In Q1, the exchange of sensitive data on Carding Marketplaces and Forums increased as government seizure of multiple Dark Web sites prompted a shift in where actors conduct illegal activities, according to the Agari and PhishLabs Quarterly Threat Trends & Intelligence Report.
These sites specialize in the trafficking of stolen credentials and data such as usernames, passwords, banking, and account information. Sensitive data is advertised via a variety of sites on the Dark Web, however the constant threat of platform seizure and shutdown equates to an unstable environment where actors often must adjust where they conduct transactions.
Every quarter, we analyzes hundreds of thousands of attacks targeting enterprises and our clients. In this blog, we analyze a sample set of client data representative of the underground landscape to identify the most recent threats on the Dark Web and who they are targeting. In this piece, the Dark Web is defined as the part of the web that cannot easily be indexed and generally requires some technical obstacles to access.
Top Dark Web Threats
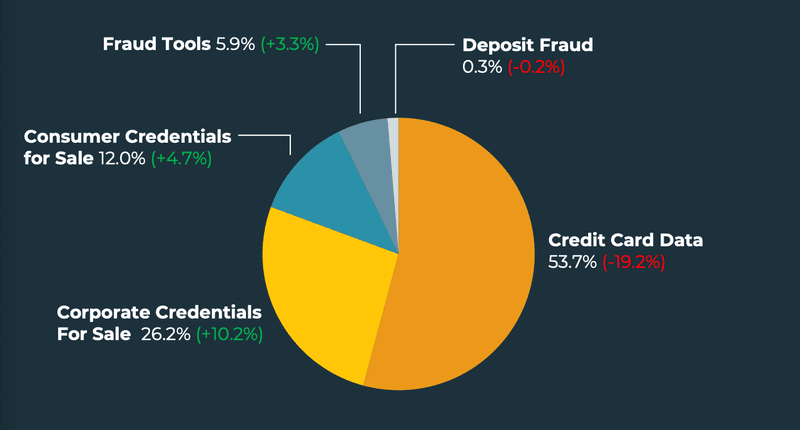
In Q1, credit card data represented 53.7% of all Dark Web incidents. Stolen credit and debit card data are consistently the top threat marketed by bad actors on the Dark Web. In Q1, card data once again represented the top advertised threat, despite a nearly 20% decrease in share from Q4.
As a result of the drop in card data, corporate credentials for sale increased 10.2%. This is the second consecutive quarter corporate credentials have experienced the greatest gain in share among Dark Web incidents. In Q1, corporate credentials for sale represented 26.2% of all Dark Web threats.
The sale of consumer credentials and fraud tools also experienced increases in Q1, representing 12% and 5.9% of share of all Dark Web incidents. Deposit fraud declined, contributing to only 0.3% of threats.
Top Targeted Industries
Financial institutions as a group contributed to nearly three-quarters of all Dark Web attacks in Q1. Compromised data associated with this industry is highly coveted by threat actors, and can mean access to Personally Identifiable Information (PII), card information, and login credentials.
In Q1, National and Regional Banks were targeted more than 40% of the time, leading all other industries despite a decrease of share of 8.8%. Credit Unions also experienced a decline, representing 21.1% of attacks. Other Financial Services experienced the only increase within the group, contributing to 11.8% of attacks.
Non-financial industries Telecom & ISPs and IT Services both experienced an uptick in share of attacks in Q1. Telecom & ISPs grew to represent 8.5% of all attacks. IT services were targeted 4.6% of the time.
Other industries targeted:
- Dating 2.9% (+0.8%)
- Staffing & Recruiting 2.8% (-0.2%)
- Retail 2.6% (+1.8%)
- Cryptocurrency 1.8% (+1.7%)
Where is Stolen Data Marketed
When popular Dark Web marketplaces are disrupted, new marketplaces emerge elsewhere to meet demands. Bad actors stand up these sites quickly, often cloning the language and infrastructure of heavily trafficked services.
In Q1, multiple Dark Web operations were shuttered, requiring vendors and customers to exchange information in new environments. This resulted in an increase in activity on Carding Marketplaces and Forums, with nearly 64% of stolen data on the Dark Web marketed via these types of sites. While Carding Marketplaces represented the majority (36.1%) of activity, Forums experienced the greatest increase in share, growing 9.3% from Q4.
Chat-Based Services were used less in Q1, declining 16.8% in share. This is the second consecutive quarter Chat-Based Services as an advertising platform have experienced a decline in activity, contributing to only 20.6% of Dark Web incidents. In Q3 2021, Chat-Based Services represented nearly 56% of all activity. Speculating, the decrease in activity may be attributed to less carding data being communicated by actors through those services.
Credential Marketplaces that specialize in the sale of account-based data increased 4.5% in share during Q1. Credential Marketplaces represented more than 12% of all Dark Web incidents. General Marketplaces also experienced an increase in share, growing 1.4% and representing 2.6% of dark web incidents. Paste Sites rounded out the top five, contributing to 1.0% of activity.
In Q1, Illicit activity on the Dark Web was turbulent, as the take down of multiple Dark Web services required actors to conduct transactions on new and varying platforms. Instability on the Dark Web is common, and the constant threat of exposure and arrest means criminals must pivot to avoid apprehension. Understanding where illegal activity is taking place, and the types of data that are being exchanged on Dark Web sites is critical to helping organizations detect compromised data. PhishLabs continuously monitors and reports on Dark Web threat types and the industries that are targeted.
