One of our Digital Risk Protection service customers, LastPass, is committed to monitoring the cyber threat environment to keep our customers as secure as possible. To highlight this commitment, we want to call attention to recent joint efforts to disrupt a phishing campaign targeting LastPass customers and associates that began two weeks ago. We are sharing this with you not because it is a new or unique threat, but to underscore the efforts we are taking to disrupt this threat and ones like it. On the morning of September 13th, LastPass customers began reporting a pervasive and convincing phishing campaign. The campaign had global reach and targeted a variety of sectors, including 87 of our own employees. The first reports we saw coming in from our customers arrived at approximately 9:34 am ET. The email originated from a sender address called “[email protected][.]th” and was associated with a domain that had not previously been linked to malicious activity targeting LastPass prior to that morning. The email also included a link to a phishing page hosted on subdomains of “customer-lastpass[.]su.” The campaign was widespread yet targeted enough to draw attention from the Information Security community, including a blog post calling out the emails from Malwarebytes published the following day. In an effort to protect our customers, this campaign became an immediate priority for LastPass and our domain monitoring and takedown vendor, Fortra’s PhishLabs, as soon as it was detected. Fig. 1: Example of Redacted Phishing Email from September 13, 2023 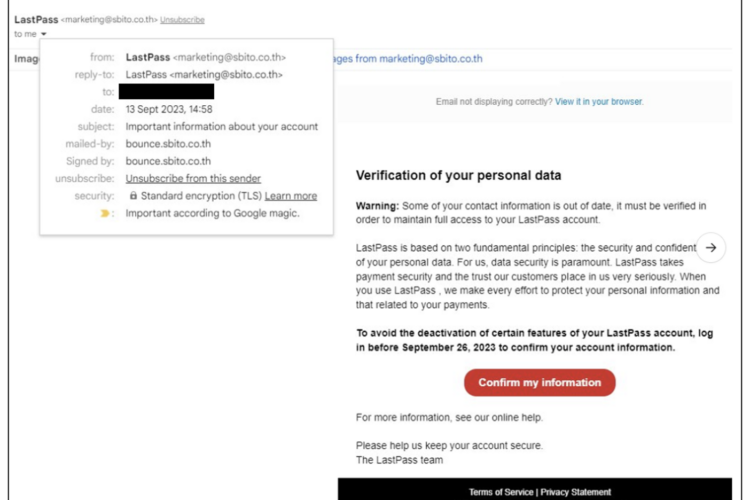 Fortunately, LastPass’ Threat Intelligence, Mitigation, and Escalations team frequently works with PhishLabs to protect our customers from phishing campaigns exactly like this one by actively monitoring our domains. In fact, by the time the first reports started coming in from our customers, a takedown request to each respective service provider for the two suspicious domains was already under way as the sites had been detected at approximately 8:55 am ET that morning. Furthermore, the “lastpass[.]su” site had been overtly marked for monitoring since September 3rd, the day after it was registered. As soon as the site went active, LastPass, in conjunction with PhishLabs, was able to begin the mitigation process immediately. Additionally, we were able to pivot off the PDNS data to proactively identify other domains that may be leveraged for future phishing campaigns and flag them for monitoring as well. Unfortunately, the threat actors materialized again on September 19th when a similar subdomain for the credential phishing site was registered, and several new domains for the phishing emails were leveraged. Again, PhishLabs was able to identify these sites as soon as they went active, immediate takedown of the phishing subdomains (all falling under the domain “last-pass[.]su”) within just 16 hours from the start of the campaign’s second wave! While the speed of takedown is often outside the control of the targeted company and can vary based on the malicious domain’s host, LastPass is proud that we were able to work with PhishLabs to get quick and seamless confirmation of site disruptions within 48 hours or less, thereby minimizing and containing the potential threat posed to our customers. Furthermore, PhishLabs shared these sites with major browsersvia Fraudcast, helping to fortify our customers’ security further with another layer of protection. Rest assured, LastPass is committed to continuing to proactively protect our users in partnership with this trusted vendor. For more information on steps you can take to help protect yourself against phishing emails, please see this blog post from LastPass' Chief Secure Technology Officer, Christofer Hoff. You can also find more technical details on our legitimate email domains here. Lastly, for LastPass customers who want to report a suspicious email, please forward any questionable emails to [email protected] and our team will take the appropriate action from there. Courtesy of the LastPass Blog and written by Mike Kosak, Senior Principal Intelligence Analyst at LastPass.
Fortunately, LastPass’ Threat Intelligence, Mitigation, and Escalations team frequently works with PhishLabs to protect our customers from phishing campaigns exactly like this one by actively monitoring our domains. In fact, by the time the first reports started coming in from our customers, a takedown request to each respective service provider for the two suspicious domains was already under way as the sites had been detected at approximately 8:55 am ET that morning. Furthermore, the “lastpass[.]su” site had been overtly marked for monitoring since September 3rd, the day after it was registered. As soon as the site went active, LastPass, in conjunction with PhishLabs, was able to begin the mitigation process immediately. Additionally, we were able to pivot off the PDNS data to proactively identify other domains that may be leveraged for future phishing campaigns and flag them for monitoring as well. Unfortunately, the threat actors materialized again on September 19th when a similar subdomain for the credential phishing site was registered, and several new domains for the phishing emails were leveraged. Again, PhishLabs was able to identify these sites as soon as they went active, immediate takedown of the phishing subdomains (all falling under the domain “last-pass[.]su”) within just 16 hours from the start of the campaign’s second wave! While the speed of takedown is often outside the control of the targeted company and can vary based on the malicious domain’s host, LastPass is proud that we were able to work with PhishLabs to get quick and seamless confirmation of site disruptions within 48 hours or less, thereby minimizing and containing the potential threat posed to our customers. Furthermore, PhishLabs shared these sites with major browsersvia Fraudcast, helping to fortify our customers’ security further with another layer of protection. Rest assured, LastPass is committed to continuing to proactively protect our users in partnership with this trusted vendor. For more information on steps you can take to help protect yourself against phishing emails, please see this blog post from LastPass' Chief Secure Technology Officer, Christofer Hoff. You can also find more technical details on our legitimate email domains here. Lastly, for LastPass customers who want to report a suspicious email, please forward any questionable emails to [email protected] and our team will take the appropriate action from there. Courtesy of the LastPass Blog and written by Mike Kosak, Senior Principal Intelligence Analyst at LastPass.
LastPass and Fortra’s PhishLabs Work Together to Protect Customers From Phishing Scams
Posted on September 26, 2023