This guest blog by Dr. Edward Amoroso, TAG Cyber, provides a high-level overview of modern advances in cyber threat intelligence and how the Fortra cybersecurity portfolio supports this important method for reducing information risk in enterprise at various levels of the intelligence process starting with data security.
Three oft-misused words in cybersecurity are data, information, and intelligence. Take a moment and see if you can write down good definitions for each. (I’ll wait.) If you’re like most people (and many websites), then you get tangled into circular definition loops where each of these terms is defined using one of more of the others as synonyms. This is wrong because these three concepts have different meanings.
Here are the definitions I write on my white board for students: Data quantifies observations, information combines data into patterns, and intelligence contextualizes information to produce insights. Obviously, if the data is bad (which it often is), then the progression to intelligence can go awry. And if the combination or contextualizing steps go bad, then the wrong insight is achieved at the end. This happens often.
This is important to a proper understanding of cyber threat intelligence because it implies that data, information, and intelligence are not always correct. And the intelligence collected by an enterprise does not always provide the correct insight. What this implies is that many different components of a security program, including those focused on protecting data, must be in place to ensure accurate threat intelligence.
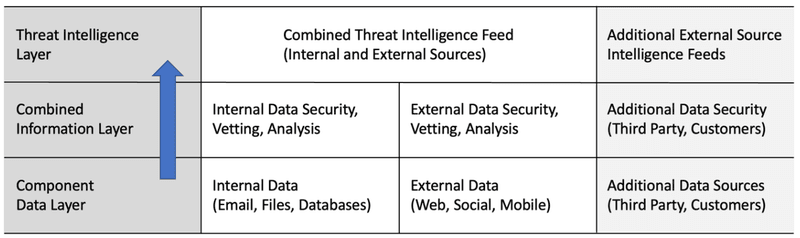
The Fortra portfolio directly supports the threat intelligence process in two important ways. First, it includes a range of data security solutions that protects the integrity of internal data as it is shared in, out, and around the network. Vera protects sensitive data shared across O365, SharePoint, DropBox, and Box, Clearswift protects email and web data, and Titus and Boldon James classify and identify the data.
These data security components can be integrated into a powerful underlying foundation for threat intelligence. Certainly, data security cannot ensure that all data sources are accurate. For example, an Internet of Things (IoT) device might correctly (or incorrectly) derive telemetry for sharing with the enterprise. But the security solutions from Fortra will ensure that no tampering or disclosure occurs once the data has been created.
Second, the Fortra portfolio includes solutions that generate and support threat intelligence provision and management. Specifically, the acquisition of PhishLabs positions the parent company directly into the cyber threat intelligence marketplace for enterprise. This enables a powerful combination of controls at all levels of the threat intelligence lifecycle across the Fortra suite of products.
Founded in 2008, PhishLabs provides threat intelligence to support brand integrity, prevent account takeover (ATO), and protect social media. Such visibility is now an essential aspect of modern enterprise teams which include hybrid use of cloud, SaaS, and social media. The PhishLabs team also includes support for mitigation of cyber threats with focus on data leakage and suspicious emails.
The PhishLabs threat intelligence platform works by analyzing massive amounts of data from the surface and dark web, social media, mobile apps, and email. The data is vetted and curated into a proper threat identification feed for customers. The resulting intelligence and insights can be used to prevent impacts to brand, business assets, and even individuals. Such external threat focus is critical to an accurate understanding of an organization’s full security posture.
The email security mitigation component of PhishLabs integrates well with complementary Fortra defenses against Business Email Compromise and advanced email threats – obtained through acquisition of email security company Agari. Enterprise teams will benefit from the combined solutions of PhishLabs and Agari, especially given the prominence of email phishing in modern attack campaigns.
The bottom line is that threat intelligence requires controls and capabilities at many different layers. Fortra has done a capable job putting together solutions that will assist in delivering high integrity data and information up the pipeline toward a threat intelligence process that can effectively reduce enterprise cyber risk.