Credit unions were the top targeted industry on the Dark Web in Q4 2023, continuing its lead over the historically targeted banking industry for the third consecutive quarter. Financials as a whole continue to be a primary focus of criminal groups on underground channels, with more than 91% of malicious activity directed at either credit unions, banks, financial services, or payment services.
Every quarter, Fortra analyzes hundreds of thousands of attacks targeting our clients. In this blog, we identify the most recent threats on the dark web and the industries they are targeting by analyzing a sample set of client data representative of the underground landscape. For purposes of this article, Fortra defines the dark web as the part of the web that cannot easily be indexed, and generally requires some technical obstacles to access.
Dark Web Threats
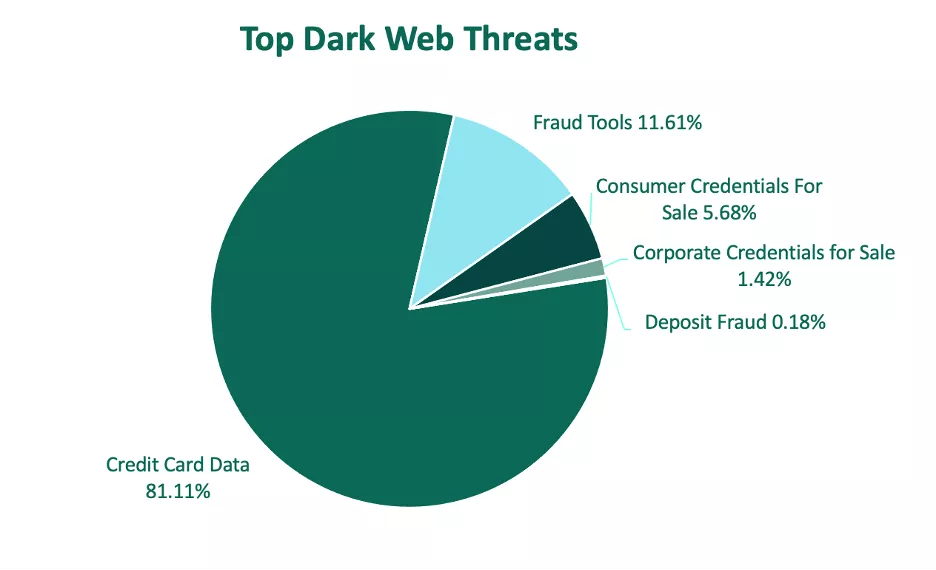
Credit card data was the most advertised threat type on dark web channels in Q4, making up over 81% of overall volume. Stolen card data consistently leads all other categories quarter-over-quarter, as this type of compromised information can lead to a quick profit for threat actors.
Fraud tools, such as phish kits or guides, were the second most prevalent threat type in Q4. Fraud tools contributed to 11.6% of all dark web threats, which is the lowest volume of share for the category after consistent QoQ declines in 2023.
Consumer credentials, or access to customer accounts, made up 5.7% of share of dark web threats. Other categories included:
- Corporate credentials for Sale 1.42%
- Deposit fraud 0.18%
Most Abused Industries
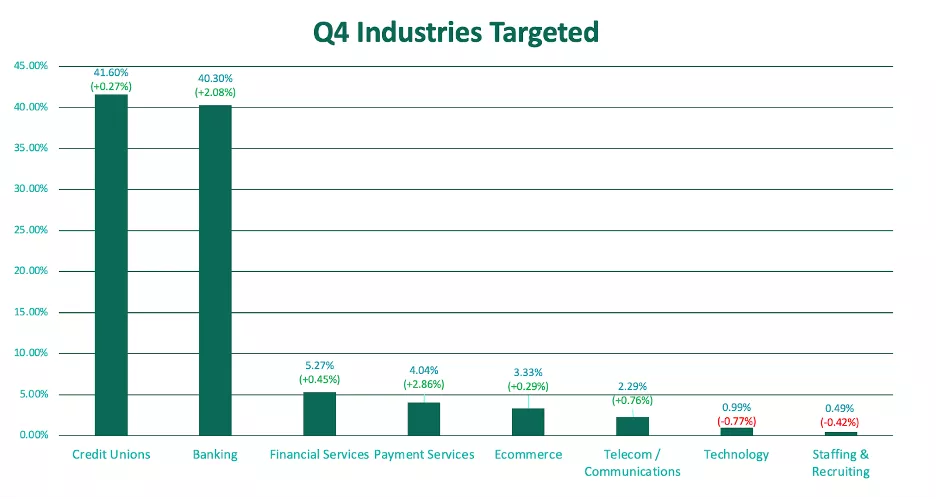
Financial institutions were the primary focus of actors on the dark web, making up an overwhelming 91% of total volume. The lion’s share of finance was divided between credit unions and banks, with the two experiencing nearly identical shares of abuse. All financially-focused industries saw an increase in attack volume.
Credit unions were the most targeted industry for the third consecutive quarter with 41.6% of volume, surpassing banking share of volume by just over a percent. Credit unions are a desirable target for threat actors, because they understand small institutions may lack the resources needed to adequately monitor underground channels for suspicious activity targeting their brand.
Banks were targeted 40.3% of the time after a quarter-over-quarter increase of more than 2%. This represents the greatest share of volume for the category since 2022.
Financial services and payment services rounded out the top four, making up 5.3% and 4%, respectively.
Other industries targeted include:
- Telecom/Communications services 2.3% (+0.76%)
- Technology 1.0% (-0.77%)
- Staffing & recruiting 0.5% (-0.42%)
Where Stolen Data is Marketed
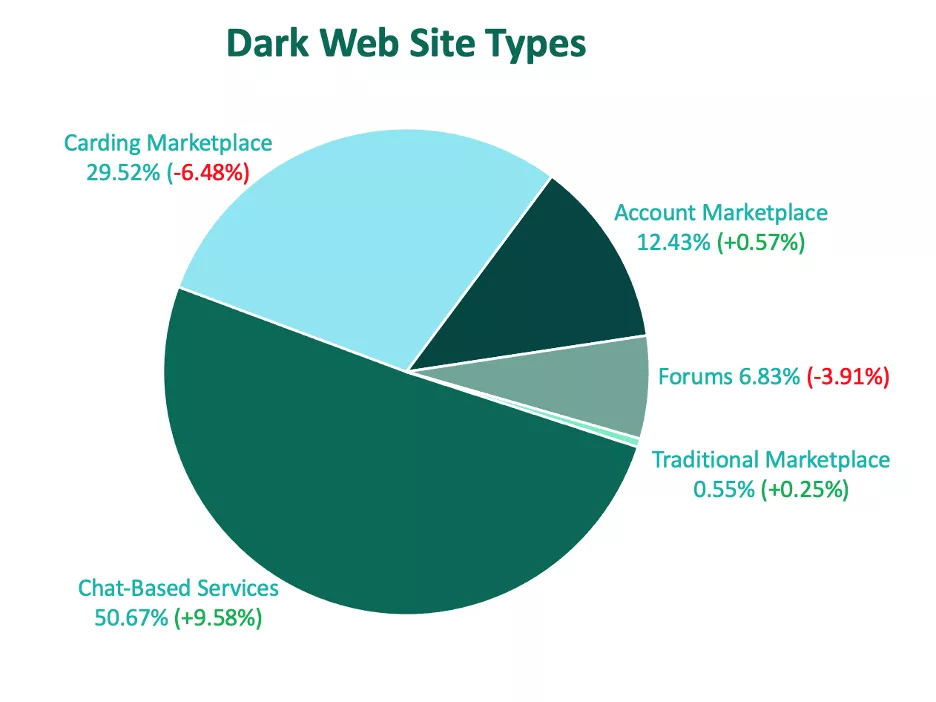
Security teams should be prepared to monitor a variety of spaces for suspicious activity targeting their brand, because the location of criminal activity is fluid.
In Q4, the majority of threat actor activity took place on chat-based services, with more than 50% of dark web threats detected in these spaces. Criminal activity in chat-based services saw an increase every quarter in 2023, peaking at the end of the year with the greatest volume of share since 2021.
Carding marketplaces remained the second most popular site type for the third consecutive quarter with nearly 30% of volume. This is despite a 6.5% decline in activity. Carding marketplaces were the top location for malicious activity in 2022 but have since taken a backseat to chat-based services.
Malicious activity took place on account marketplaces 12.4% of the time after a nominal increase in Q4. Forums and traditional marketplaces trailed behind with 6.8% and 0.6% of threat volume, respectively.
Stolen information and malicious tools on the dark web leave organizations and their customers prone to a wide range of threats including compromise, revenue loss, reputational damage, and more. The complex and gated nature of underground channels makes these threats difficult to identify. In order to prevent attacks that originate from the dark web, security teams should actively monitor for stolen data and suspicious activity associated with their brands.
Fortra can help detect dark web activity targeting your brand.
