Phishing site volume increased 28% over the course of 2021, according to our Quarterly Threat Trends & Intelligence Report. Attacks last year displayed increasingly volatile behavior on a month-to-month basis, often intermixed with a variety of attack vectors. Despite a lack of congruency, phishing unequivocally remains the most dominant attack method targeting organizations.
Every quarter, we analyze hundreds of thousands of phishing and social media attacks targeting enterprises, their brands, and their employees. In this post, we analyze phishing activity targeting organizations, their brands, and customers.
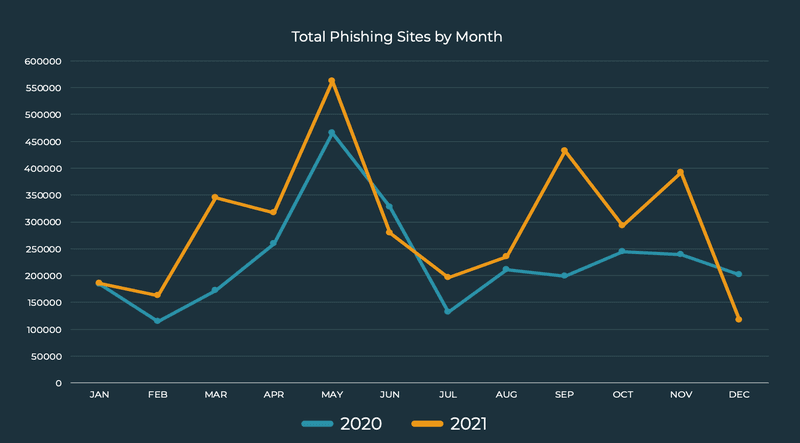
Phishing attacks proved more unpredictable than 2020, with a significant spike once again occurring in May and an uncharacteristic two-year low recorded in December. Despite these striking fluctuations, Q4 2021 phishing volume still outpaced Q4 2020 by 16.8%.
In Q4, November experienced the third highest monthly volume of attacks this year. Alternately, December recorded the second lowest number of attacks in a two-year period, dipping 42.2% below December of 2020.
Industries Targeted
The financial industry, telecommunications, and social media contributed to nearly 98% of all phishing sites in Q4. These three industries represented the top targets for attacks throughout 2021, with some fluctuation among the leaders.
Financials were targeted most, contributing to 61.2% of attacks after a 6.2% increase in share in Q4. Overall, attacks on the financial industry increased consistently during 2021, experiencing an increase in share of 27.5% from Q1 to Q4.
Telecommunications overtook social media for the first time to become the second most targeted industry. Attacks on telecommunications experienced an increase of 17.2% in share from Q3.
Other industries targeted by phishing sites in Q4 include Webmail & Online Services (1.6%) and Ecommerce (0.3%).
Site Staging
In Q4, just over half (50.1%) of all phishing sites were staged by abusing a free service or tool. Minimal shifts in share were seen across all staging methods, with Tunneling Services experiencing the most significant change, declining 5.1% from Q3.
Although free sites and resources as a whole are desirable to threat actors, compromising existing websites represented the single most abused method for standing up phishing sites (36.4%) in Q4. Paid domain registrations experienced a slight decrease (0.3%), contributing to 13.5% of staging methods.
Domain Abuse
Legacy top-level domain .com accounted for half of all phishing activity in Q4, despite a decrease in share of 4.9%. As a group, nearly 60% of all phishing scams reported used a Legacy generic Top-Level Domain for staging phishing sites.
Country code top-level domains (ccTLDs) were used widely in Q4, accounting for one-third of all phishing sites staged. The ccTLD .ca experienced the largest increase in abuse, contributing to nearly 20% of all phishing activity.
Notably, the ccTLD .uk experienced an increase in abuse in Q4, moving to the third most abused TLD from the 22nd position. Additionally, ccTLDs .hk and .ng made their debut on the top 10, rising to 7th from 137th and 9th from 81st, respectively.
Despite commanding a majority of threats facing enterprises, the erratic volume of phishing attacks in 2021 is indication of the increased presence of emerging online threats. In order to proactively protect against attacks targeting organizations, security teams should invest in broad detection and cross-channel monitoring.
To learn more, access our Quarterly Threat Trends & Intelligence Report.