Two significant changes have been observed in the C2 tactics used by the threat actors behind BankBot Anubis, a mobile banking trojan. One change is the use of Chinese characters to encode C2 strings, in addition to base64 encoding. Another is the use of Telegram Messenger alongside Twitter to communicate C2 URLs.
We previously reported the criminals behind BankBot Anubis have been using public Twitter accounts to post tweets containing encoded C2 URLs in an attempt to hide their C2 infrastructure.
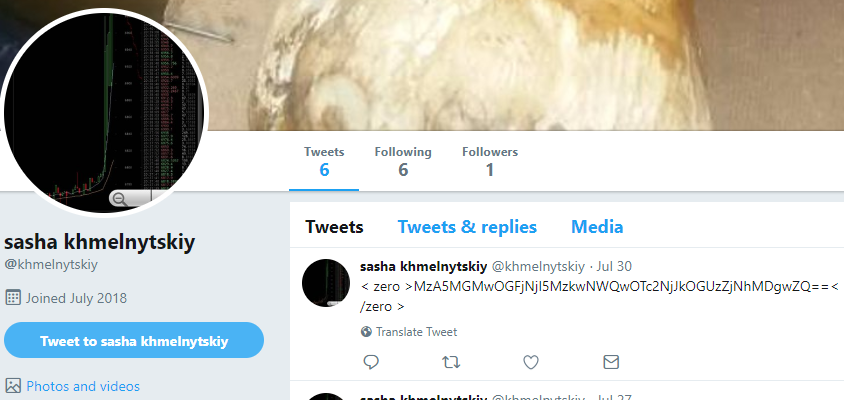 Example of BankBot Anubis C2 communications via Twitter
Example of BankBot Anubis C2 communications via Twitter
Recently, we observed BankBot Anubis threat actors encoding C2 information posted to Twitter using Chinese characters.
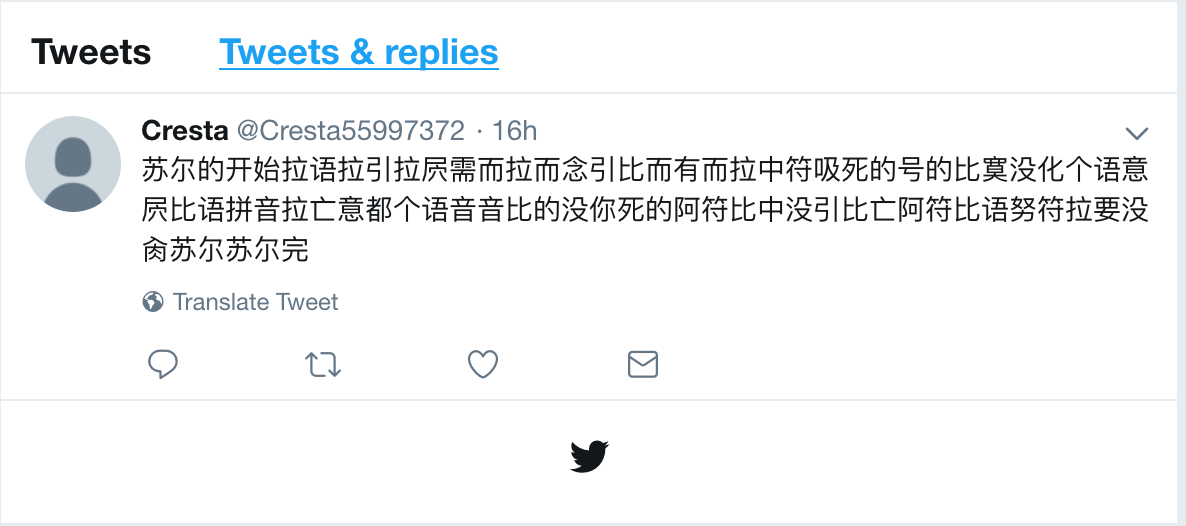
BankBot Anubis Twitter C2 Message in Chinese
Why use Chinese? Previously, the C2 posts contained base64 encoded strings. Translating the base64 strings to Chinese characters creates an additional step that malware analysts have to take in order to reveal the plaintext C2. Plus, having a large string of Chinese characters is less suspicious and would definitely garner less attention than the previous base64 encoded strings.
The first step towards revealing the plaintext C2 URL is to convert the Chinese characters.
苏尔的开始比语有屄并而标妈死寞没脚死语在符拉中念吸个中意都拉语意脚拉而努号比要需你拉而件音拉要死斯比的件音苏尔苏尔完
This converts to a base64 string:
NDI2Yzg1ZmU4ZDRkMTA5OTEyMDE4MzBlNWQ0MzdhMWZiNjdh
Which can then be converted to a base16 string:
426c85fe8d4d10991201830e5d437a1fb67a
This is then decoded to reveal the C2 URL in plaintext.
https://[EVIL-DOMAIN.TLD]
Not only have these threat actors updated how they encode their C2 communications, they're also trying out new ways to deliver them. After seeing the use of Chinese characters on Twitter, we observed the criminals also start using Telegram Messenger, a free messaging application. Telegram offers the use of public channels to broadcast messages to large audiences with a public URL.
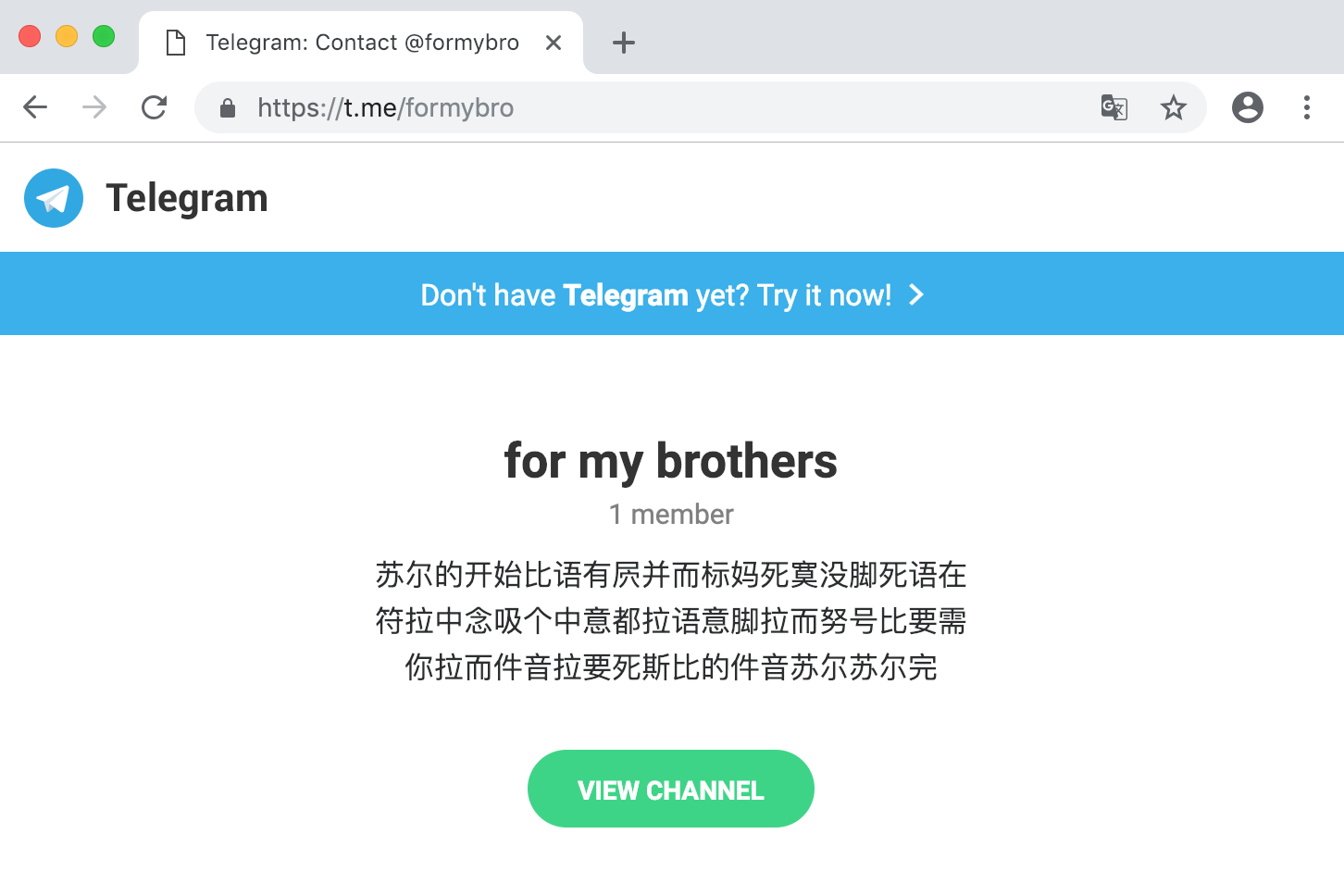 BankBot Anubis Telegram C2 Message in Chinese
BankBot Anubis Telegram C2 Message in Chinese
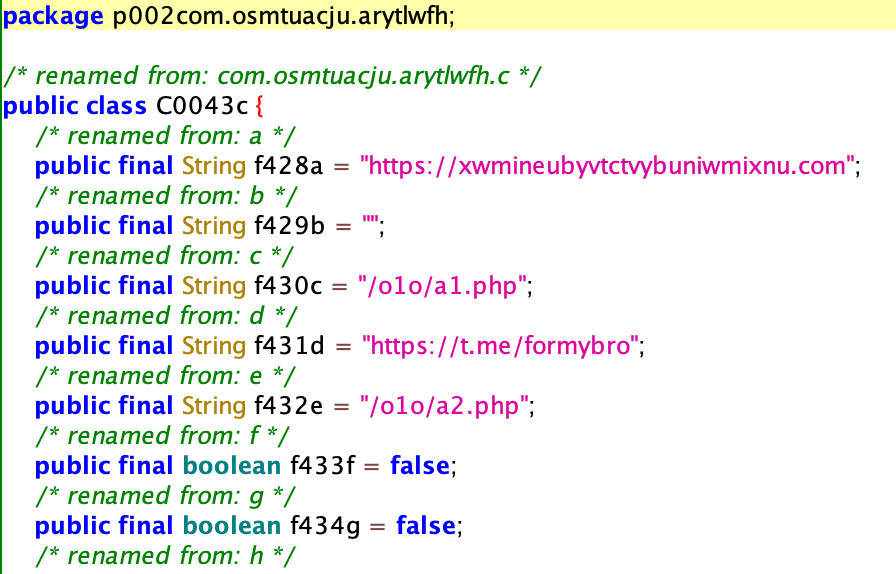 Screenshot of BankBot Anubis JAR file containing C2 URL
Screenshot of BankBot Anubis JAR file containing C2 URL
Why the change? The overall trend of using social media such as Facebook, blogs, or Twitter for C2 is not new, however we suspect the addition of Telegram by BankBot Anubis could simply be to test it out as a new venue for C2 communications.
In summary, these developments highlight the continued efforts by the threat actors behind BankBot Anubis to refine their tooling and complicate defensive efforts. As a widely deployed mobile banking trojan targeting hundreds of mobile applications across organizations worldwide, BankBot Anubis remains a significant threat. Security and threat intelligence professionals should closely monitor its activity and evolution to stay ahead of emerging tactics.