Since 2015, PhishLabs (now Fortra Brand Protection) has and continues to track how threat actors abuse HTTPS or SSL certs. In particular, threat actors often use HTTPS on their phishing sites to add a layer of legitimacy, better mimic the target site in question, and reduce being flagged or blocked from some browsers.
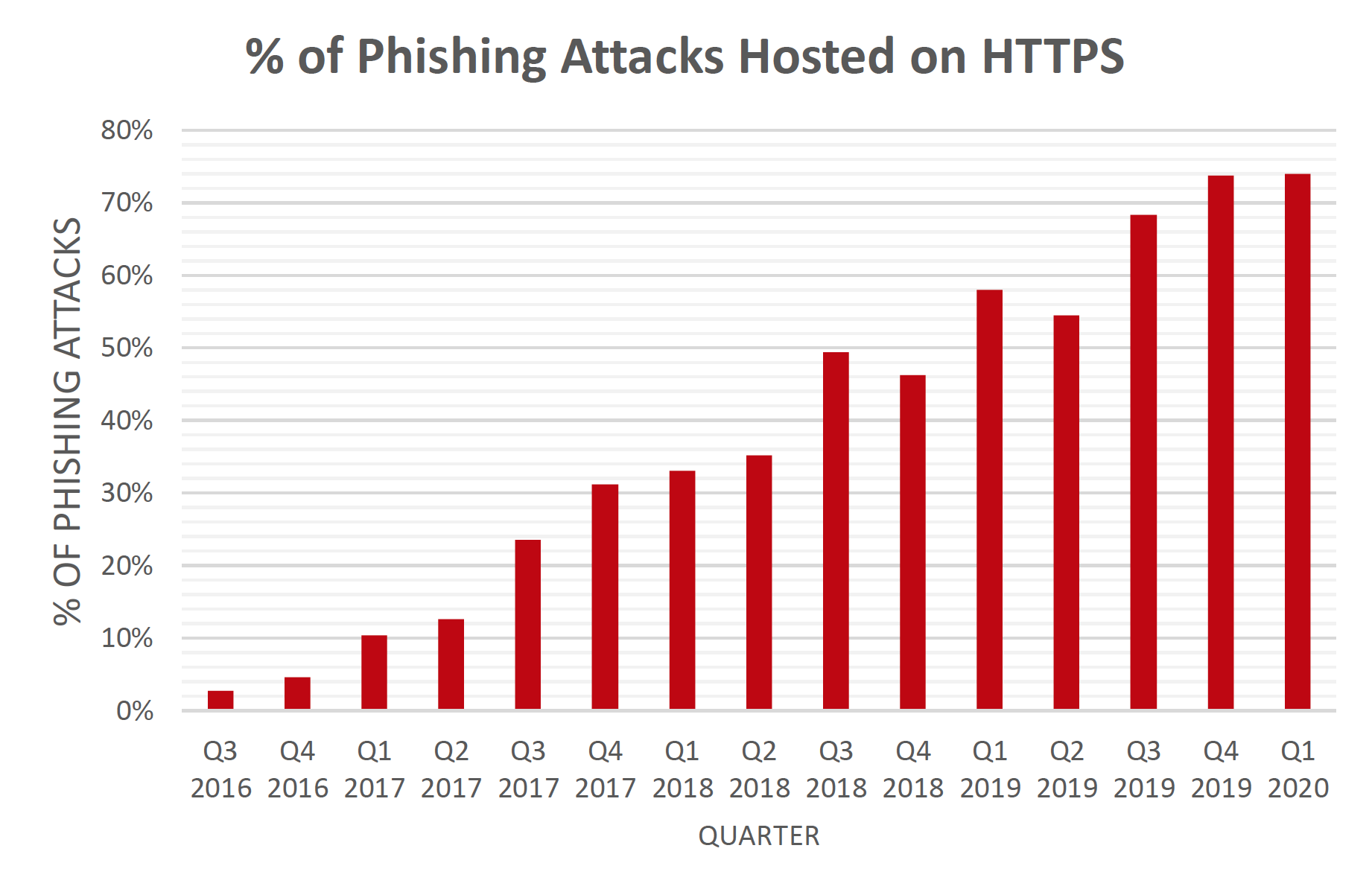
In 2014, threat actors hit a significant milestone in this usage when more than 50% of phishing sites included an SSL certificate. Now, just six months later, our data suggests that nearly three-fourths of all phishing sites, specifically 74%, now abuse HTTPS.
“The majority of phishing web sites continue to use SSL/TLS," said John LaCour, PhishLabs Founder. “We hope that users have learned that SSL doesn't mean a site is legitimate. Virtually every website — good and bad — now uses SSL."
The majority of sites now use SSL certs or what shows as HTTPS in the URL bar. Since we began tracking phishing sites that abuse HTTPS, the number has gradually increased. In 2019 however, the number of phishing sites that used HTTPS spiked, reaching new records in each quarter of the year that followed. By Q4 of 2019, the number of phishing sites reached just below 74% where it has since stabilized. There are currently no indicators to show a decline. This is due to the availability and accessibility of obtaining an SSL certificate as well as the ease in which threat actors can acquire one without additional overhead. In some cases, threat actors can simply take over a legitimate site and abuse their SSL cert.
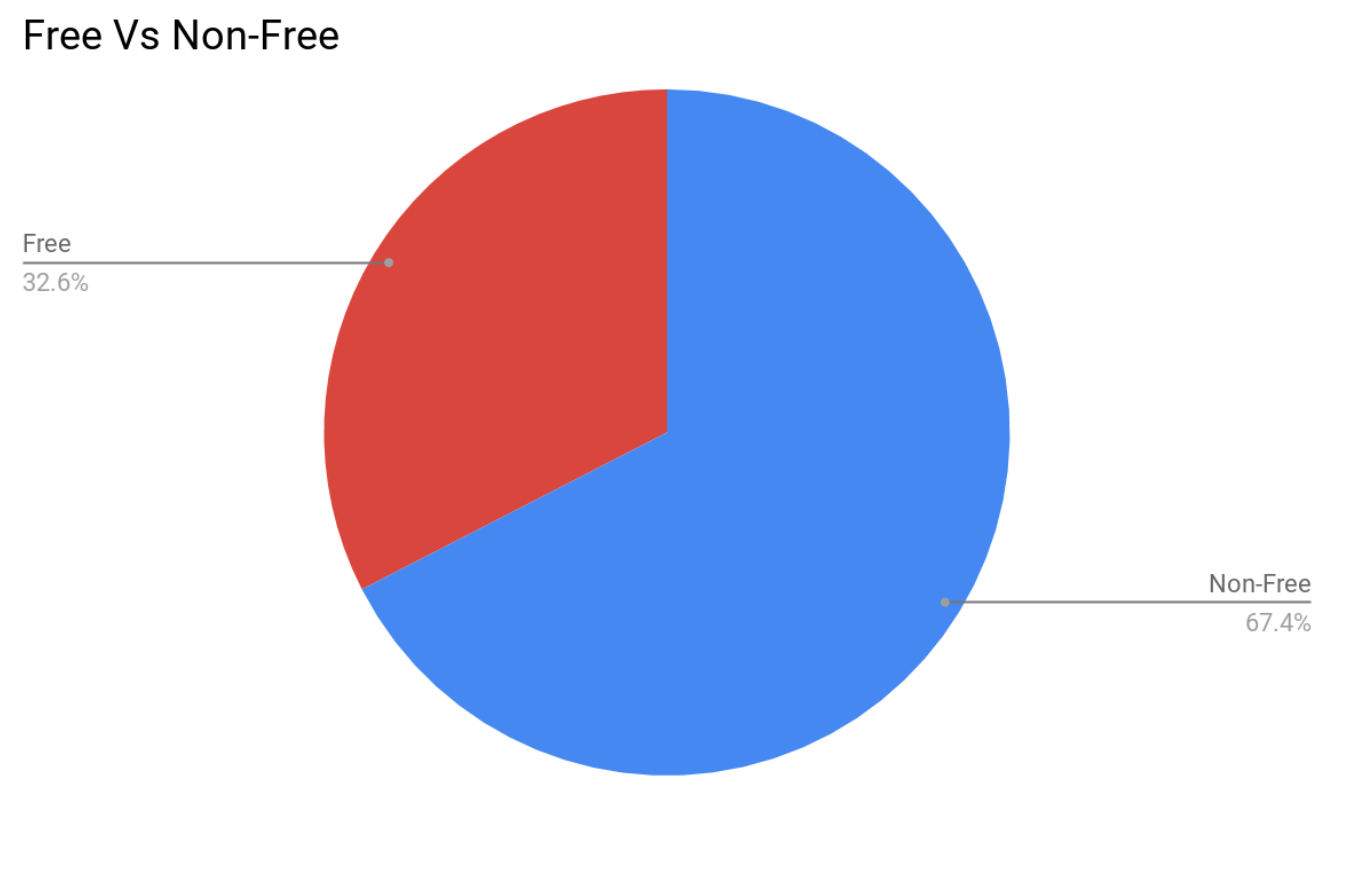
Historically, most phishing sites operated on paid or compromised domains. Over the past year, however, there has been a clear year-over-year increase in the use of free domains. By leveraging these no-cost options, threat actors can accelerate operations, bypass the need to purchase domains or compromise existing sites, and launch phishing campaigns with greater speed and efficiency.
Additional Resources:
