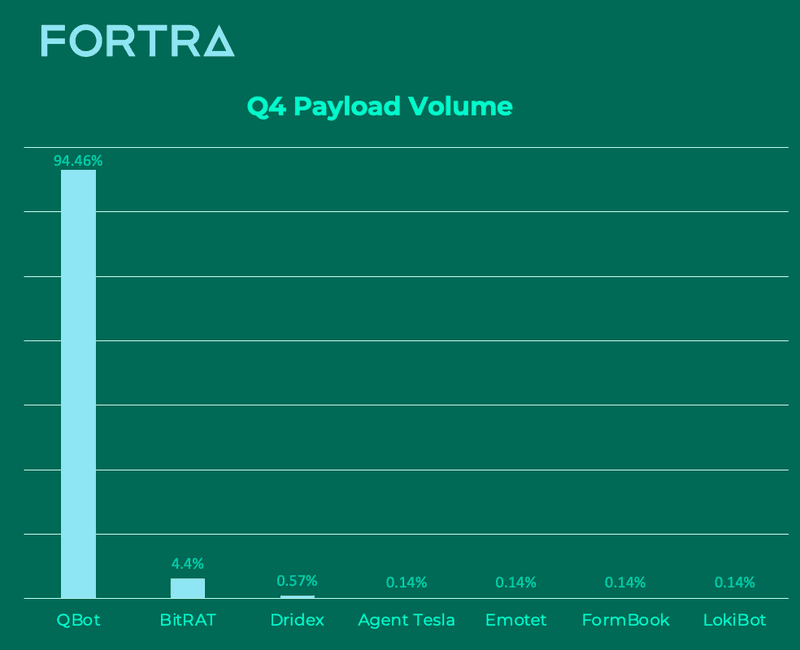
Email continues to be the primary delivery method for ransomware targeting businesses. Continuous monitoring of reported payload families in corporate inboxes is critical for mitigating these threats. Below is a breakdown of the top payload threats to enterprises in the fourth quarter.
QBot
QBot represented the vast majority of malware attacks in the fourth quarter, contributing to 94.46% of total volume. QBot is a versatile MaaS (malware-as-a-service) capable of performing a broad range of actions including stealing financial information and credentials, moving laterally within networks, and more.
QBot is one of many former banking trojans increasingly used by threat actors to install backdoors for malicious software like ransomware. Delivery tactics include phishing lures containing malicious Microsoft Word or Excel attachments, and HTML hijacking campaigns using SVG files to smuggle malicious Javascript onto an end-user’s device. QBot is linked to the Egregor and Black Basta ransomware families.
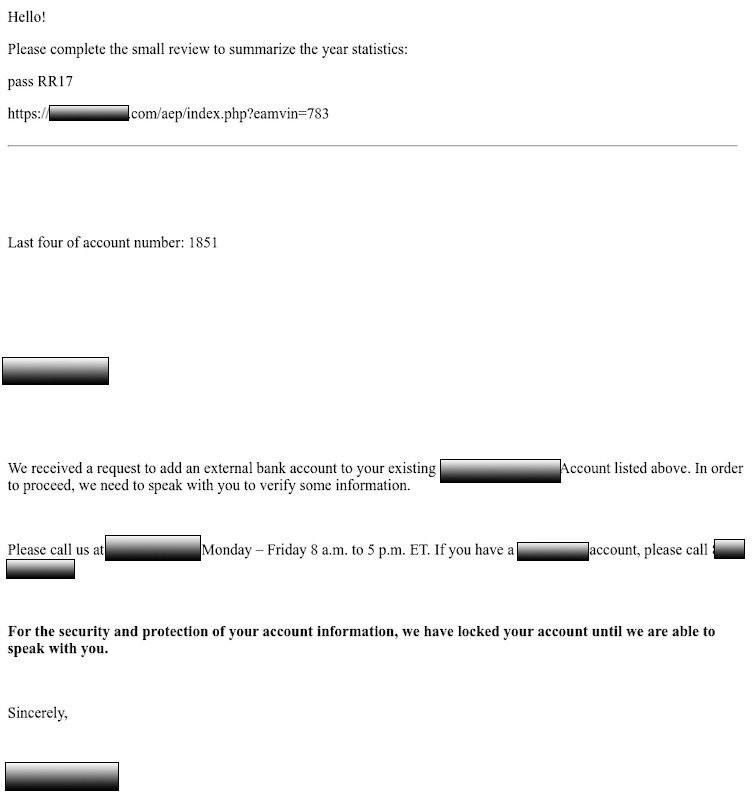
Following is an example of a phishing lure containing a link to QBot malware. The attacker used a previously legitimate email thread to deliver the lure.
BitRAT
BitRAT was the second most reported payload variety in Q4, contributing to 4.4% of overall volume. BitRAT is a low-cost, ready-to-deploy malware that has grown in popularity within the criminal underground since its emergence in 2021. BitRAT’s capabilities include stealing credentials and delivering ransomware. Recent BitRAT campaigns use previously stolen banking data in phishing lures.
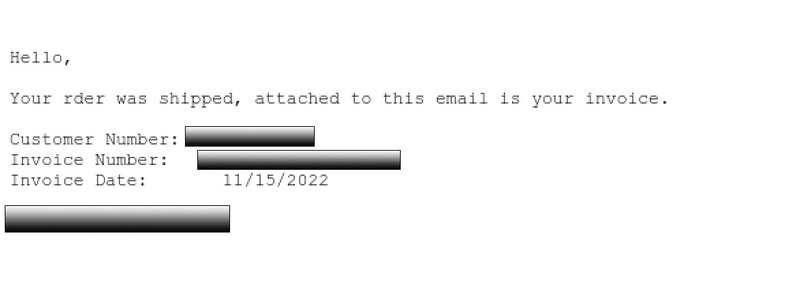
Below is a phishing lure delivering a BitRAT attachment.
Dridex
Dridex rounded out the top three payload varieties in Q4, making up 0.57% of reports. Dridex is a banking trojan and backdoor capable of form grabbing, key logging, and data encryption. It is also capable of more advanced functions such as atom bomb injection, a code injection technique which abuses Windows atoms tables to infiltrate systems.
Dridex has been largely absent from reports in 2022, with its volume peaking in October. The malware is thought to be the brainchild of Russian actor group Evil Corp and has recently been linked to newcomer Raspberry Robin, a worm with similar functionality and infrastructure.
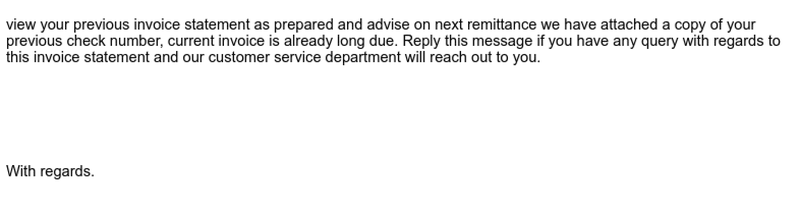
Below is a phishing lure delivering a malicious attachment infected with Dridex.
Other malware varieties reported in Q4 were Agent Tesla, Emotet, Formbook, and LokiBot.
Malware continues to result in data and financial loss and is often used as initial access in ransomware attacks. Malware varieties frequently fluctuate in activity, as functionalities are improved upon and new tactics are adopted. Fortra’s PhishLabs monitors payload activity so that organizations may better prepare for and prevent these types of attacks.
Learn how Fortra protects against threats targeting corporate inboxes.
