Fake mobile apps are more sophisticated and more dangerous than ever. Cloned and spoofed mobile applications flood both official and third-party app stores, exploiting brand trust to trick users into downloading malware. These imposters don’t just erode brand equity; they expose users to serious data breaches. And with mobile users often skipping basic security precautions, the risk of compromise continues to rise.
Fake Apps
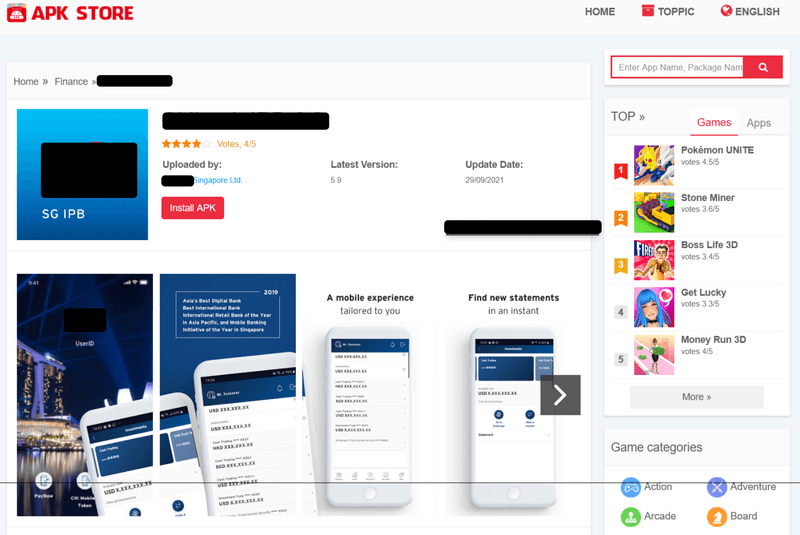
Fake mobile apps are deceptive clones of legitimate applications. They're often cheaper and easier to access through third-party app stores than official ones.
These unofficial marketplaces, numbering in the hundreds and growing, operate with little oversight. This makes them a breeding ground for threat actors who mimic real apps, abusing trademarks, copyrighted content, and other brand assets to appear authentic.
Relying on familiar logos, language, and user interfaces, these fake apps trick users into downloading malicious software — often without verifying its legitimacy or source. Cybercriminals exploit this misplaced trust to:
- Divert traffic
- Earn ad revenue, and/or
- Steal sensitive data
Detection
Detecting brand abuse across mobile platforms is increasingly complex. New third-party app stores are constantly emerging, and unofficial apps can be created and distributed in minutes. Most enterprises lack the visibility and expertise to keep up.
To stay ahead of mobile app fraud, organizations need dedicated mobile threat analysts and continuous monitoring of both known and newly launched app stores. Suspicious apps should be flagged immediately if they reference, mimic, or misuse brand assets, including unauthorized use of:
- Logos
- Trademarks
- Content
- Functionality
- Appearance
Because of the high volume of brand mentions that may be flagged when monitoring third-party sites, security teams should conduct manual analysis to determine whether brand references qualify as abuse.
Mitigation
When a mobile app poses a real threat to your brand or users, swift mitigation is critical. Security teams should work directly with third-party app stores to report and remove malicious or infringing apps. Establishing relationships with these platforms in advance can streamline communication and accelerate takedowns.
Not all brand mentions qualify as violations. Using your brand name in app descriptions or metadata may not meet the threshold for removal. That’s why it’s essential to report all suspicious apps for deeper review, especially if they replicate your branding, impersonate official channels, or engage in deceptive behavior.
If third-party store contacts are unresponsive, escalation may require additional details such as hosting provider, domain registrar, registrant identity, and country of origin. Broadening your mitigation approach beyond the app store can improve the chances of a successful takedown.
Successful mitigation does not ensure removal is permanent. Fake apps may re-appear with edits or adjustments to content or imagery and may require additional action by security teams. Following is an example of a cloned application removed by Fortra Brand Protection, later re-emerging in a different language.
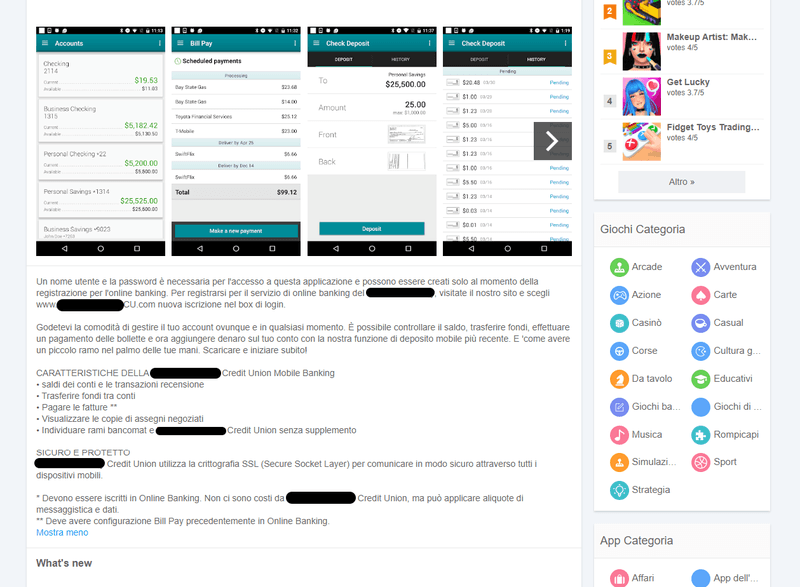
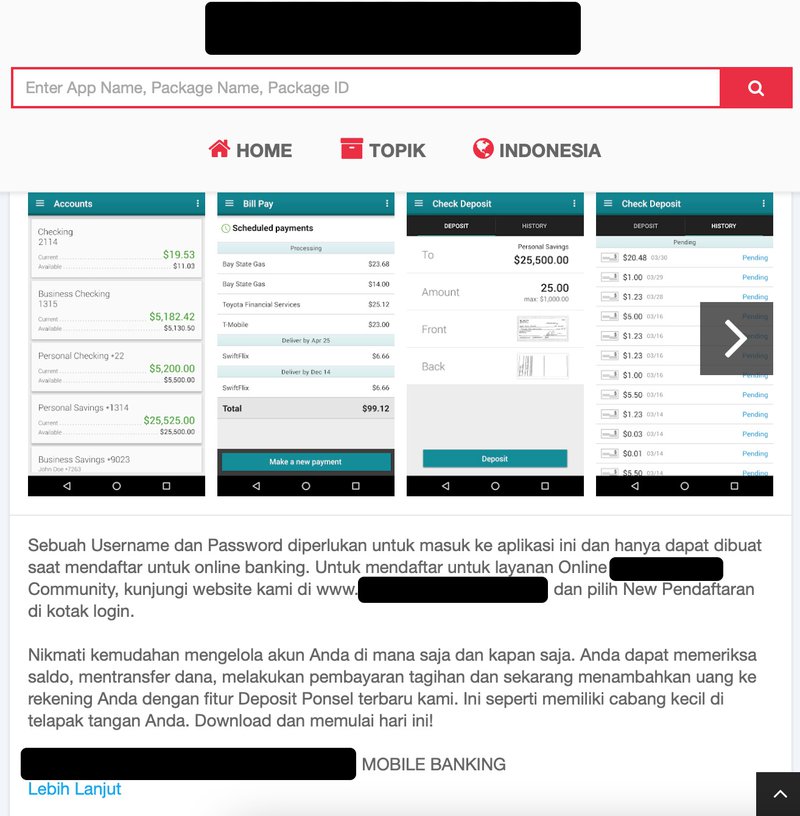
Why It Matters to Security Teams
Outdated or unauthorized versions of your mobile app can open the door to serious threats. Cloned apps often lack critical security updates, exposing users to data theft, fraud, and ransomware. Beyond the technical risks, brand impersonation can erode trust and inflict significant financial and reputational damage. Security teams must proactively detect suspicious apps targeting their brand and act swiftly to assess and remove those posing a threat.
In today’s mobile-first world, protecting your brand across app stores is no longer optional, it’s essential. Threat actors are increasingly exploiting mobile platforms to impersonate legitimate brands, deceive users, and launch damaging attacks. With Fortra Brand Protection's Mobile App Protection, organizations gain comprehensive visibility into app store threats, expert analysis to assess risk, and rapid takedown of malicious or unauthorized apps. By partnering with Fortra Brand Protection, security teams can defend their brand integrity, safeguard customer trust, and stay ahead of evolving mobile threats.
